In this article, we will look at OWASP and the top 10 web application vulnerabilities they've identified. This is a useful topic for both web app pen-testers and bug bounty hunters.
What do web app pen-testers and bug bounty hunters have in common? They are both hunting for bugs, but the latter makes more money ;)
Web application security is a broad topic. There are many ways a web app can be exploited. This can be a challenge for security engineers, especially if they are getting started in their careers.
OWASP, short for Open Web Application Security Project, is an organization dedicated to improving software security. OWASP provides tools and resources for security engineers to help make their applications more secure.
OWASP’s most important contribution to cybersecurity is the OWASP Top 10 Vulnerabilities list. This list contains the 10 most critical web application security risks that should be monitored and prevented.
Knowing these 10 security risks will help you reduce the risk of attacks against your company’s web assets. It also helps bug-bounty hunters get an idea of what to look for while auditing web applications.
Let’s look at each OWASP vulnerability in detail.
Injection Attacks

An injection is a type of vulnerability in which an attacker injects malicious code into a web app. Injections can lead to unauthorized access to sensitive data, loss of data, or even complete system compromise.
An example of an injection attack is SQL Injection. This is where an attacker injects malicious SQL code into a web application’s SQL query. This is performed when inputs into the web app are not properly checked. If successful, the malicious code gets executed by the database server.
Another example is Command Injection. Here, an attacker injects malicious shell commands into a web application. This can lead to devastating consequences including a complete system takeover.
To prevent injection attacks, check and sanitize all user input. Sanitizing is the removal of harmful or malicious data entered into the input box.
For example, if a user enters any characters other than an alphanumeric string, you can remove them before you send it to the backend and double check it in the backend as well. This helps to eliminate harmful or malicious content and protects against security threats.
Also, always use ready-made SQL queries in the backend instead of generating SQL queries on the fly. Additionally, keep all software and libraries up to date with the latest security patches.
Insufficient Monitoring and Logging

Insufficient monitoring and logging refers to the lack of proper monitoring and logging for a web server or database. This makes detection and response to security incidents difficult.
For example, if a system does not have proper logging in place, it will be difficult to detect when an attacker tries to compromise the system. Without real-time monitoring, it will be difficult to detect security incidents on time.
To address insufficient monitoring and logging, you should implement robust monitoring systems that capture a wide range of events. This includes logging access to sensitive data, network traffic, and system logs.
Include monitoring for network devices as well by using services like Snort. Snort is a free open source network intrusion detection and prevention system. Also, review and analyze log data periodically to identify trends and potential security incidents.
Broken Authentication

Broken authentication refers to weaknesses in the authentication process. This includes issues such as weak or easily guessable passwords, lack of proper password management, and using vulnerable authentication mechanisms.
For example, an attacker can exploit a system that allows weak passwords by guessing common passwords from a list like rockyou.txt. They can also use brute-force tools like Hydra and other password-cracking tools to break encryption if a weak algorithm is used.
Another example is using easily guessable security questions, such as “What is your mother’s maiden name?”. An attacker who has done basic research on the target can easily answer these questions.
To prevent broken authentication, enable strong authentication mechanisms, such as multi-factor authentication (MFA). Enforce password recycling policies that require users to change passwords periodically.
Sensitive Data Exposure

Sensitive Data Exposure refers to storing and transmitting sensitive information without proper security. This includes passwords, credit card numbers, and personally identifiable information (PII).
The most common reason for this is lack of encryption. Encryption is the process of encoding information. This process converts the original text, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can decipher a ciphertext back to plaintext and access the original information.
For example, if you have a database where you store passwords, you have to use some type of an encryption to protect your customer's passwords. If you store them as plaintext, you will be putting your customers under risk if you expose their passwords.
Without protective methods such as encryption, sensitive data exposure can result in the data being intercepted, stolen, or manipulated by an attacker. To mitigate this risk, always encrypt sensitive information when stored and transmitted.
Always store encrypted passwords instead of plain-text passwords. Enable access controls to ensure that only authorized personnel can access sensitive data.
XML External Entities

XML External Entities is a vulnerability that affects XML processors. This happens when they parse XML input from a user without proper validation.
This vulnerability allows an attacker to inject malicious XML code into an XML document. This can lead to the exposure of sensitive information, denial of service, and even remote code execution.
To prevent XXE attacks, applications should validate and sanitize XML input. Disable XML external entity and DTD processing by default.
Whenever possible, use a less complex data format, such as JSON. Most APIs are now JSON-based, so it would be a win-win to move away from XML to JSON.
Broken Access Control

