By Konark Modi
I asked my wife if it is alright if her Date of Birth is known to a stranger. Only if they send me a birthday gift, she joked. What about your passport number? She lowered the book she was reading. I now had her attention.
Now imagine this, I said “You try to check-in for your flight online, and see the error message — This booking does not exist. You try again, this surely is a mistake. Nope, still the same error message. The call center person repeats the same words. This has to be a mistake! You check your email, and there it is — staring back at you — email confirmation of cancellation. But you are sure you didn’t do it.” Whodunnit?
This is not a far-fetched scenario from a Sci-fi book, this really happened.
An organisation with a primary Digital Product that lacks even the basic data security practices is living in a utopian world where people leave their safe open and never expect a burglar to walk in.
In the wake of full disclosure, sometime last year while booking travel for my family, I stumbled across a few data-security practices that, as a Data Security advocate, made me extremely worried. When I voiced my concerns to Emirates team, this conversation took place -
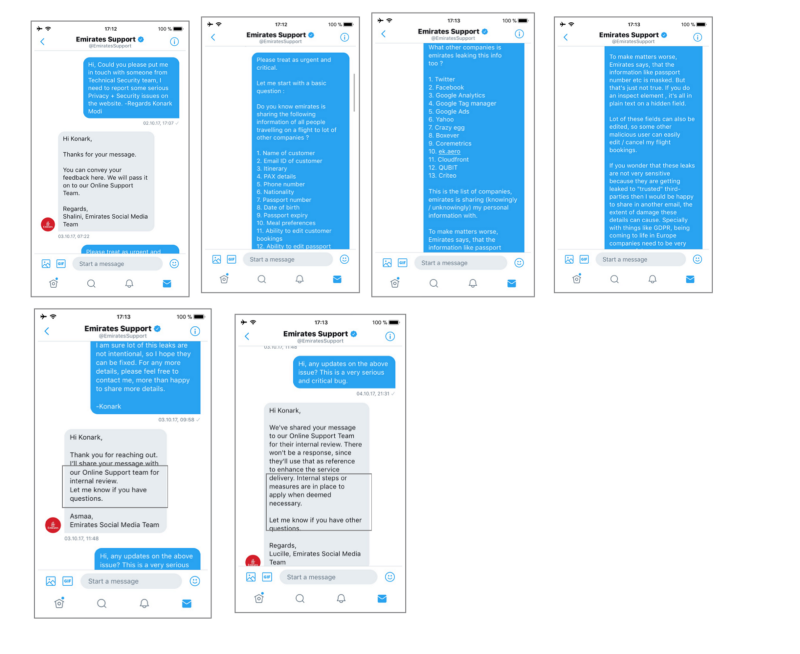
For a layman, when you book your flight through Emirates, Domestic or International, there are approximately 300 data points related to your booking.
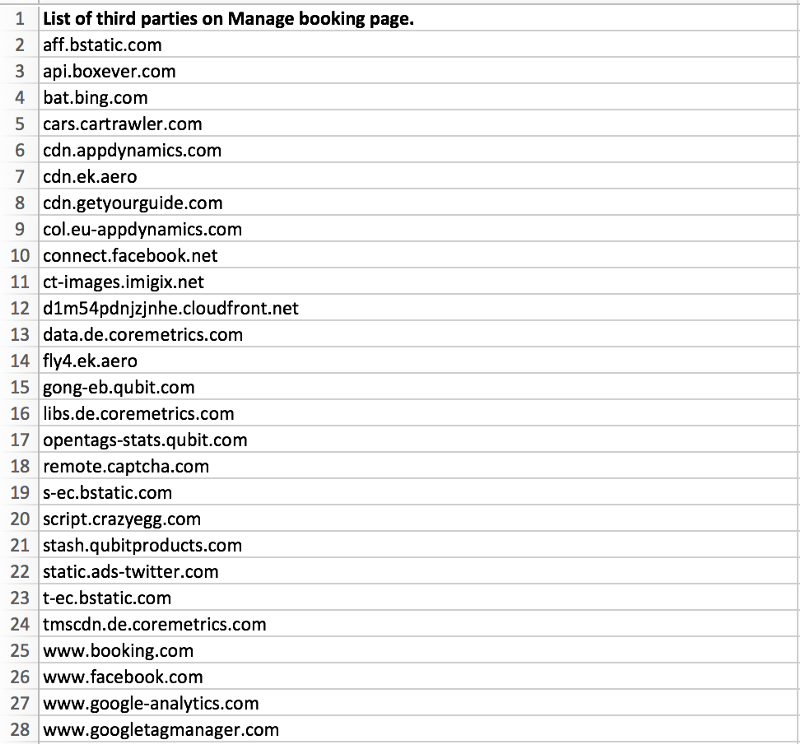
The moment you click on manage preferences to select a seat or meal for your trip or to Check-in to your flight, your Booking ID and Last name is passed on to approximately 14 different third-party trackers like Crazy egg, Boxever, Coremetrics, Google, and Facebook among others.
