by Alex Nadalin
How to get valid SSL certificates for local development
A few weeks ago I bumped into mkcert, a tool written by Filippo. He is the same guy behind the popular heartbleed test tool.
The tool in question answers one simple need:
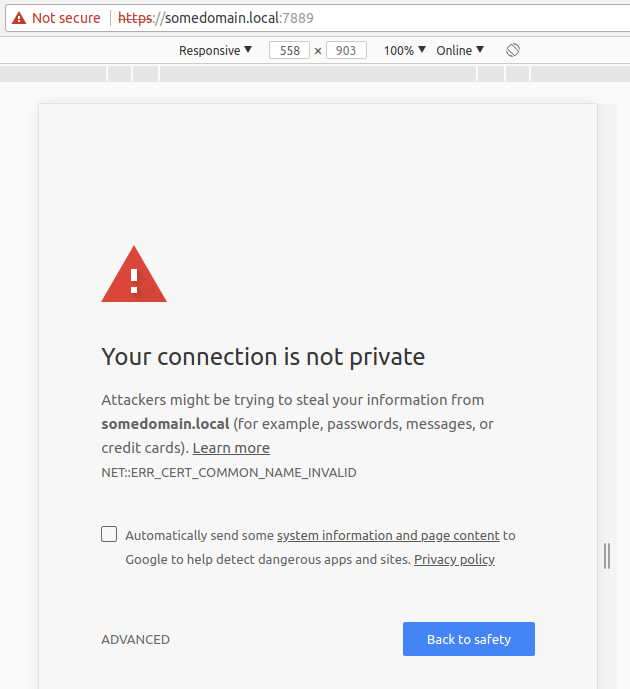
By creating a local root CA file that gets installed in your system, it makes all certificates issued by mkcert trusted.
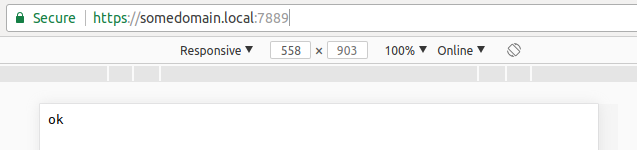
After downloading the latest release from GitHub, you can simply “install” it by running mkcert -install. Once that is done, you can create your first, trusted (by your own system) certificate:
$ mkcert somedomain.local
Using the local CA at "/home/alex/.local/share/mkcert" ✨
Created a new certificate valid for the following names ?
- "somedomain.local"
The certificate is at "./somedomain.local.pem" and the key at "./somedomain.local-key.pem" ✅For example, here’s how it would look like if you had to boot a Node server with SSL support:
const fs = require('fs')
const options = {
key: fs.readFileSync(__dirname + '/somedomain.local-key.pem'),
cert: fs.readFileSync(__dirname + '/somedomain.local.pem')
};
require('https').createServer(options, (req, res) => {
res.writeHead(200)
res.end(`Got SSL?`)
}).listen(443)Pretty neat, eh?
What mkcert does is to simply add another CA file in your system.(I guess under /etc/ssl/certs/ca-certificates.crt, but I’m not entirely sure). Browsers consider these certificates trusted — a nice workaround to trick any HTTP client.
That’s it for today! Adios!
Originally published at odino.org (1st September 2018).
You can follow me on Twitter — rants are welcome! ?