While authentication tells us whether a user can access a system, access control tells us who can access a specific resource in a system.
Broken Access Control happens when an application does not restrict access to sensitive resources. This includes files, database records, or even product features that should be limited to select users.
Broken access control can lead to unauthorized users being able to view, change, or delete sensitive data. To reduce this risk, enable strong access control policies like role-based access for users, admins, and others.
Assign access rights based on the principle of least privilege. This means users should only have the least access required to perform their job. Regular security audits and assessments will help identify these access control vulnerabilities.
Security Misconfiguration
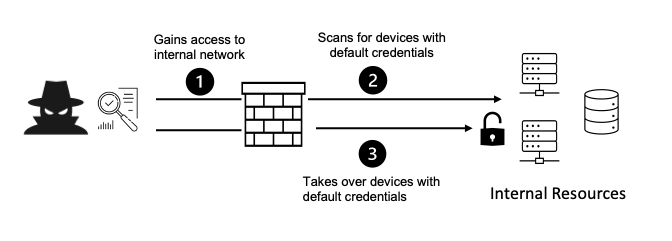
Security Misconfiguration arises when an application is not configured properly. This will result in the exposure of critical information, such as error messages or system details.
For example, if you don't change the default settings of your backend, it can expose the error message to the user instead of gracefully handling it. You can often see this in PHP sites that print an error in the browser instead of a 500 message.
To reduce this risk, hide all debug and error messages from your production application. Apply appropriate security controls and patches as needed, on time. Finally, perform regular security scans and assessments to make sure there is no misconfiguration in your applications.
Cross-Site Scripting (XSS)

Cross-Site Scripting (XSS) is a common security issue in websites. If not handled, an attacker can inject malicious scripts into a web page. This script is then executed by the victim’s web browser.
Consider a website that allows users to post comments. An attacker could craft a comment that contains malicious JavaScript code and add it as a comment. If the input is not sanitized by the website, this code will execute on every user who opens the comments page.
XSS attacks can steal data such as login details, perform unauthorized actions on behalf of the victim, or even redirect the victim to a malicious website. To prevent XSS attacks, always sanitize user-generated content and double-check input data on the server side.
Insecure Deserialization
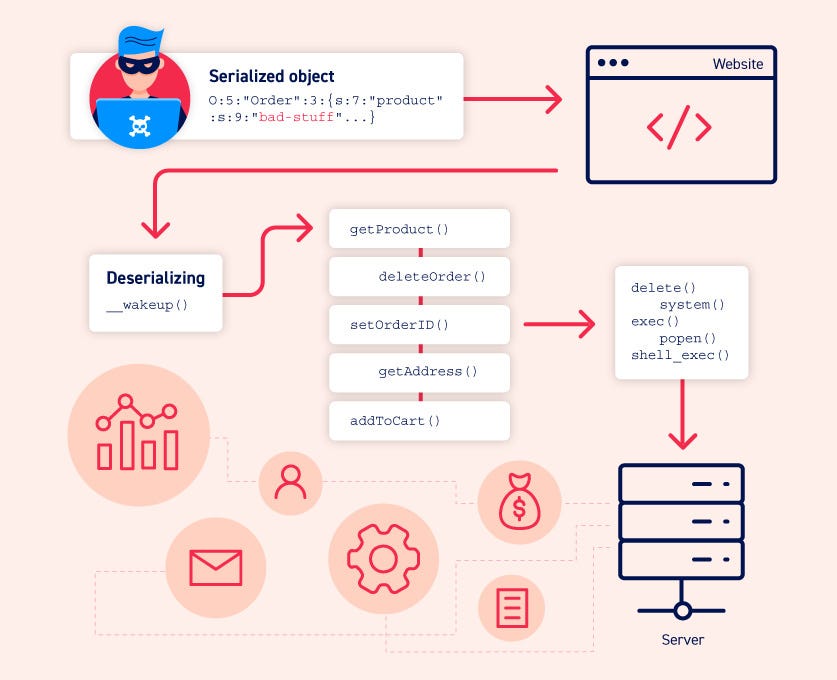
Deserialization is the process of converting a stream of bytes back into a data structure that a program can then use. Insecure Deserialization occurs when a web app deserializes untrusted data.
For example, a web application may allow users to upload a file containing serialized Java objects as input. The web application then deserializes the objects and processes them.
An attacker can craft a malicious file, which, when deserialized, will execute malware. This will allow an attacker to perform various types of attacks, such as remote code execution and privilege escalation.
To prevent Insecure Deserialization attacks, double-check all inputs from the user. Limit the amount of code that runs with high privileges and ensure that you encrypt all sensitive data.
Using Components with Known Vulnerabilities

When you plan to use a piece of software, check for known vulnerabilities. There are many public databases like exploitdb that will help you look for issues with third-party software.
These databases contain publicly disclosed vulnerabilities for various software and applications. Failing to do this will leave your application open to attacks. An attacker will do the research for you and use these vulnerabilities to gain access to your system.
For example, your application may use a third-party library to handle file uploads, but that library might have a known vulnerability. This will leave the application open to attack, even if the rest of the application is secure.
Make sure you do your research before using any third-party software for your business.
Summary
To summarize, OWASP’s Top 10 vulnerabilities is a vital checklist. It helps us to keep our web applications and software secure.
As a pen-tester or a bug bounty hunter, you should be aware of these vulnerabilities to stay ahead of attackers.
Always sanitize user input, employ logging, and do your research before using any third-party software.
Hope you found this article insightful. You can find more AI & cybersecurity articles / videos on my website.