Details
After I completed the booking on Emirates, I received an e-mail confirmation titled: Booking Confirmation — Booking Number.

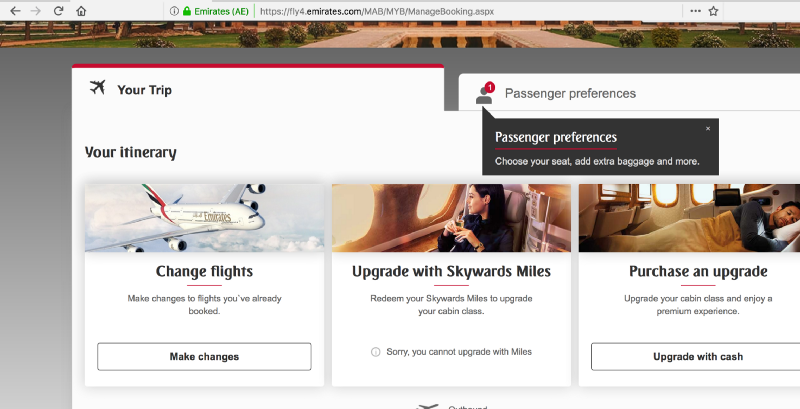
The body of the email contained Manage booking. I proceeded to select seats and meal by clicking on the Manage Booking button and reached the Manage Preference page. This was pretty straightforward.

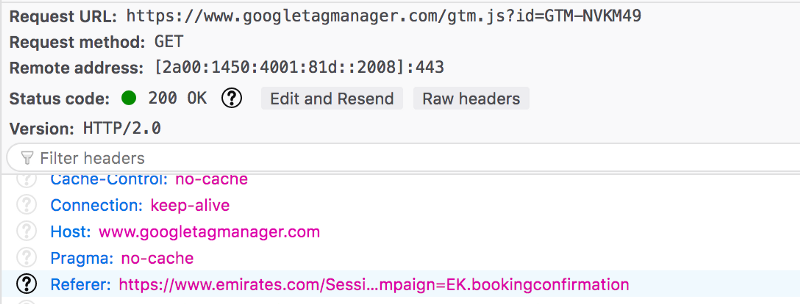
While as a user, I saw the normal behaviour of clicking a link and reaching the landing page “Manage Preferences”, in the background a redirection chain took place.
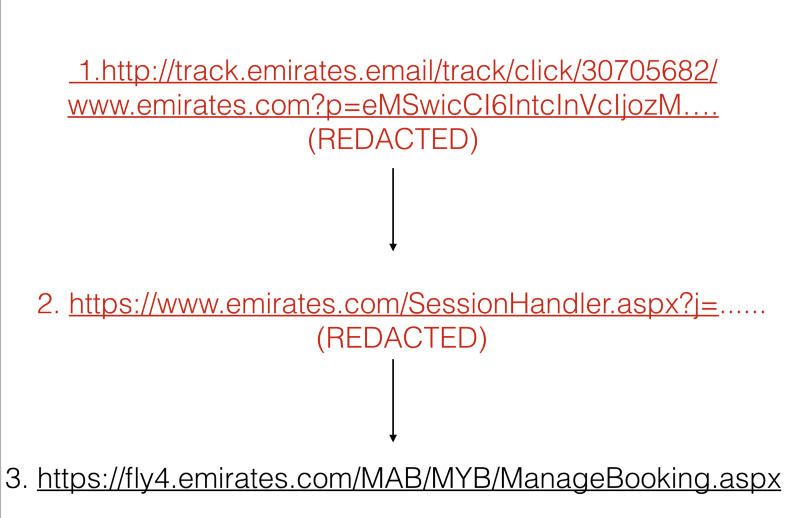
While Manage Booking link was supposed to be exclusive to me (the user and the website), this link was also shared with numerous third party trackers implemented by Emirates on their webpages.
The cherry on the cake was the HTTP link that leads to the Manage Preferences page. The insecureness of HTTP has been talked about over and over again, especially when it comes to maintaining the authenticity of the content and protection against interlopers. But in short, HTTP links are a Data Privacy nightmare. So, not only was Emirates passing on user information to the self-implemented third party trackers, but also allowing network adversaries to have access to the supposedly “Private” page.
