What is a cybersecurity tabletop exercise (TTX)?
Cybersecurity breaches are resulting in an increasing number of losses ($4.2 million in 2021). So it's important to do as much as possible to prepare and train before experiencing a potential incident yourself.
A cybersecurity tabletop exercise (TTX) is one of the best methods that you can use to exercise your incident response plan – short of experiencing a real incident.
In short, the TTX is designed to help assess the preparedness of your company to handle an incident. The exercise should reinforce a culture of learning and training – there are no failures during an exercise, just opportunities to iterate and refine processes.
Main Benefits of a Cybersecurity Tabletop Exercise
- Develop a better understanding of the impact of a breach in a cost-efficient manner
- Maintain a positive reputation through transparency and communication
- Solidify roles and responsibilities and explore decision making processes
- Assess the capabilities of your existing resources
- Identify and address deficiencies in planning
What Makes a Tabletop Exercise Effective?
Given that this exercise is a critical component of testing how prepared your company is to handle an incident, it is important to go into the exercise with clear objectives.
The following components will help ensure that your exercise is as efficient as possible.
- Have an incident response plan. Without an incident response plan, the exercise will likely be extremely chaotic, as you will be figuring out roles and responsibilities on the fly, without defined processes to follow. The goal is to test your plan, not create a new one!
- Perform risk analysis ahead of time. Unless the goal of the tabletop is to reinforce that a formal risk analysis is needed, it is important to have performed at least a cursory analysis to understand the key risks to the business. Why do they care about funding the security program? What do they care about protecting? What is the potential harm to the company if an adverse event occurs?
- Have clear objectives. Think of what you want to accomplish with this exercise – what outcomes are you looking for? You may have numerous scenarios testing various components of the business you want to run, but you might also have limited time with senior executives. Make sure you don't throw too many objectives into the exercise. Keep focused. Develop the scenario only after you've decided what you want to get out of the exercise.
- Get stakeholder/executive buy-in. To be successful, the exercise needs to be performed willingly with the intent to learn, not just to tick a checkbox for compliance. Executive leadership needs to be involved and willing to learn from the results, transforming the lessons learned into actionable changes within the company where appropriate.
- Strong facilitator. The facilitator needs to keep everyone on track, ensuring that all important points during each inject are covered. While open discussion is great, the facilitator needs to ensure that the conversation stays on point rather than going down various rabbit holes and tangents.
How Does a TTX Generally Flow?
The general flow of a cybersecurity tabletop exercise will walk participants through the process of an incident from inception until conclusion. There will be a focus on exploring the various decision points that come up during the process, ensuring that all participants understand who the key decision makers and stakeholders are in an incident.
The below diagram illustrates the various key components of the exercise itself, from planning to execution:
Exercise Flow:
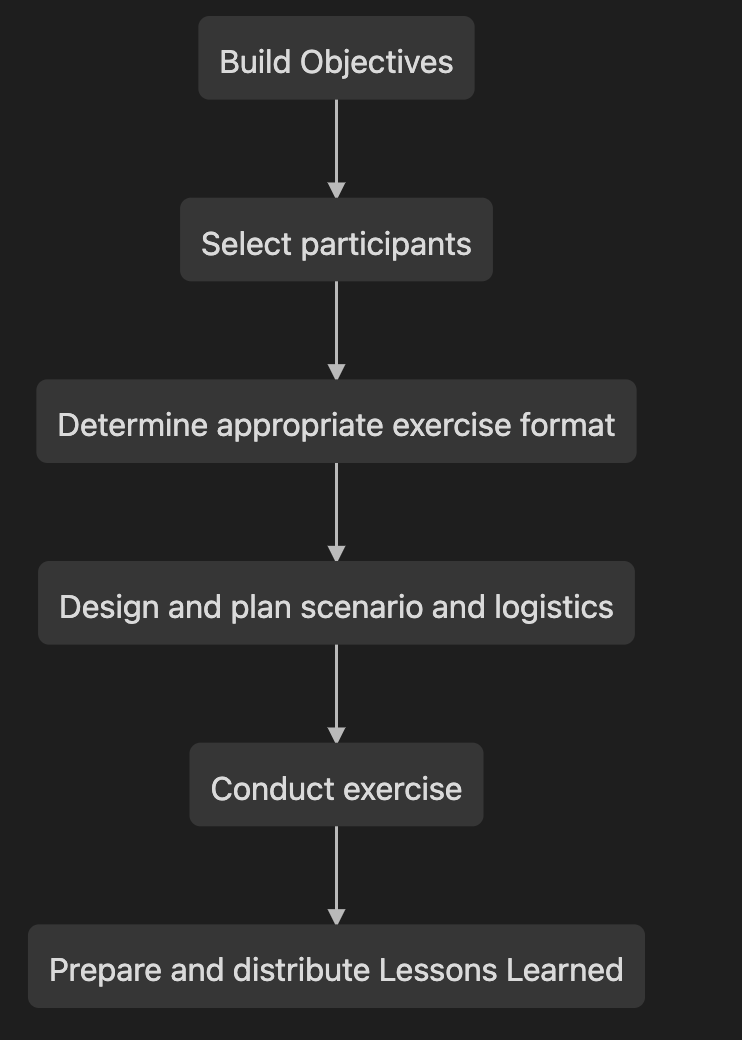
Let's go through each element in this flow:
Building valuable objectives
It is important to identify key learning opportunities that stakeholders can take from the exercise (for example, "Does leadership know who is responsible for deciding whether to halt trading activity of our company's stock on the exchange?" or "Who makes the call to unplug a critical, revenue generating system.").
