Vulnerabilities can exist in all products. The larger your software grows, the greater the potential for vulnerabilities.
Vulnerabilities create opportunities for exploits which could ruin both the user experience and the product itself.
Additionally, in today’s fast-paced world, the rate of vulnerabilities increase as companies demand rapid development (or update) processes. And exploiters are everywhere, looking to take advantage of them.
That is why it’s important to check for vulnerabilities as early as possible in your applications. This can help you make sure that the final product is secure, and save you a lot of time in the long-run.
In this article, we'll look at six tools that will help you check for vulnerabilities in Node.js.
Vulnerabilities in Node.js
Security vulnerabilities are very common in Node.js. As developers, we keep using open source tools because we do not want to reinvent the wheel. This makes development easier and faster for us, but at the same time it introduces possible vulnerabilities to our applications.
The best we can do for ourselves is to continually verify the packages we use because the more dependencies we use, the more room there is for more vulnerabilities.
Manually checking dependencies can be stressful and can increase development time. And going online to find out how vulnerable a package is before installing it can be time-consuming, especially for an application with many dependencies.
This is why we need automated tools to help us with this process.
Tools for Checking for Vulnerabilities in Node.js
1. Retire.js
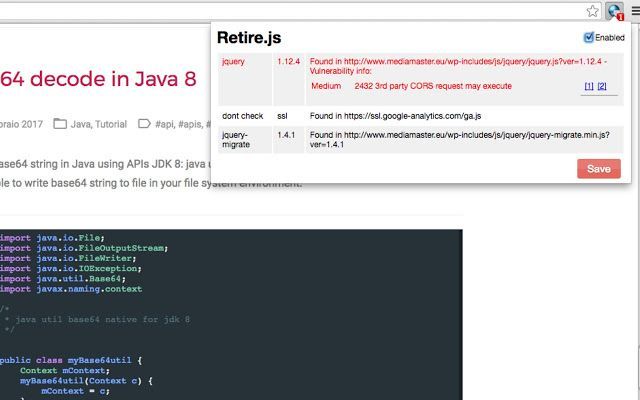
Retire.js helps developers detect versions of libraries or modules with known vulnerabilities in Node.js applications.
It can be used in four ways:
- A command line scanner to scan a Node.js application.
- A Grunt plugin (
grunt-retire), used to scan Grunt enabled applications. - Browser extensions (Chrome and Firefox). These scan visited sites for references to insecure libraries and puts warnings in the developer console.
- Burp and OWASP Zap Plugin, used for penetration testing.
2. WhiteSource Renovate
WhiteSource Renovate is a multi-platform and multi-language open source tool by WhiteSource which performs automated dependency updates in software updates.
It offers features such as automated pull requests when dependencies need updating, supports numerous platforms, easy modification, and lots more. All changelogs and commit histories are included in each update of the application.
It can be used in various ways such as:
- A command-line tool for automating the process of updating dependencies to invulnerable dependencies.
- Github Application for performing the automation process on GitHub repositories
- GitLab Applications for integrating the automation process on GitLab repositories
WhiteSource Renovate also has an on-premises solution that extends the CLI tool to add more features thereby making your applications more efficient.
3.OWASP Dependency-Check

Dependency-Check is a Software Composition Analysis (CPA) tool used for managing and securing open source software.
Developers can use it to identify publicly disclosed vulnerabilities in Node.js, Python, and Ruby.
The tool inspects the project's dependencies to gather information about every dependency. It determines if there is a Common Platform Enumeration (CPE) identifier for a given dependency, and if found, it generates a list of associated Common Vulnerability and Exposure (CVE) entries.
Dependency-Check can be used as a CLI tool, a Maven plugin, an Ant Task and a Jenkins plugin.
4. OSS INDEX

The OSS Index allows developers to search for millions of components to discover the vulnerable and invulnerable ones. This assures developers that the components they plan on using are well protected.
They also provide developers with various tools and plugins for programming languages like JavaScript.
These allow them to scan projects for open source vulnerabilites as well as integrate security into the development process of the project.
5. Acutinex

Acunetix is a web application security scanner that allows developers to identify vulnerabilites in Node.js applications and enables them to fix the vulnerabilities to prevent hackers. It comes with a 14 day trial for testing applications.
The benefits of using Acunetix to scan web applications are numerous. Some of them are:
- Tests for over 3000 vulnerabilities
- Analysis of external links for malwares and phishing URLs
- Scanning of HTML, JavaScript, single page applications, and web services
6. NODEJSSCAN
NodeJsScan is a static security code scanner. It is used for discovering security vulnerabilities in web applications, web services and serverless applications.
It can be used as a CLI tool (which allows NodeJsScan to be integrated with CI/CD pipelines), a web based application, and also has a Python API.
Conclusion
Packages, libraries and components for Node.js applications are released regularly, and the fact that they are open source leaves room for vulnerabilities. This is true whether you're working with Node.js, Apache Struts vulnerabilities, or any other open source framework.
Developers need to watch out for vulnerabilities in new releases of packages and know when it's necessary to update packages. The tools above can ease the process of creating efficient and reliable products.