What kind of information can third-parties access?
Links mentioned in (1) and (2) are currently being sent to the third-parties.
Following fields take home the URL, which gives access to booking details.


dr used by Google Analytics.
Anyone who has access to these links can not only read but also edit the information that I as a user can.
For example, they can now -
- Change or Cancel flight
- Change seat or meal preference
- Add more products to the booking
- Change or add Passport Information
- Change or add Frequent Flyer Information, etc.
Exhibit of editable personal information on this page:
a. Full Name:
b. Skywards number

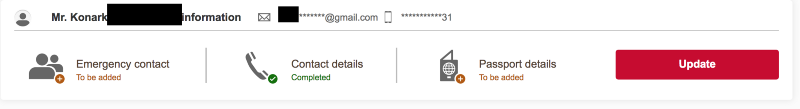
c. Email ID / Telephone number:
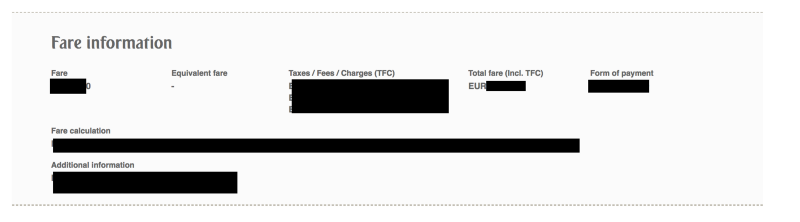
d. Amount Paid, fare breakup.
e. Passport details, Nationality, Date of birth, Gender
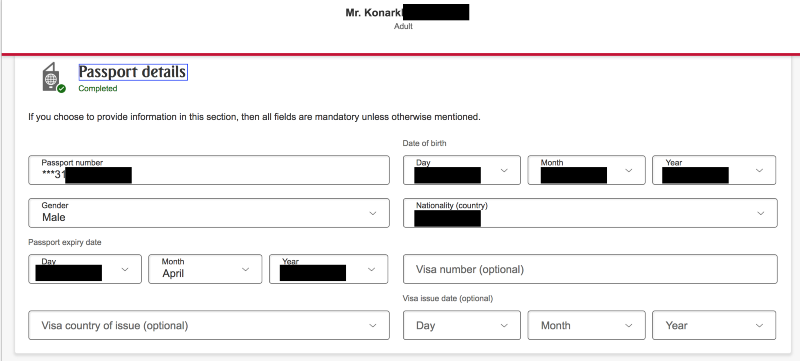
Note: In October 2017, fields such as Passport Number, Email Id and Telephone number were shown to be masked on the User Interface but were not obfuscated in source code. The web app has been revamped since then and these fields are now obfuscated.
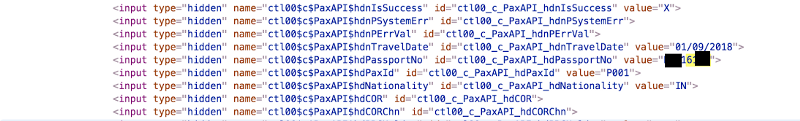
I decided to take a peek into the mobile app and see if the past catches up with the present, and lo and behold there it was in its full glory — Passport Number, Email ID and Telephone number in plain text. What was obfuscated on the web app was easy to access on the mobile app.
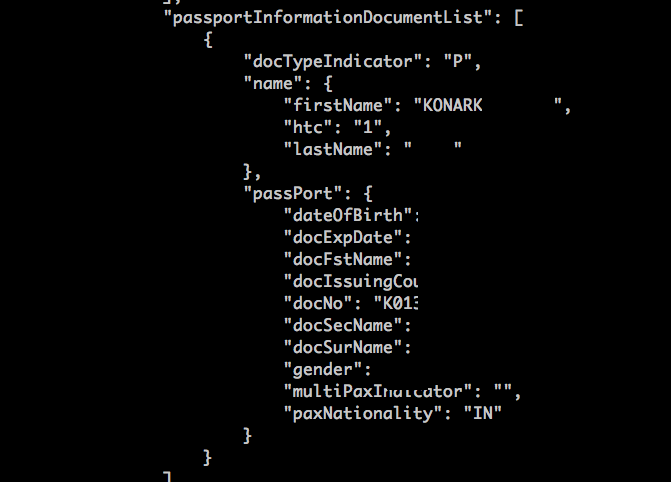
Now, what is wrong with this?