Once these objectives are identified, it will be possible to inform the scenario's design. Example objectives could include:
- Test efficacy of out of band communication processes
- Assess training gaps
- Determine inconsistencies between the incident response plan and implemented processes
- Evaluate current decision making processes
Who needs to be involved in the exercise?
Participants should be actively involved in the exercise, taking part in the discussion and decision making process. It is important to involve a variety of stakeholders as appropriate for the scenario.
Typically, representatives of the following groups will be present:
- C-suite: CEO, CFO, COO, CIO, CTO, and so on.
- Human Resources
- Legal/CLO
- Compliance and Privacy
- Business unit leadership
A facilitator is an internal or external resource who will walk participants through the scenario, the various injects, and control the flow of conversation.
It is critical to keep everyone focused on the scenario and to ensure that participants don't fall down rabbit holes poking holes in the scenario or addressing unnecessary elements.
Note: Consider having a third party, such as an incident response forensics firm, take on this role as a primary or supporting facilitator. They can provide broader background information on attacks they have observed and answer macro-level questions posed by executives.
Outside agencies can include law enforcement, outside counsel, security forensics firms, or regulators.
Finally, you'll need a scribe to take notes of participant's reactions and decisions, lessons learned, what went well, and what did not.
What types of exercise formats are there?
There are generally two main forms an exercise can take: a discussion or live-fire/wargame. There is no right or wrong format. The type of exercise selected should match the participants and desired outcomes and objectives of the exercise itself.
A live-fire exercise, sometimes known as a wargame, is when an incident is simulated in real-time, requiring swift action by teams that may or may not be aware the event is taking place.
This type of exercise is typically performed for the incident response team and the "boots on the ground" responders - for example, network, firewall, application, and database teams.
This exercise is designed to measure how efficiently the company's people, process, and technologies will operate in an environment as close to a real incident as possible.
A discussion-based exercise will typically feature a presentation where general, high-level information is provided to the participants, who are typically a cross section of senior leaders across various business functions in the company.
Periodically, an inject will be used throughout the presentation. These are often meant to provide some new information or other type of curveball to the participants. Examples of an inject can be an internal memo, a media report, a phone call, or even a slide with further information.
You should perform the following after each inject:
- Assess situation
- Revalidate assumptions
- Identify security and organizational implications
- Develop a course of action
- Review resources
- Develop recommendations
- Take actions to implement changes
- Outputs – document the discussion, lessons learned, and so on.
How do I design a relevant scenario?
When building your scenarios, here are some example questions you can use to help structure your exercise:
- Who is the threat actor?
- What is the threat actor's intent?
- What threats are occurring against your industry? This can inform your scenario or various decision points.
- How will the team handle and respond to the attack?
- What external entities should be involved?
- Will employees, customers, or regulators need to be informed?
Make sure that each slide that conveys information has a timestamp to let the participants know how much time has elapsed between events. The scenario should not include too many slides or injects – typically 2-4 injects and some for of media content should be sufficient, alongside the general information slides.
Logistics
Discussion-based exercises work best when performed for approximately 3-4 hours, with the majority of participants physically located in the same room.
Prior to the exercise, the facilitator should have a list of key topics that should be explored for each slide and ensure that these are discussed throughout the exercise. Make sure to have coffee and snacks too 😊.
The rules
Make sure everyone understands the "rules" of the event. Suspend disbelief, no enemies, work together.
Provide rules both several days before as well as during the event. Include the IR plan. Do not fight the scenario!
How to leverage the "hot wash" and lessons learned
A short review (the "hot wash") should occur immediately after the exercise (optionally with or without any third parties that may have been present) to review what went well and what could be improved while information is still fresh.
Close out the session by asking each participant to name one takeaway they have from the event.
Over the next couple of weeks, review all notes and observations from the exercise and compile a list of lessons learned. Distill these into several themes that you can share with leadership, after which you can construct a plan to address these items.
Some example lessons can include:
- Create a "pocket runbook" so that individuals "on the ground" have a clear and concise set of instructions on what to do / not do during an incident
- Establish authority for the incident commander
- Implement an asset inventory system that takes into account systems, applications, critical suppliers, and critical personnel
- Onboard an alternate communication system to allow for communicating with staff if core systems such as email and chat are inaccessible
- Retain a crisis PR firm on retainer in the event of an incident and ensure executives undergo media communication training
Conclusion
Well, that was a LOT of information. Hopefully you've learned quite a bit about how a tabletop exercise works, and how to build a valuable exercise.
Here are some key takeaways to help ensure that you are building an effective tabletop:
- Establish clear objectives – what is the desired outcome after running this exercise? Use that to identify valuable objectives to achieve throughout the exercise.
- Be engaging – slides can be dull. Never just read off the slides. Try to add some form of multimedia (like a fake news report about leaked data causing stock price to decline, a phone call from a journalist, and so on.) to break up the flow.
- Action the lessons learned – Once you have consensus on the lessons learned, put together a roadmap and project plan for each item, along with an owner. The goal of the exercise is to produce actionable tasks that will improve the readiness of the company when responding to an incident while also mitigating the impact of any future incidents.
Last, if you are looking for inspiration, be sure to check out CISA's Tabletop Exercise Packages for some ready to go templates!