This issue is not only limited to Emirates, a lot of airlines like Lufthansa, KLM (last checked on October 2017) suffer from the same issues.
Every website uses third party trackers for improving their product and provide better web-usage experience. Data leaks are often considered collateral-damage and sometimes not even considered at all while implementation of such trackers.
Most of these third-parties are present on a lot of other websites and use long term identifiers like cookies etc to track users across domains. Now because one of the websites, in this case Emirates, leaks private information, these companies now potentially can not only link the user’s activity across web, but also identify who the user is.
The questions that need answering by Emirates (and others) are -
- Why was my booking information passed on to these third parties without my explicit consent.
- Why do these third parties need to receive this information?
- Is Emirates even aware that sensitive user information is being leaked to these third parties?
- Who are these third parties?
- What are they doing with user information?
Reporting it to Emirates
In the wake of responsible behaviour, on discovering these serious security flaws that violate user-data privacy, I decided to flag them to Emirates through Twitter DM in October 2017. Please note that I could not find a dedicated channel for reporting security bugs on Emirates website.
The Social Media Team immediately responded to my Twitter DM with a canned response but I was not ready to give up hope. I also wrote an email to the Product Manager highlighting the security flaws. I was met with a deafening silence.
As of today (2018–03–03) lot of these issues still persists.
This is a serious violation of privacy, there is no point during the whole booking process, where I agreed upon sharing any of this personal information with any of these websites.
The privacy policy of Emirates itself is not very clear. It does mention some of the of these services, but not all or the what data being shared with them.
Can I not opt-out?
Not an option. Unfortunately, I could not find a way to opt-out of this system provided by Emirates. I finally had to fall back on using privacy preserving browser extensions.
Can this not be fixed by Emirates?
As a Software Engineer who has worked for the some of the largest eCommerce companies, I understand the need to use third party services for optimising and enhancing not only the Digital Product but also how user interacts with the product.
It is not the usage of third party services that is of concern here in this case but the implementation of these services. Emirates has the control of their website and what the website shares with third party services. It is this control that needs to be exercised to limit the leakage of User information.
It is not a mammoth task, it is just a matter of commitment to preserving the basic right to privacy.
For example:
- Private pages should have noindex meta tags.
- Limit the presence of third-party services on private pages.
- Referrer-Policy on pages with sensitive data.
- Implement CSP and SRI. Even with a huge footprint of third-party services CSP, SRI are not enabled on Emirates.com
- User needs to be informed when sensitive information like passport, contact details etc. is updated, edited, or deleted.
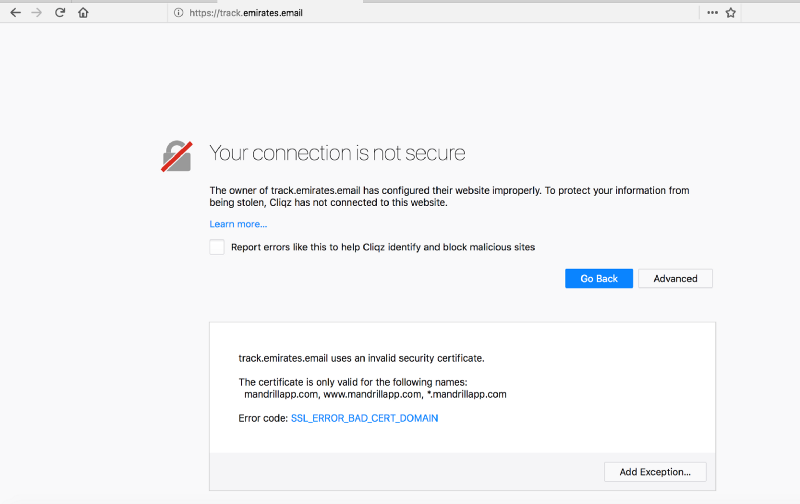
- Domain for sending e-mails : track.emirates.email, should have a valid certificate. https://track.emirates.email/
If you are interested in reading more about the presence of trackers on your favourite websites, I highly recommend checking out WhoTracksMe.
Updates:
- March 6th, 2018:
Emirates responded with a standard statement.
Excerpt: “The depiction in Mr Modi’s article as to what data is being shared, or customer choice in ‘opting out’ is inaccurate.”
Here is my response: Privacy leaks round-trip: Emirates.com in denial
Happy Hacking!
Thanks for reading and sharing ! :)
If you liked this story, feel free to ??? a few times (Up to 50 times. Seriously).
_Credits: Special thanks to Remi ,Pallavi for reviewing the post._